Distinguished Name (DN) rule conditions
This topic discusses how to use distinguished name conditions in a decryption rule. If you're not sure, you can find a certificate's Subject Alternative Name (SAN) and Common Name using a web browser, then you can add those values to a decryption rule as distinguished name conditions.
For detailed information about SANs, see RFC 528, section 4.2.1.6.
The following sections discuss:
DN rule matching example
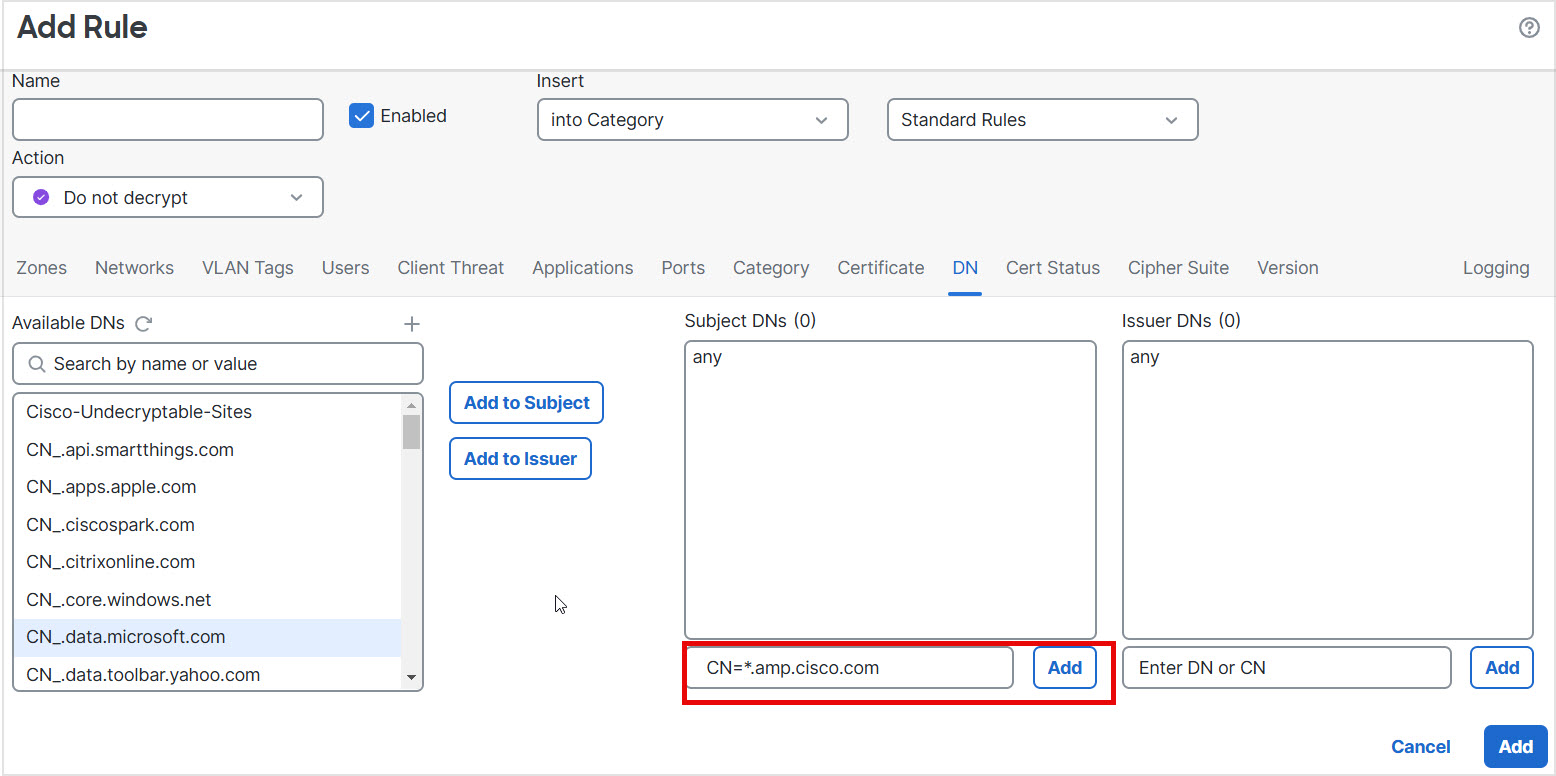
Following is an example of DN rule conditions in a Do Not Decrypt rule. Suppose you want to make sure to not decrypt