Matching Traffic on Certificate Status
Before you begin
-
Add a trusted CA object or group to your SSL policy. See Trusting external certificate authorities for more information.
Procedure
Step 1 | In the Firewall Management Center, click . |
Step 2 | Add a new policy or edit an existing policy. |
Step 3 | Add a new TLS/SSL rule or edit an existing rule. |
Step 4 | In the Add Rule or Editing Rule dialog box, choose Cert Status. |
Step 5 | For each certificate status, you have the following options:
|
Step 6 | Add or continue editing the rule. |
Example
The organization trusts the Verified Authority certificate authority. The organization does not trust the Spammer Authority certificate authority. The system administrator uploads the Verified Authority certificate and an intermediate CA certificate issued by Verified Authority to the system. Because Verified Authority revoked a certificate it previously issued, the system administrator uploads the CRL that Verified Authority provided.
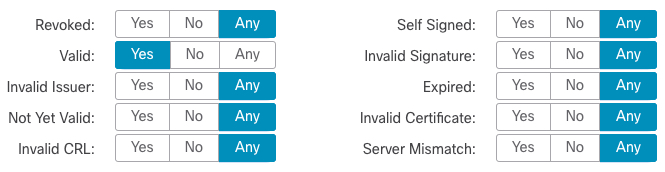
The following figure shows a certificate status rule condition checking for valid certificates, those issued by a Verified Authority, are not on the CRL, and still within the Valid From and Valid To date. Because of the configuration, traffic encrypted with these certificates is not decrypted and inspected with access control.
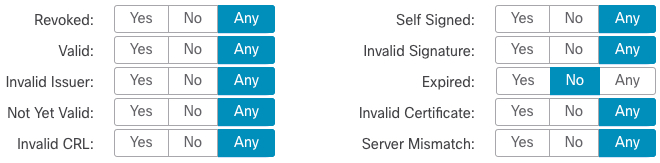
The following figure shows a certificate status rule condition checking for the absence of a status. In this case, because of the configuration, it matches against traffic encrypted with a certificate that has not expired and monitors that traffic.
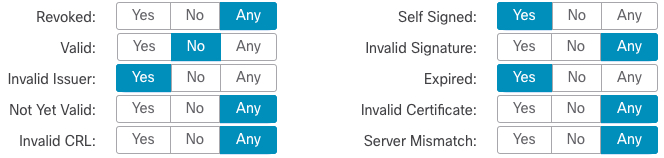
The following graphic illustrates a certificate status rule condition that matches on the presence or absence of several statuses. Because of the configuration, if the rule matches incoming traffic encrypted with a certificate issued by an invalid user, self-signed, invalid, or expired, it decrypts the traffic with a known key.
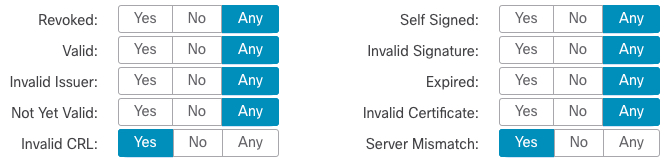
The following graphic illustrates a certificate status rule condition that matches if the SNI of the request matches the server name or if the CRL is not valid. Because of the configuration, if the rule matches either condition, traffic is blocked.
What to do next
-
Deploy configuration changes.