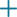Add a RADIUS External Authentication Object for Security Cloud Control
Add a RADIUS server to support external users for device management.
Procedure
Step 1 | Choose System ( | ||||
Step 2 | Click External Authentication. | ||||
Step 3 | Click Add icon ( | ||||
Step 4 | Set the Authentication Method to RADIUS. | ||||
Step 5 | Enter a Name and optional Description. | ||||
Step 6 | Check the RADIUS Server-Enabled Message Authenticator check box to require the Message-Authenticator attribute in all RADIUS responses, ensuring that every response from the RADIUS server is securely verified by the Threat Defense. This feature is enabled by default for new RADIUS servers. We recommend you enable it for existing servers after the upgrade. Disabling message authenticators may expose your firewalls to potential attacks. Ensure that your RADIUS server has the Message-Authenticator configuration. | ||||
Step 7 | For the Primary Server, enter a Host Name/IP Address. | ||||
Step 8 | (Optional) Change the Port from the default. | ||||
Step 9 | Enter the RADIUS Secret Key. | ||||
Step 10 | (Optional) Enter the Backup Server parameters. | ||||
Step 11 | (Optional) Enter RADIUS-Specific Parameters. If you change a user's role, you must save/deploy the changed external authentication object and also remove the user from the Users screen. The user will be re-added automatically the next time they log in. | ||||
Step 12 | (Optional) Define Custom RADIUS Attributes. If your RADIUS server returns values for attributes not included in the When you create a RADIUS authentication object, a new dictionary file for that object is created on the device in the Example:If a RADIUS server is used on a network with a Cisco router, you might want to use the To declare that custom attribute, you create a custom attribute with an attribute name of You could then enter | ||||
Step 13 | (Optional) In the CLI Access Filter area Administrator CLI Access User List field, enter the user names that should have CLI access, separated by commas. Make sure that these usernames match usernames on the RADIUS server. The names must be Linux-valid usernames:
To prevent RADIUS authentication of CLI access, leave the field blank.
| ||||
Step 14 | (Optional) Click Test to test management center connectivity to the RADIUS server. | ||||
Step 15 | (Optional) You can also enter Additional Test Parameters to test user credentials for a user who should be able to authenticate: enter a User Name and Password, and then click Test.
Example:To test if you can retrieve the | ||||
Step 16 | Click Save. |
Examples
Simple User Role Assignments
The following figure illustrates a sample RADIUS login authentication object for a server running Cisco Identity Services Engine (ISE) with an IP address of 10.10.10.98 on port 1812. No backup server is defined.
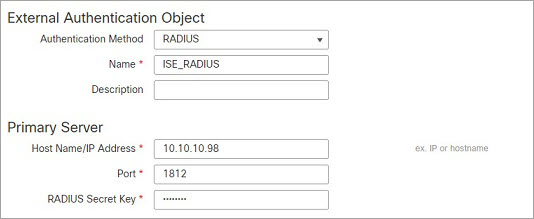
The following example shows RADIUS-specific parameters, including the timeout (30 seconds) and number of failed retries before the Secure Firewall System attempts to contact the backup server, if any.
This example illustrates important aspects of RADIUS user role configuration:
Users ewharton and gsand are granted web interface Administrative access.
The user cbronte is granted web interface Maintenance User access.
The user jausten is granted web interface Security Analyst access.
The user ewharton can
log into the device using a CLI account.
The following graphic depicts the role configuration for the example:
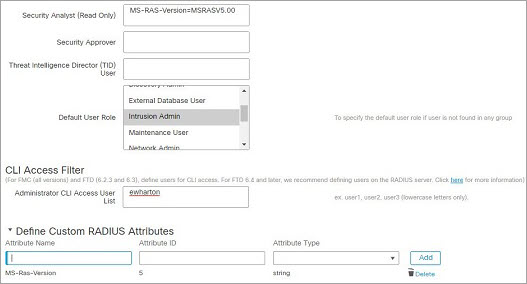
Roles for Users Matching an Attribute-Value Pair
You can use an attribute-value pair to identify users who should receive a particular user role. If the attribute you use is a custom attribute, you must define the custom attribute.
The following figure illustrates the role configuration and custom attribute definition in a sample RADIUS login authentication object for the same ISE server as in the previous example.
In this example, however, the MS-RAS-Version custom attribute is returned for one or more of the users because a Microsoft remote access server is in use. Note the MS-RAS-Version custom attribute is a string. In this example, all users logging in to RADIUS through a Microsoft v. 5.00 remote access server should receive the Security Analyst (Read Only) role, so you enter the attribute-value pair of MS-RAS-Version=MSRASV5.00 in the Security Analyst (Read Only) field.