traffic going to amp.cisco.com or to YouTube. You could set up your DN conditions as follows:
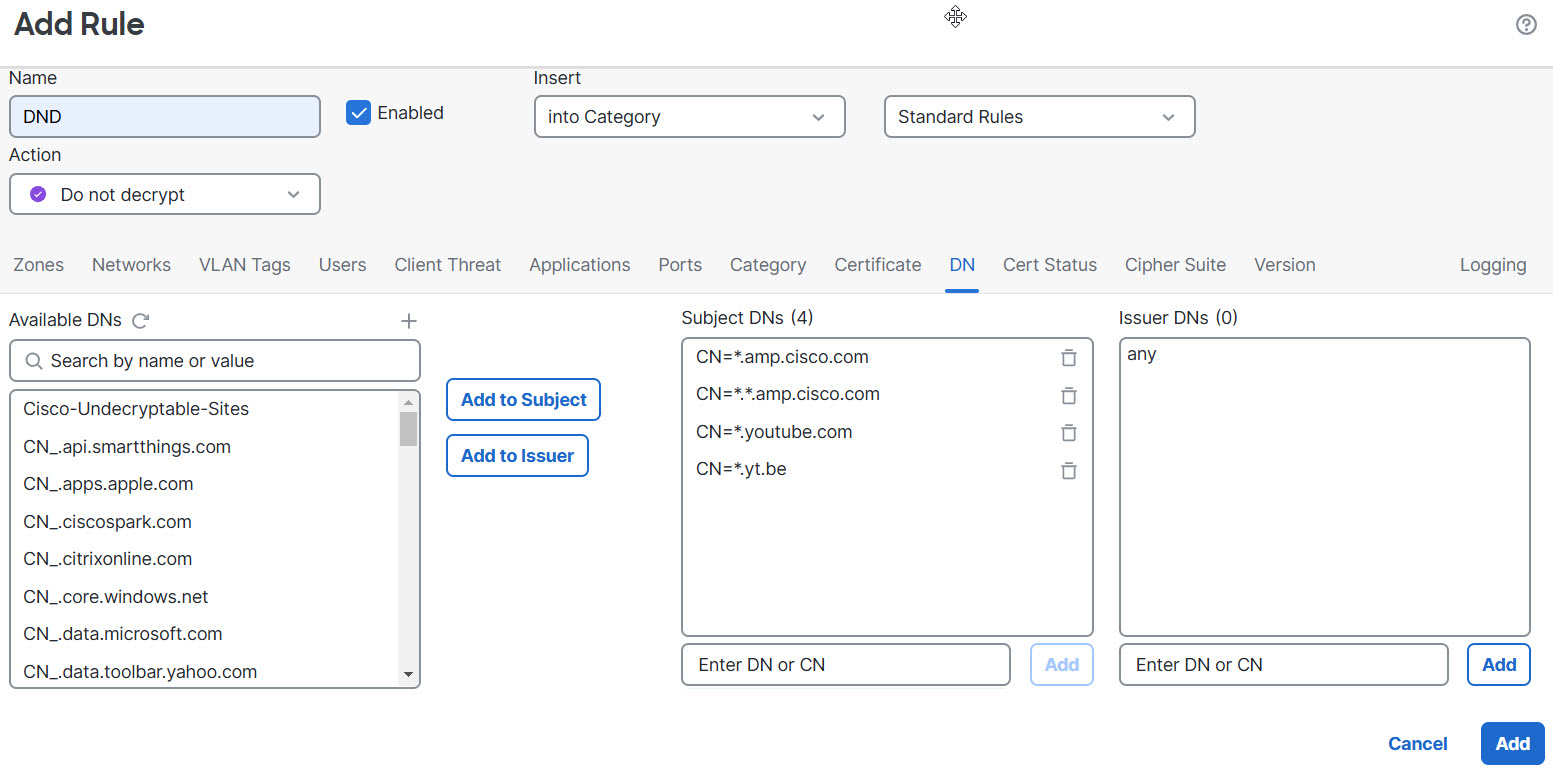
The preceding DN rule conditions would match the following URLs and therefore, the traffic would be undecrypted an earlier rule prevented it:
-
www.amp.cisco.com
-
auth.amp.cisco.com
-
auth.us.amp.cisco.com
-
www.youtube.com
-
kids.youtube.com
-
www.yt.be
The preceding DN rule conditions would not match any of the following URLs and therefore, the traffic would not match the Do Not Decrypt rule but might match any other decryption rules in the same decryption policy.
