Create a rule-based decryption policy with inbound connection protection
This task discusses how to create a decryption policy with a rule that protects inbound connections; that is, the destination server is inside your protected network. This type of rule has a Decrypt - Known Key rule action.
When you create a decryption policy, you can create multiple rules at the same time, including multiple Decrypt - Known Key rules and multiple Decrypt - Resign rules.
Before you begin
You must upload an internal certificate for your internal server before you can create a decryption policy that protects inbound connections. You can do this in any of the following ways:
-
Create an internal certificate object by going to and referring to PKI.
-
At the time you create this decryption policy.
If you enabled Change Management, you must create and assign a ticket before you can create a decryption policy. Before the decryption policy can be used, the ticket and all associated objects (like certificate authorities) must be approved. For more information, see Creating change management tickets and Policies and objects that support change management.
Procedure
Step 1 | Log in to Security Cloud Control if you haven't already done so. |
Step 2 | Click . |
Step 3 | Click Create Decryption Policy. |
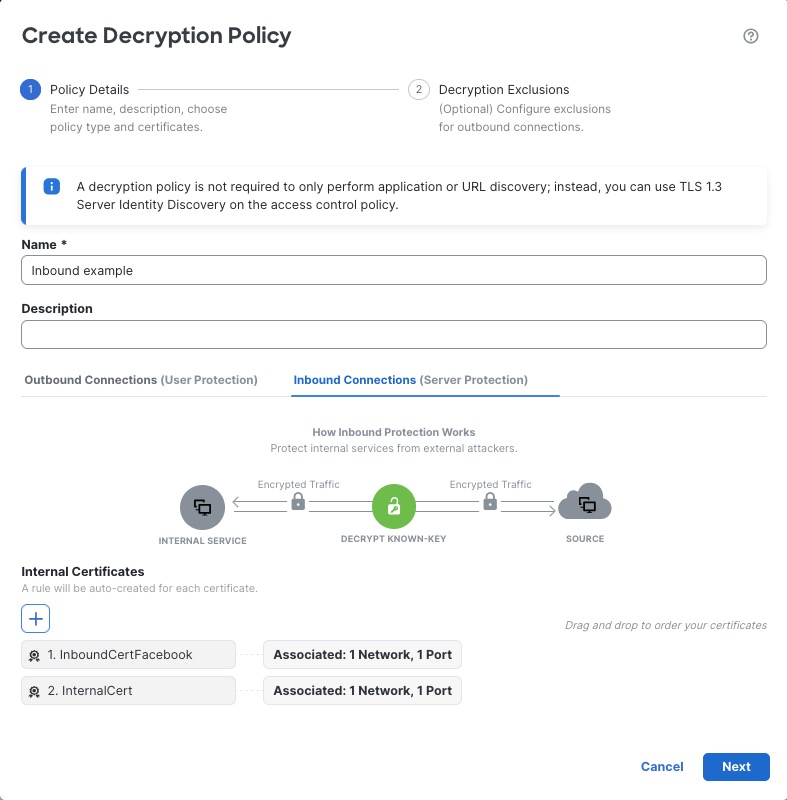
Step 4 | Give the policy a unique Name and, optionally, a Description. The following characters are not supported in decryption policy names:
|
Step 5 | From the Internal Certificates list, upload or choose certificates for the rules. For more information about internal CA certificates, see Internal Certificate Authority Objects. |
Step 6 | (Optional.) Choose networks and ports. For more information: |
Step 7 | Click the Inbound Connections tab.
|
Step 8 | Click Next. |
Step 9 | Continue with Rule-based decryption policy exclusions. |
Step 10 | Click Save. |
What to do next
-
Add rule conditions: Rule-based decryption rule conditions
-
Add a default policy action: Rule-based decryption policy default actions
-
Configure logging options for the default action .
-
Set advanced policy properties: Rule-based decryption policy advanced options.
-
Associate the decryption policy with an access control policy as described in Associating other policies with access control.
-
Deploy configuration changes.