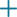Add an LDAP External Authentication Object for the Security Cloud Control
Add an LDAP server to support external users for device management.
Before you begin
-
You must specify DNS server(s) for domain name lookup on your device. Even if you specify an IP address and not a hostname for the LDAP server on this procedure, the LDAP server may return a URI for authentication that can include a hostname. A DNS lookup is required to resolve the hostname.
-
If you are configuring an LDAP authentication object for use with CAC authentication, do not remove the CAC inserted in your computer. You must have a CAC inserted at all times after enabling user certificates.
Procedure
Step 1 | Choose System ( | ||||
Step 2 | Click the External Authentication tab. | ||||
Step 3 | Click Add icon ( | ||||
Step 4 | Set the Authentication Method to LDAP. | ||||
Step 5 | Enter a Name and optional Description. | ||||
Step 6 | Choose a Server Type from the drop-down list.
| ||||
Step 7 | For the Primary Server, enter a Host Name/IP Address. If you are using a certificate to connect via TLS or SSL, the host name in the certificate must match the host name used in this field. In addition, IPv6 addresses are not supported for encrypted connections. | ||||
Step 8 | (Optional) Change the Port from the default. | ||||
Step 9 | (Optional) Enter the Backup Server parameters. | ||||
Step 10 | Enter LDAP-Specific Parameters. | ||||
Step 11 | Configure Attribute Mapping to retrieve users based on an attribute.
| ||||
Step 12 | (Optional) Configure Group Controlled Access Roles. If you do not configure a user’s privileges using group-controlled access roles, a user has only the privileges granted by default in the external authentication policy. | ||||
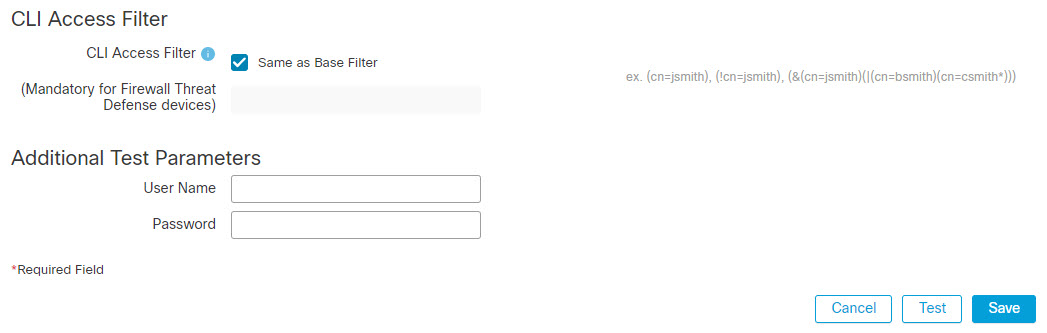
Step 13 | (Optional) Set the CLI Access Filter to allow CLI users. To prevent LDAP authentication of CLI access, leave this field blank. To specify CLI users, choose one of the following methods:
The usernames must be Linux-valid:
| ||||
Step 14 | (Optional) Click Test to test connectivity to the LDAP server. The test output lists valid and invalid user names. Valid user names are
unique, and can include underscores ( | ||||
Step 15 | (Optional) You can also enter Additional Test Parameters to test user credentials for a user who should be able to authenticate: enter a User Name
If you are connecting to a Microsoft Active Directory Server and supplied a UI access attribute in place of
Example:To test if you can retrieve the | ||||
Step 16 | Click Save. |
Examples
Basic Example
The following figures illustrate a basic configuration of an LDAP login authentication object for a Microsoft Active Directory Server. The LDAP server in this example has an IP address of 10.11.3.4. The connection uses port 389 for access.
This example shows a connection using a base distinguished name of OU=security,DC=it,DC=example,DC=com for the security organization in the information technology domain of the Example company.
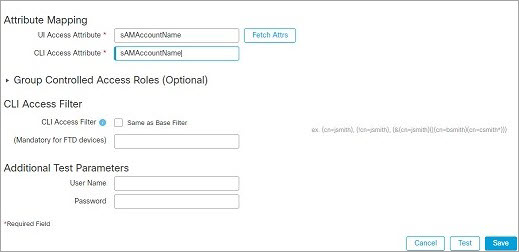
However, because this server is a Microsoft Active Directory server, it uses the sAMAccountName attribute to store user names rather than the uid attribute. Choosing the MS Active Directory server type and clicking Set Defaults sets the UI Access Attribute to sAMAccountName. As a result, the system checks the sAMAccountName attribute for each object for matching user names when a user attempts to log into the system.
In addition, a CLI Access Attribute of sAMAccountName causes each sAMAccountName attribute to be checked for all objects in the directory for matches when a user logs into a CLI account on the appliance.
