Identity deployments
When the system detects user data from a user login, from any identity source, the user from the login is checked against the list of users in the Security Cloud Control user database. If the login user matches an existing user, the data from the login is assigned to the user. Logins that do not match existing users cause a new user to be created, unless the login is in SMTP traffic. Non-matching logins in SMTP traffic are discarded.
The group to which the user belongs is associated with the user as soon as the user is seen by the Security Cloud Control.
Sample identity deployments
The sample deployments discussed in this section are based on the system shown in the following figure.
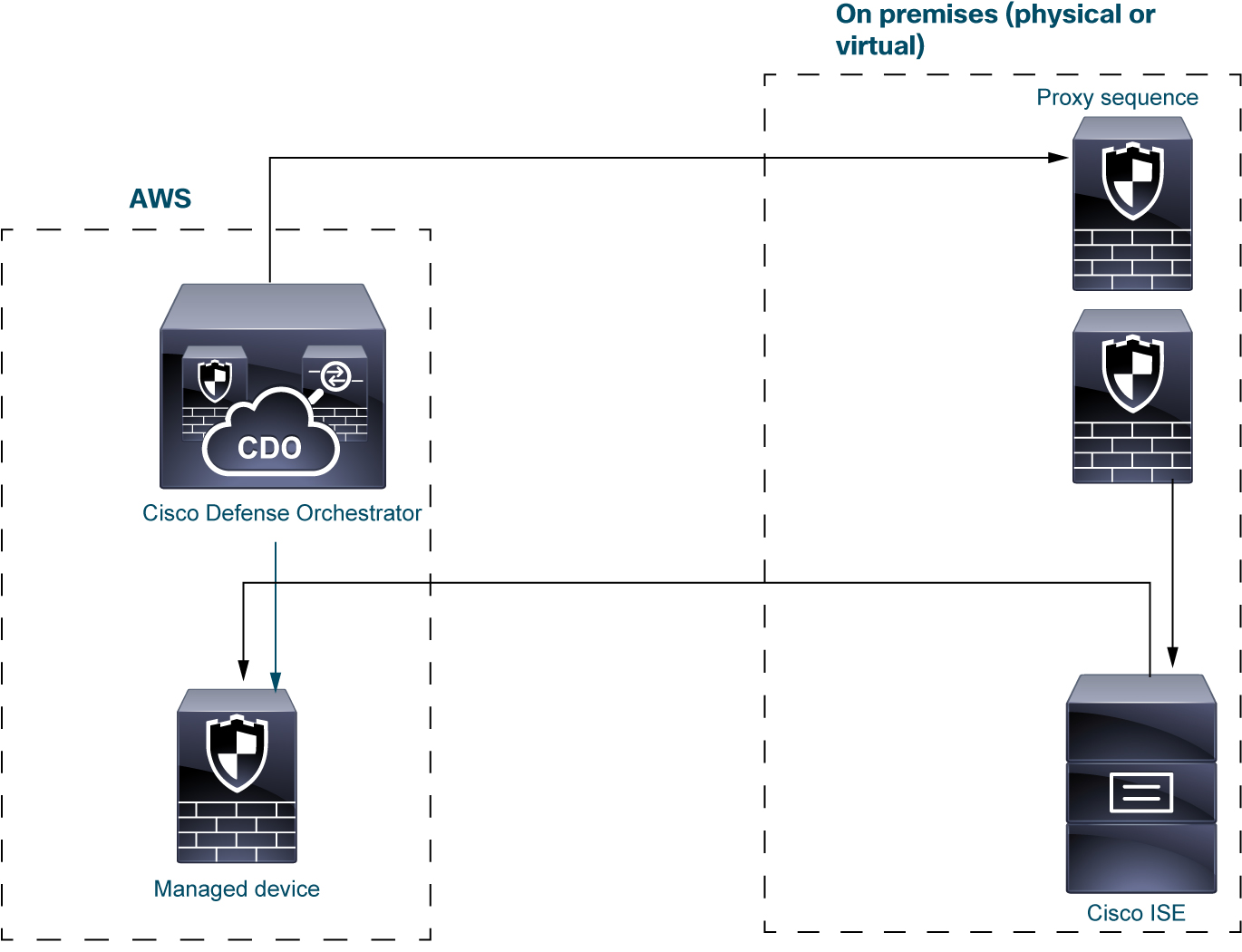
In the preceding figure, Security Cloud Control and one managed device are deployed to AWS and the other devices are located on premises. These devices can be either physical or virtual; they just need to be able to communicate with each other.
The two on-premises managed devices are intended to be used as a proxy sequence. You must add those devices to Security Cloud Control as well.
A proxy sequence is one or more managed devices that can be used to communicate with an LDAP, Active Directory, or ISE/ISE-PIC server. It is necessary only if Security Cloud Control cannot communicate with your Active Directory or ISE/ISE-PIC server. (For example, Security Cloud Control might be in a public cloud but Active Directory or ISE/ISE-PIC might be in a private cloud.)
