Router Between VXLAN Domains
With a VXLAN-stretched Layer 2 domain, a VM can point to an Firewall Threat Defense as its gateway while the Firewall Threat Defense is not on the same rack, or even when the Firewall Threat Defense is far away over the Layer 3 network.
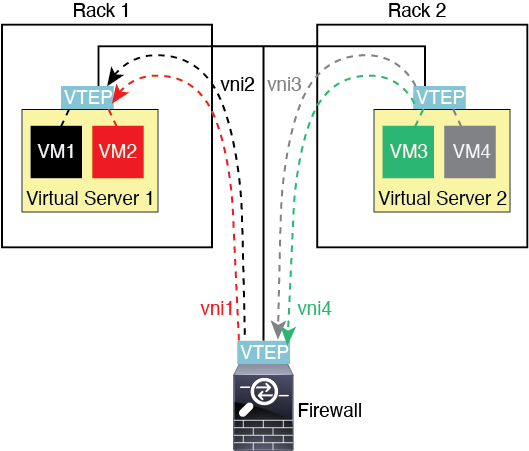
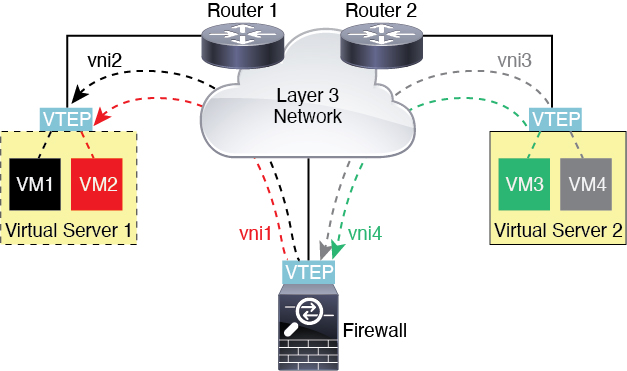
See the following notes about this scenario:
-
For packets from VM3 to VM1, the destination MAC address is the Firewall Threat Defense MAC address, because the Firewall Threat Defense is the default gateway.
-
The VTEP source interface on Virtual Server 2 receives packets from VM3, then encapsulates the packets with VNI 3’s VXLAN tag and sends them to the Firewall Threat Defense.
-
When the Firewall Threat Defense receives the packets, it decapsulates the packets to get the inner frames.
-
The Firewall Threat Defense uses the inner frames for route lookup, then finds that the destination is on VNI 2. If it does not already have a mapping for VM1, the Firewall Threat Defense sends an encapsulated ARP broadcast on the multicast group IP on VNI 2.
NoteThe Firewall Threat Defense must use dynamic VTEP peer discovery because it has multiple VTEP peers in this scenario.
-
The Firewall Threat Defense encapsulates the packets again with the VXLAN tag for VNI 2 and sends the packets to Virtual Server 1. Before encapsulation, the Firewall Threat Defense changes the inner frame destination MAC address to be the MAC of VM1 (multicast-encapsulated ARP might be needed for the Firewall Threat Defense to learn the VM1 MAC address).
-
When Virtual Server 1 receives the VXLAN packets, it decapsulates the packets and delivers the inner frames to VM1.