Configure Dynamic DNS
When an interface uses DHCP IP addressing, the assigned IP address can change when the DHCP lease is renewed. When the interface needs to be reachable using a fully qualified domain name (FQDN), the IP address change can cause the DNS server resource records (RRs) to become stale. Dynamic DNS (DDNS) provides a mechanism to update DNS RRs whenever the IP address or hostname changes. You can also use DDNS for static or PPPoE IP addressing.
DDNS updates the following RRs on the DNS server: the A RR includes the name-to-IP address mapping, while the PTR RR maps addresses to names.
The Firewall Threat Defense supports the following DDNS update methods:
-
Standard DDNS—The standard DDNS update method is defined by RFC 2136.
With this method, the Firewall Threat Defense and the DHCP server use DNS requests to update the DNS RRs. The Firewall Threat Defense or DHCP server sends a DNS request to its local DNS server for information about the hostname and, based on the response, determines the main DNS server that owns the RRs. The Firewall Threat Defense or DHCP server then sends an update request directly to the main DNS server. See the following typical scenarios.
-
The Firewall Threat Defense updates the A RR, and the DHCP server updates the PTR RR.
Typically, the Firewall Threat Defense "owns" the A RR, while the DHCP server "owns" the PTR RR, so both entities need to request updates separately. When the IP address or hostname changes, the Firewall Threat Defense sends a DHCP request (including the FQDN option) to the DHCP server to inform it that it needs to request a PTR RR update.
-
The DHCP server updates both the A and PTR RR.
Use this scenario if the Firewall Threat Defense does not have the authority to update the A RR. When the IP address or hostname changes, the Firewall Threat Defense sends a DHCP request (including the FQDN option) to the DHCP server to inform it that it needs to request an A and PTR RR update.
You can configure different ownership depending on your security needs and the requirements of the main DNS server. For example, for a static address, the Firewall Threat Defense should own the updates for both records.
-
-
Web—The Web update method uses the DynDNS Remote API specification (https://help.dyn.com/remote-access-api/).
With this method when the IP address or hostname changes, the Firewall Threat Defense sends an HTTP request directly to a DNS provider with which you have an account.
The DDNS page also supports setting DHCP server settings relating to DDNS.
Note | DDNS is not supported on the BVI or bridge group member interfaces. |
Before you begin
-
Configure a DNS server group on , and then enable the group for the interface on , create or edit a Threat Defense policy and click DNS. See DNS.
-
Configure the device hostname. You can configure the hostname when you perform the Firewall Threat Defense initial setup, or by using the configure network hostname command. If you do not specify the hostname per interface, then the device hostname is used.
Procedure
Step 1 | Choose , and edit the Firewall Threat Defense device. | ||
Step 2 | Choose . | ||
Step 3 | Standard DDNS method: Configure a DDNS update method to enable DNS requests from the Firewall Threat Defense. You do not need to configure a DDNS update method if the DHCP server will perform all requests. | ||
Step 4 | Web method: Configure a DDNS update method to enable HTTP update requests from the Firewall Threat Defense. | ||
Step 5 | Configure interface settings for DDNS, including setting the update method, DHCP client settings, and the hostname for this interface.