-
amp.cisco.com
-
youtube.com
-
yt.be
To match any of the preceding host names, add more CNs to the rule (for example, adding CN=yt.be would match that URL.)
How the system uses the SNI and SANs
The host name portion of the URL in the client request is the Server Name Indication (SNI). The client specifies which hostname they want to connect to (for example, auth.amp.cisco.com) using the SNI extension in the TLS handshake. The server then selects the corresponding private key and certificate chain that are required to establish the connection while hosting all certificates on a single IP address.
If there's a match between the SNI and the CN or a SAN in the certificate, we use the SNI when comparing against the DNs listed in the rule. If there is no SNI or if it doesn't match the certificate, we use the certificate's CN when comparing against the DNs listed in the rule.
How to find a certificate's Common Name and subject alternative names
To find any certificate's Common Name, use the following steps. You can even use these steps to find the common name and SANs for a self-signed certificate.
These steps are for Firefox but other browsers are similar. The following procedure uses amp.cisco.com as an example.
-
Browse to
amp.cisco.comin Firefox. -
In the browser's location bar, to the left of the URL, click
 .
. -
Click .
(For a non-secure or self-signed certificate, click .)
-
On the Page Info dialog box, click View Certificate.
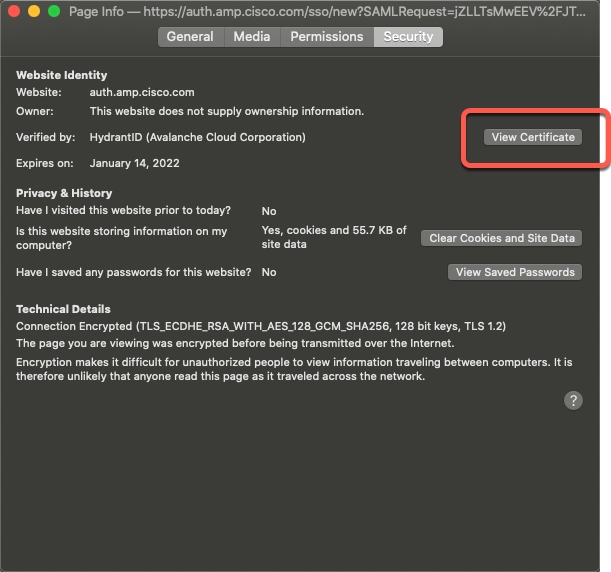
-
The next page shows certificate details.