LDAP or Active Directory are needed only for TS Agent and captive portal, as the following paragraphs explain.
For more information about setting up a system like this, see How to set up an identity policy.
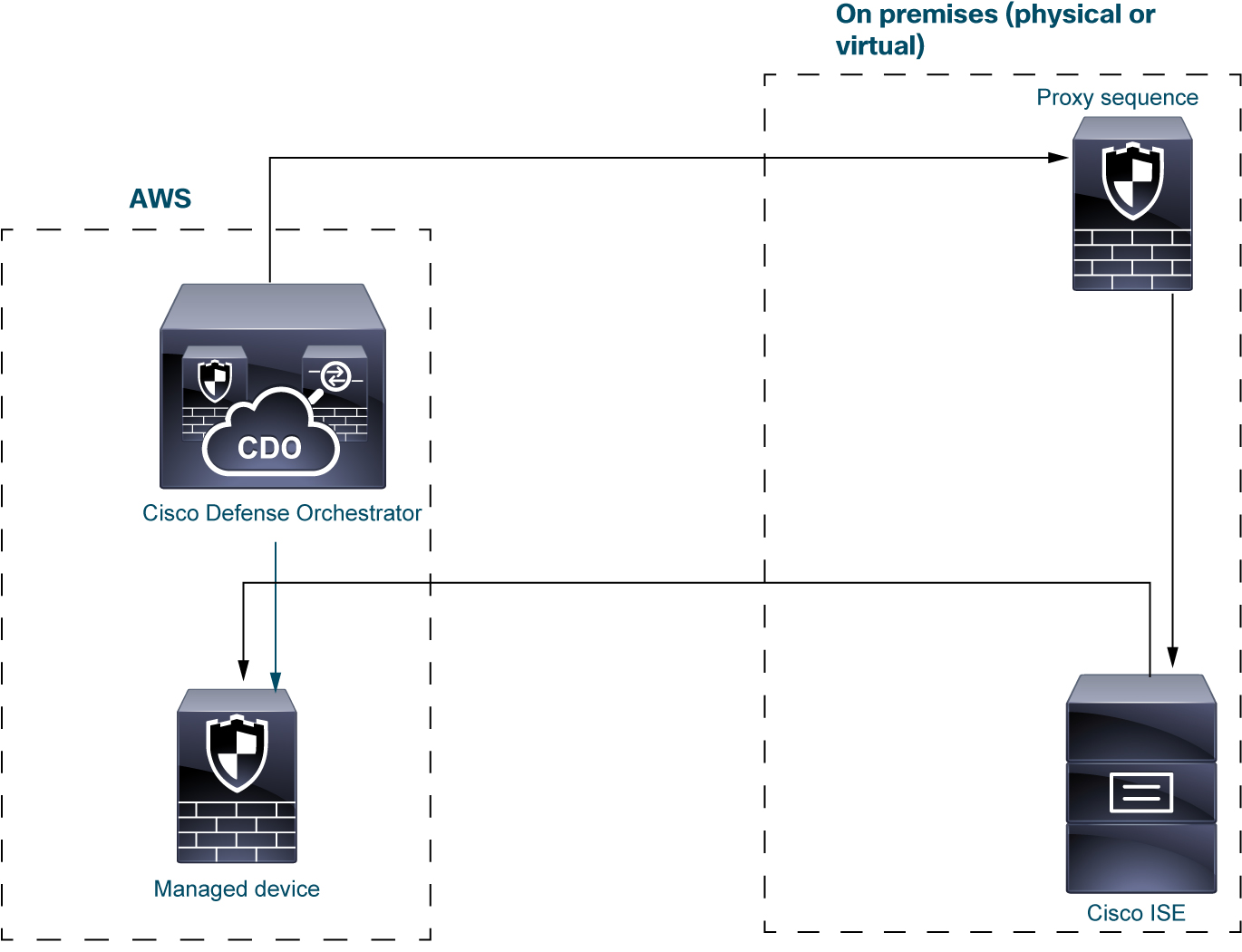
ISE/ISE-PIC identity source
When you deploy the ISE/ISE-PIC identity source, Security Cloud Control contacts the proxy sequence if Security Cloud Control cannot contact the ISE/ISE-PIC server directly. Users, groups, and subscriptions are sent from the ISE/ISE-PIC server to the managed device in AWS.
You can optionally have an LDAP server in an ISE/ISE-PIC deployment but because it's optional, it isn't shown in the following figure.
For more information about ISE/ISE-PIC, see The ISE/ISE-PIC identity source.
Passive identity agent identity source
Software that monitors one or several Microsoft AD domain controllers, sending user name and IP address information to the Security Cloud Control.