| ||
Step 6 | If you enable the DHCP server on an Firewall Threat Defense, you can configure DHCP server settings for DDNS. To enable the DHCP server, see Configure the DHCPv4 Server). You can configure the server behavior when DHCP clients use the standard DDNS update method. If the server performs any updates, then if the client lease expires (and is not renewed), the server will request that the DNS server remove the RRs for which it was responsible. | ||
Step 7 | (Optional) Configure general DHCP client settings. These settings are not related to DDNS, but are related to how the DHCP client behaves. | ||
Step 8 | Click Save on the Device page to save your changes. | ||
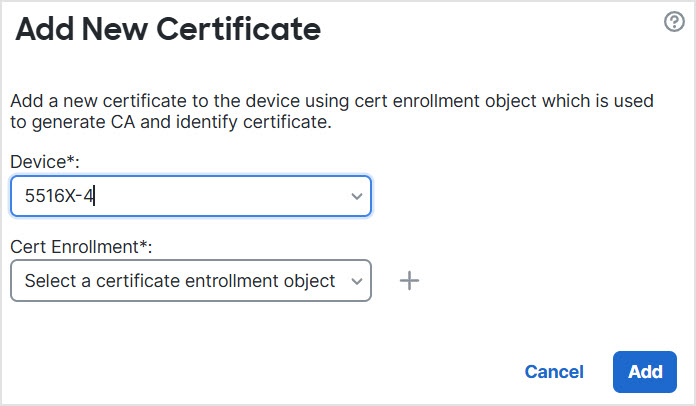
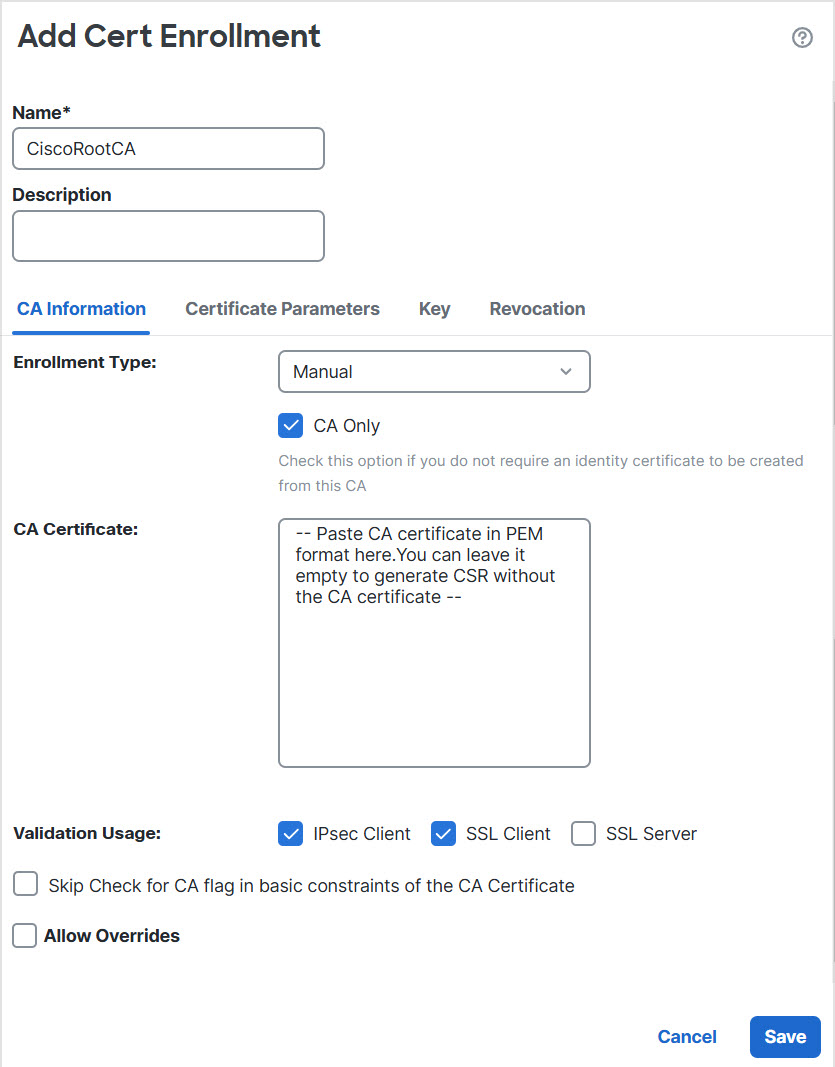
Step 9 | The Web method for DDNS also requires you to identify the DDNS server root CA to validate the DDNS server certificate for the HTTPS connection. The following example shows how to add a DDNS server's CA as a trustpoint. |