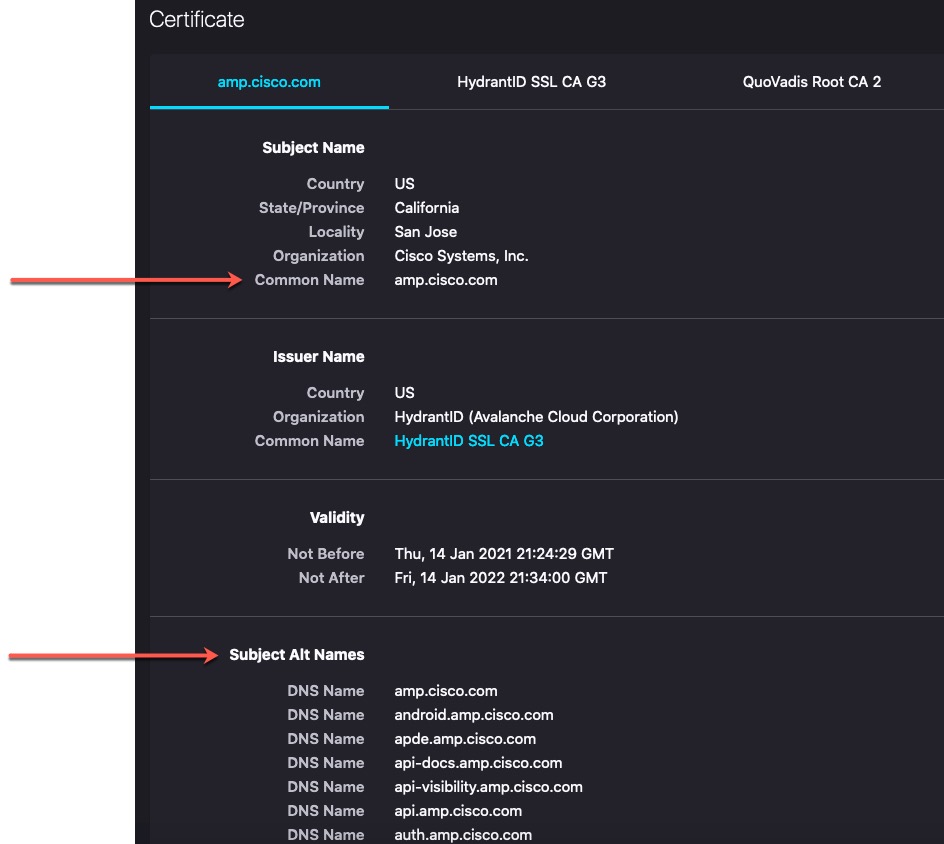
Note the following:
-
CN=auth.amp.cisco.com, if used as a DN rule condition, would match only that host name (that is, SNI). The SNIamp.cisco.comwould not match. -
To match as many domain name fields as possible, use wildcards.
For example, to match
auth.amp.cisco.com, useCN=*.amp.cisco.com. To matchauth.us.amp.cisco.com, useCN=*.*.amp.cisco.com.A DN like
CN=*.example.commatcheswww.example.combut notexample.com. To match both SNIs, use two DNs in the rule condition. -
Don't go overboard with wildcards though. For example, a DN object like
CN=*.google.commatches a very large number of SANs. Instead ofCN=*.google.com, use a DN object likeCN=*.youtube.comas the DN object so it matches names likewww.youtube.com.You can also use variations of the SNI that match SANs like
CN=*.youtube.com,CN=youtu.be,CN=*.yt.be, and so on. -
A self-signed certificate should work the same way. You can confirm it's a self-signed certificate by the fact the issuer DN is the same as the subject DN.
