Add a Standalone Firewall Threat Defense
Standalone logical devices work either alone or in a High Availability pair. On the Firepower 9300 with multiple security modules, you can deploy either a cluster or standalone devices. The cluster must use all modules, so you cannot mix and match a 2-module cluster plus a single standalone device, for example.
Before you begin
-
Download the application image you want to use for the logical device from Cisco.com, and then upload that image to the Firepower 4100/9300 chassis.
NoteFor the Firepower 9300, you can install different application types (ASA and Firewall Threat Defense) on separate modules in the chassis. You can also run different versions of an application instance type on separate modules.
-
Configure a management interface to use with the logical device. The management interface is required. Note that this management interface is not the same as the chassis management port that is used only for chassis management (and that appears at the top of the Interfaces tab as MGMT).
-
You can later enable management from a data interface; but you must assign a Management interface to the logical device even if you don't intend to use it after you enable data management. See the configure network management-data-interface command in the FTD command reference for more information.
-
You must also configure at least one Data type interface. Optionally, you can also create a firepower-eventing interface to carry all event traffic (such as web events). See Interface Types for more information.
-
Gather the following information:
-
Interface IDs for this device
-
Management interface IP address and network mask
-
Gateway IP address
-
Firewall Management Center IP address and/or NAT ID of your choosing
-
DNS server IP address
-
Firewall Threat Defense hostname and domain name
-
Procedure
Step 1 | Choose Logical Devices. |
Step 2 | Click , and set the following parameters: 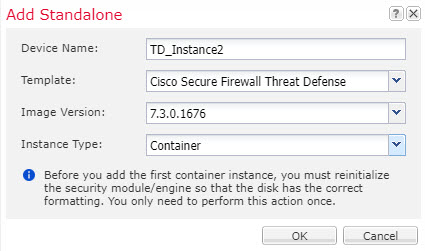 |
Step 3 | Expand the Data Ports area, and click each interface that you want to assign to the device. You can only assign data interfaces that you previously enabled on the Interfaces page. You will later enable and configure these interfaces in Firewall Management Center, including setting the IP addresses. Hardware Bypass-capable ports are shown with the following icon: |
Step 4 | Click the device icon in the center of the screen. A dialog box appears where you can configure initial bootstrap settings. These settings are meant for initial deployment only, or for disaster recovery. For normal operation, you can later change most values in the application CLI configuration. |
Step 5 | On the General Information page, complete the following: |
Step 6 | On the Settings tab, complete the following: 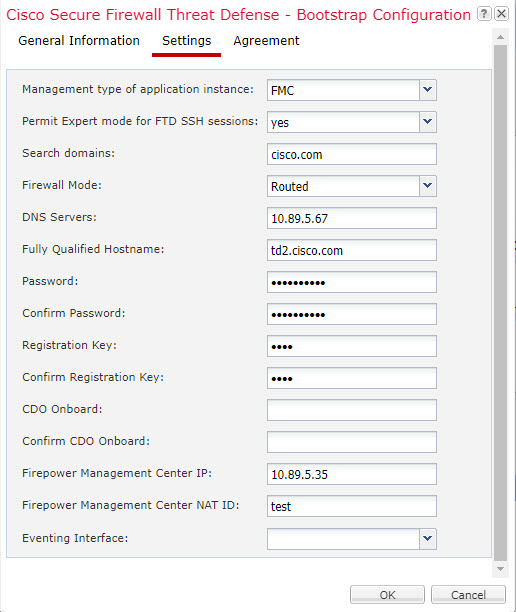
|
Step 7 | On the Agreement tab, read and accept the end user license agreement (EULA). |
Step 8 | Click OK to close the configuration dialog box. |
Step 9 | Click Save. The chassis deploys the logical device by downloading the specified software version and pushing the bootstrap configuration and management interface settings to the application instance. Check the Logical Devices page for the status of the new logical device. When the logical device shows its Status as online, you can start configuring the security policy in the application. 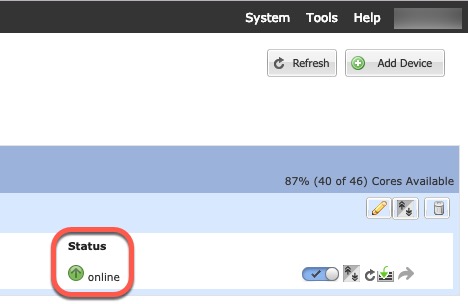 |
Step 10 | See the Firewall Management Center configuration guide to add the Firewall Threat Defense as a managed device and start configuring your security policy. |