For more information, see The passive identity agent identity source.
pxGrid Cloud Identity Source
The Cisco Identity Services Engine (Cisco ISE) pxGrid Cloud identity source enables you to use subscription and user data from Cisco ISE in Cloud-Delivered Firewall Management Center access control rules. Also, the identity source uses constantly changing dynamic objects from Cisco ISE in access control policies in the Cloud-Delivered Firewall Management Center.
For more information, see About the pxGrid Cloud identity source.
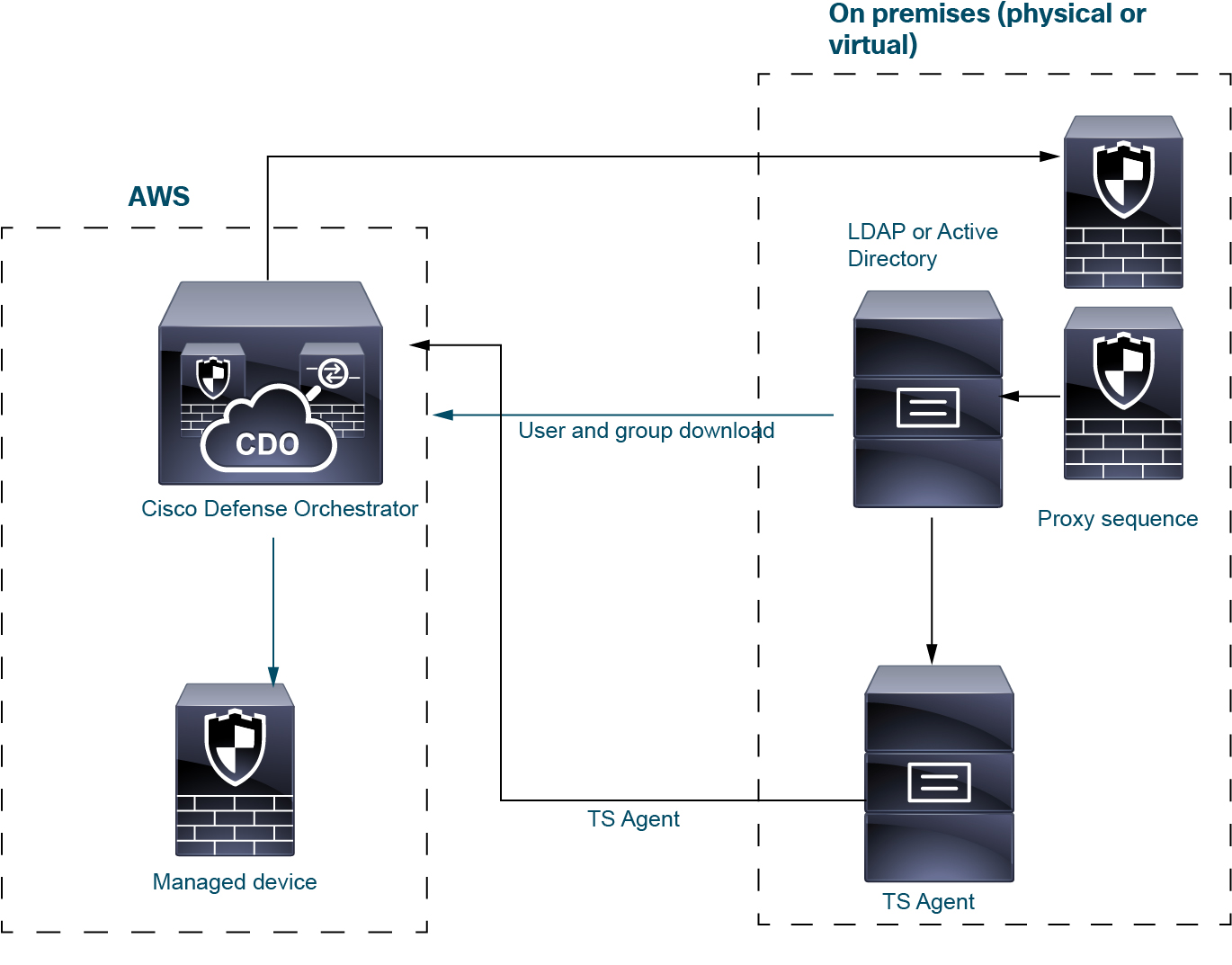
TS Agent identity source
The Terminal Services (TS) Agent software runs on a Microsoft Server and sends Security Cloud Control user information based on the port range the users log in to the server with. TS Agent gets user identity information from LDAP or Active Directory and sends it to Security Cloud Control.
For more information about the TS Agent identity source, see The Terminal Services (TS) Agent identity source.
Captive portal
You can use captive portal active authentication with any of the following:
-
LDAP
For more information, see The captive portal identity source.
-
Microsoft AD
For more information, see The captive portal identity source.
-
Microsoft Azure AD (SAML)
For more information, see Create a Microsoft Azure AD (SAML) realm.