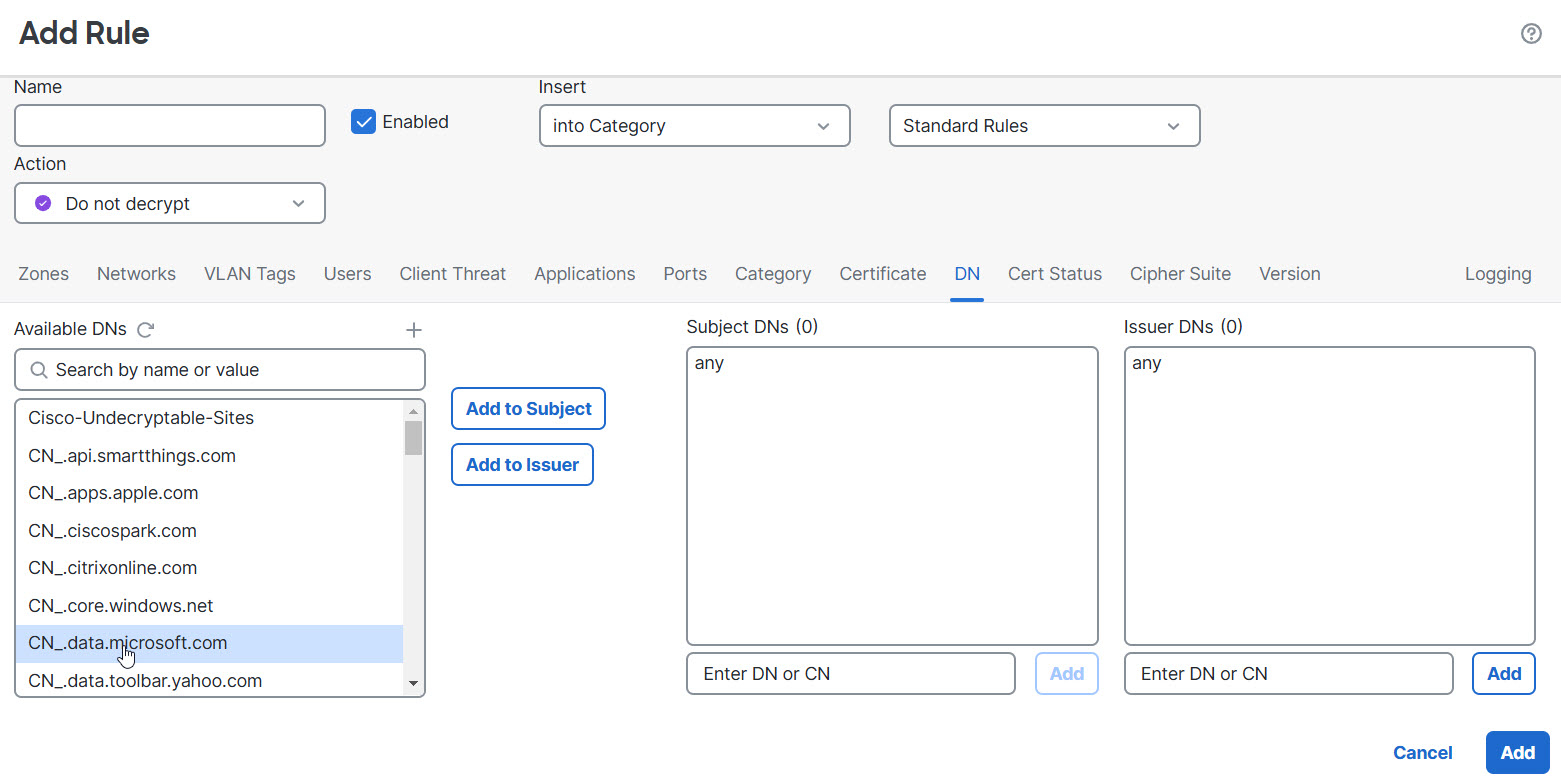
How to add a DN rule condition
After you know the CN you want to match, edit the decryption rule in one of the following ways:
-
Use an existing DN.
Click the name of a DN and then click either Add to Subject or Add to Issuer. (Add to Subject is much more common.) To view the value of a DN object, hover the mouse pointer over it.)
-
Create a new DN object.
Click Add (
 ) to the right of Available DNs. The DN object must consist of a name and a value.
) to the right of Available DNs. The DN object must consist of a name and a value. -
Add the DN directly.
Enter the DN in the field at the bottom of the Subject DNs field or the Issuer DNs field. (Subject DNs is more common.) After you enter the DN, click Add.