Note that because no base filter is applied to this server, the system checks attributes for all objects in the directory indicated by the base distinguished name. Connections to the server time out after the default time period (or the timeout period set on the LDAP server).
Advanced Example
This example illustrates an advanced configuration of an LDAP login authentication object for a Microsoft Active Directory Server. The LDAP server in this example has an IP address of 10.11.3.4. The connection uses port 636 for access.
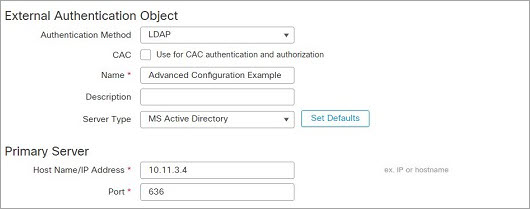
This example shows a connection using a base distinguished name of OU=security,DC=it,DC=example,DC=com for the security organization in the information technology domain of the Example company. However, note that this server has a base filter of (cn=*smith). The filter restricts the users retrieved from the server to those with a common name ending in smith.
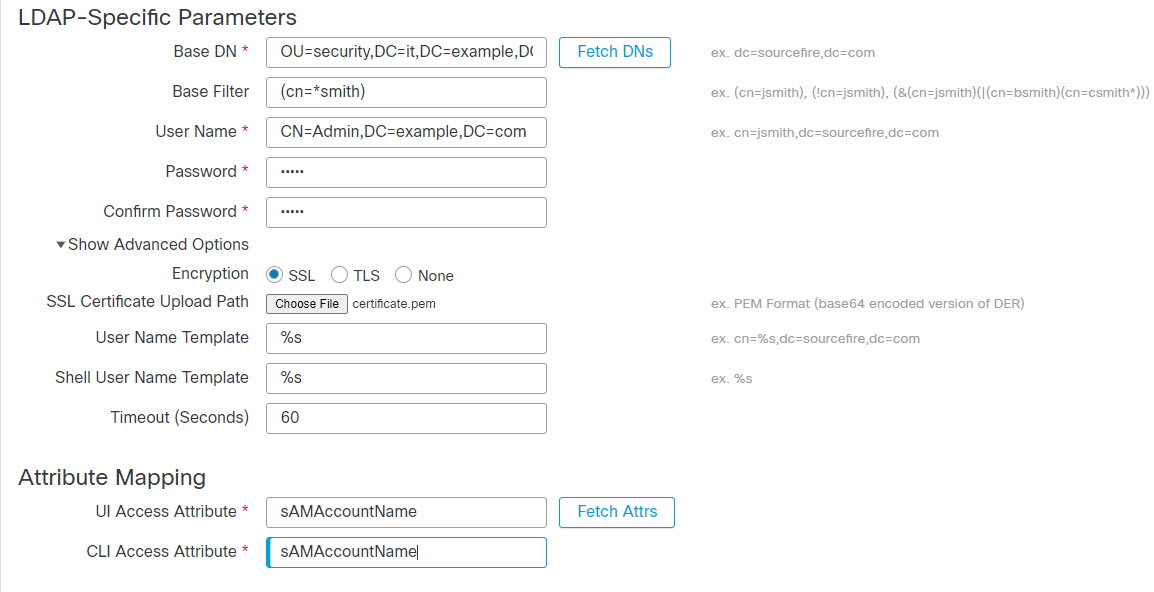
The connection to the server is encrypted using SSL and a certificate named certificate.pem is used for the connection. In addition, connections to the server time out after 60 seconds because of the Timeout (Seconds) setting.
Because this server is a Microsoft Active Directory server, it uses the sAMAccountName attribute to store user names rather than the uid attribute. Note that the configuration includes a UI Access Attribute of sAMAccountName. As a result, the system checks the sAMAccountName attribute for each object for matching user names when a user attempts to log into the system.
In addition, a CLI Access Attribute of sAMAccountName causes each sAMAccountName attribute to be checked for all objects in the directory for matches when a user logs into a CLI account on the appliance.
This example also has group settings in place. The Maintenance User role is automatically assigned to all members of the group with a member group attribute and the base domain name of CN=SFmaintenance,DC=it,DC=example,DC=com.
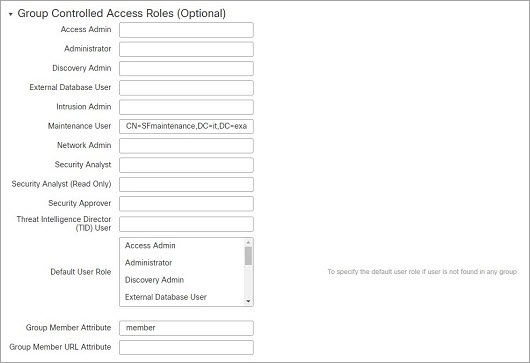
The CLI Access Filter is set to be the same as the base filter, so the same users can access the appliance through the CLI as through the web interface.