Guidelines for using TLS/SSL decryption
General guideline
rule-based decryption rules require processing overhead that can impact performance. Determine which traffic must be decrypted and subjected to deep inspection before you set up any policies or rules.
You cannot decrypt traffic on a device that uses any of the following:
-
Passive interface
-
Inline or inline tap interface
-
TCP state bypass
Guidelines for undecryptable traffic
We can determine that certain traffic is not decryptable either because the website itself is not decryptable or because the website uses TLS/SSL pinning, which effectively prevents users from accessing a decrypted site without errors in their browser.
For more information about certificate pinning, see About TLS/SSL pinning.
We maintain the list of these sites as follows:
-
A Distinguished Name (DN) group named Cisco-Undecryptable-Sites
-
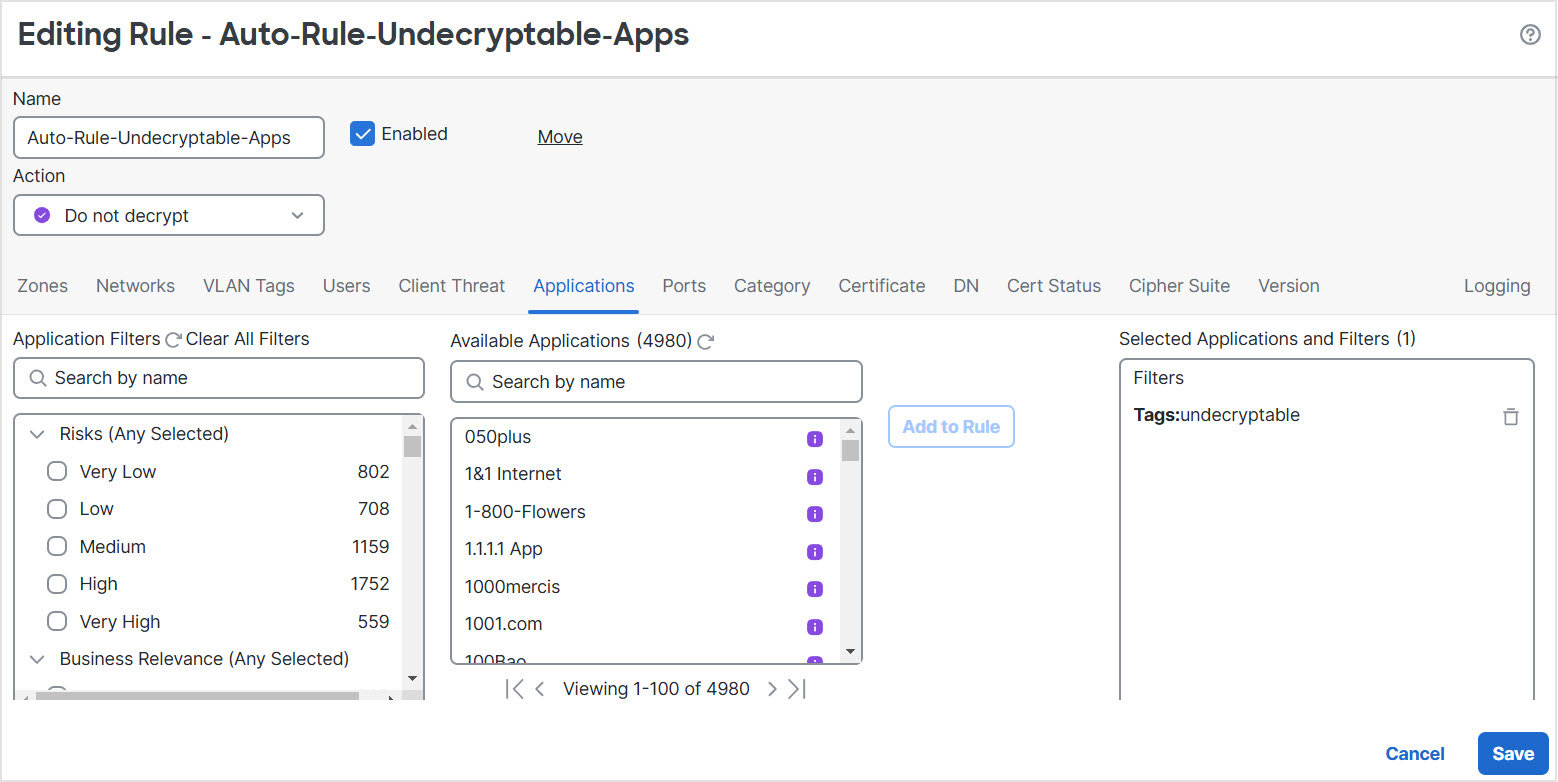
The pinned certificate or undecryptable application filter
If you are decrypting traffic and you do not want users to see errors in their browsers when going to these sites, we recommend you set up a Do Not Decrypt rule toward the bottom of your decryption rules.
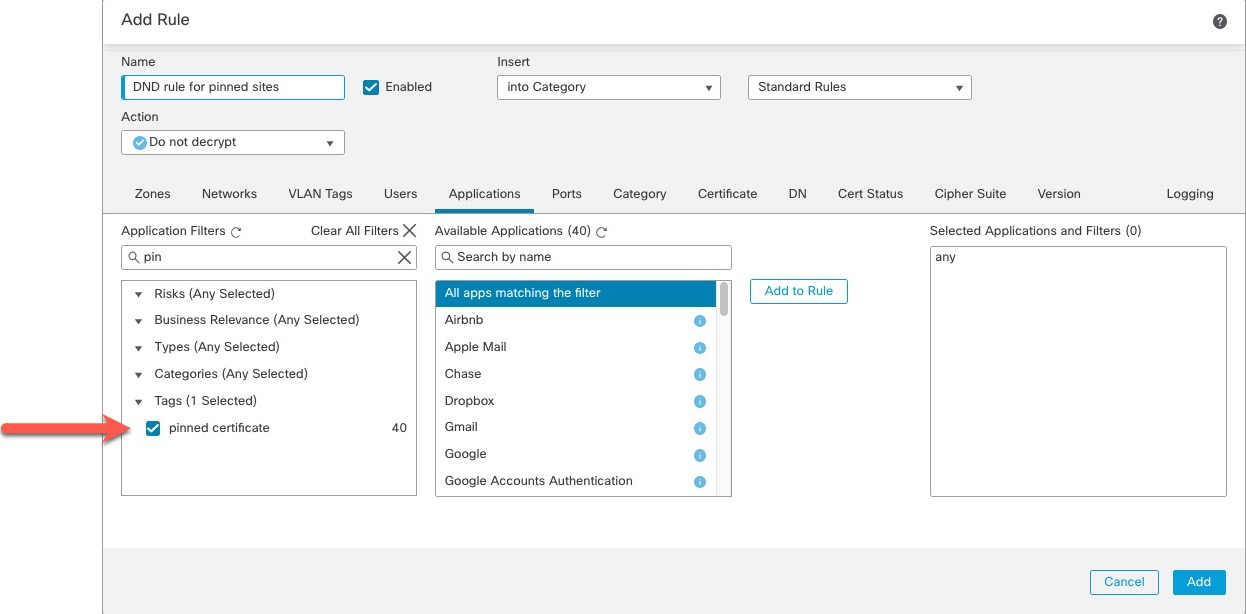
If you use the decryption policy wizard to create a policy for outbound traffic protection, a Do Not Decrypt rule for pinned certificates is created for you as the following example shows.
An example of setting up a pinned certificate application filter follows.