View and Edit Your Snort 3 Intrusion Policy
Procedure
Step 1 | Choose . | ||
Step 2 | Ensure that the Intrusion Policies tab is chosen. | ||
Step 3 | Click Snort 3 Version next to the intrusion policy that you want to view or edit. | ||
Step 4 | Close the Snort helper guide that is displayed. | ||
Step 5 | Click the Group Overrides layer. This layer lists all the categories of rule groups in an hierarchical structure. You can drill down to the last leaf rule group under each rule group. 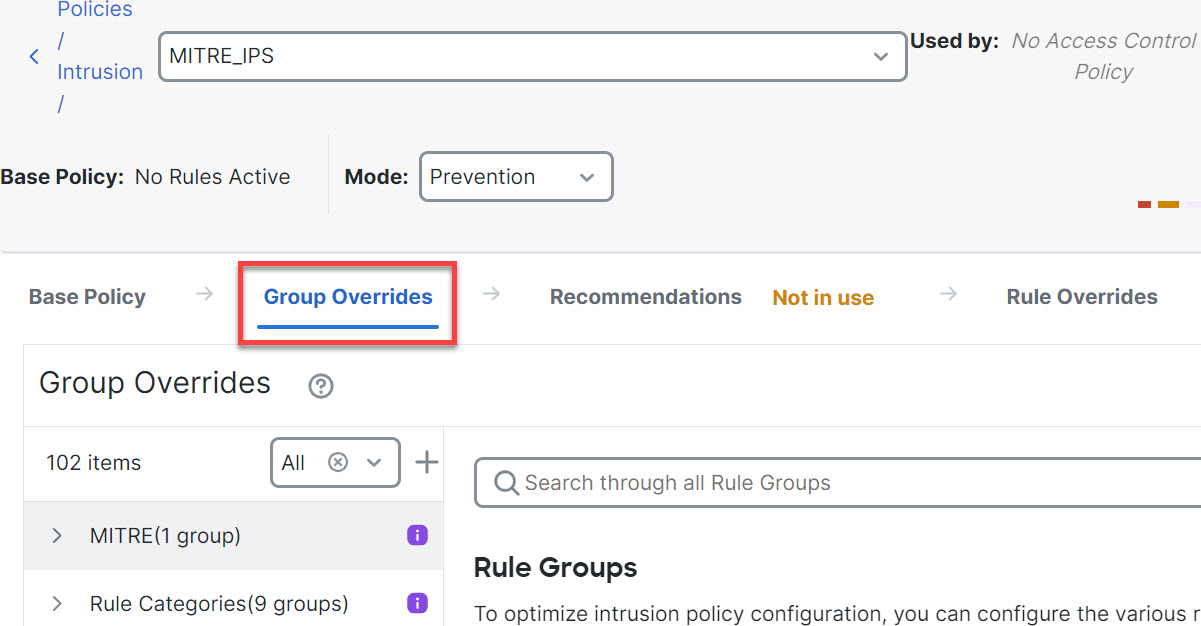 | ||
Step 6 | Under Group Overrides, ensure that All is chosen in the drop-down list, so that all the rule groups for the corresponding intrusion policy are visible in the left pane. 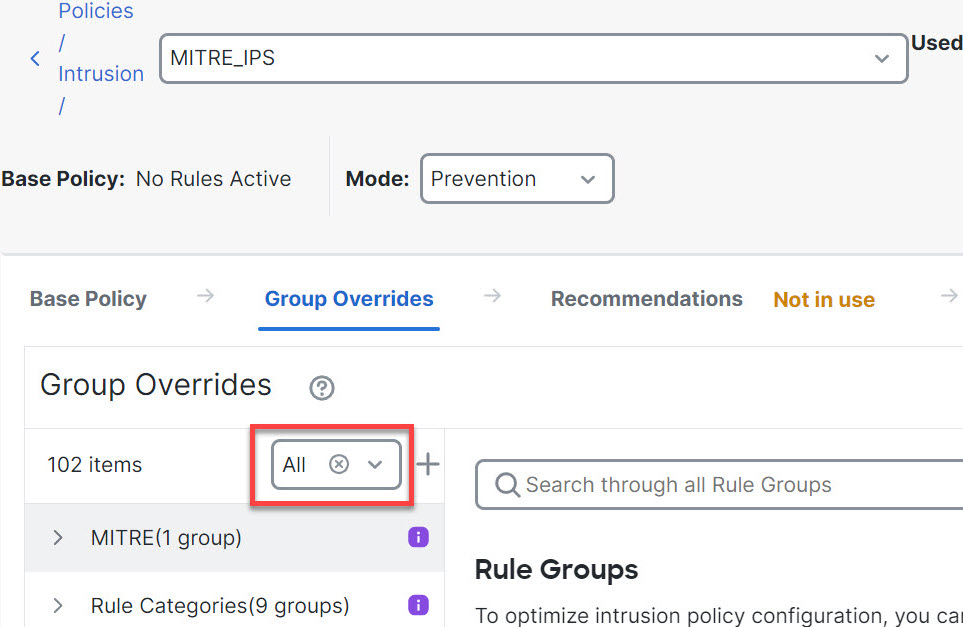
| ||
Step 7 | Click MITRE in the left pane.
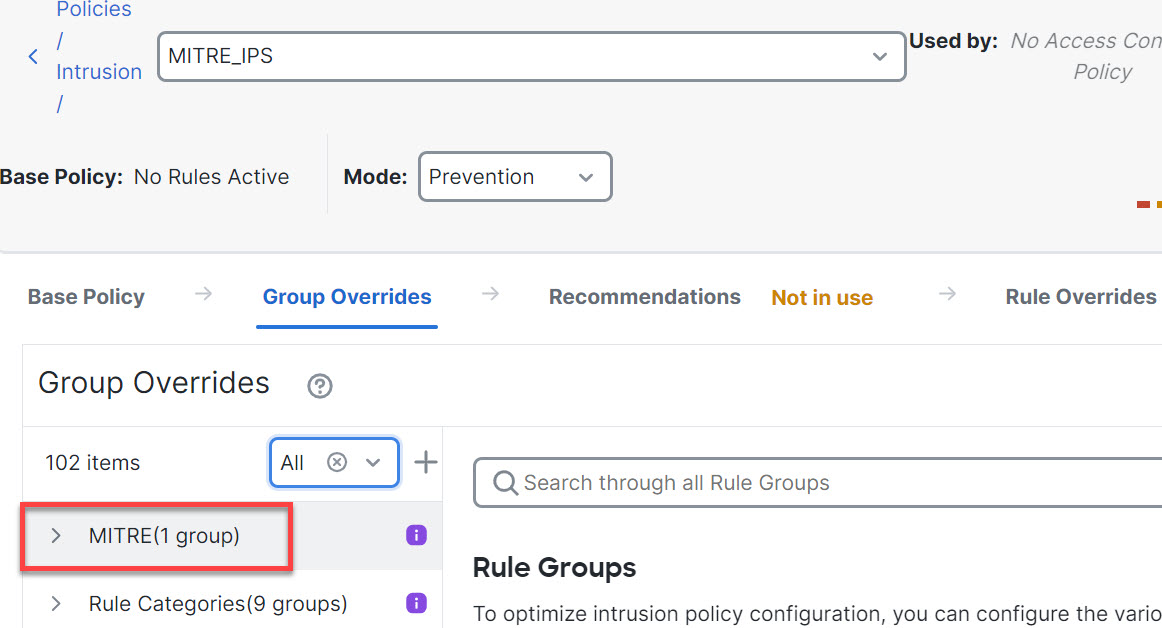 | ||
Step 8 | Under MITRE, click ATT&CK Framework to drill down. 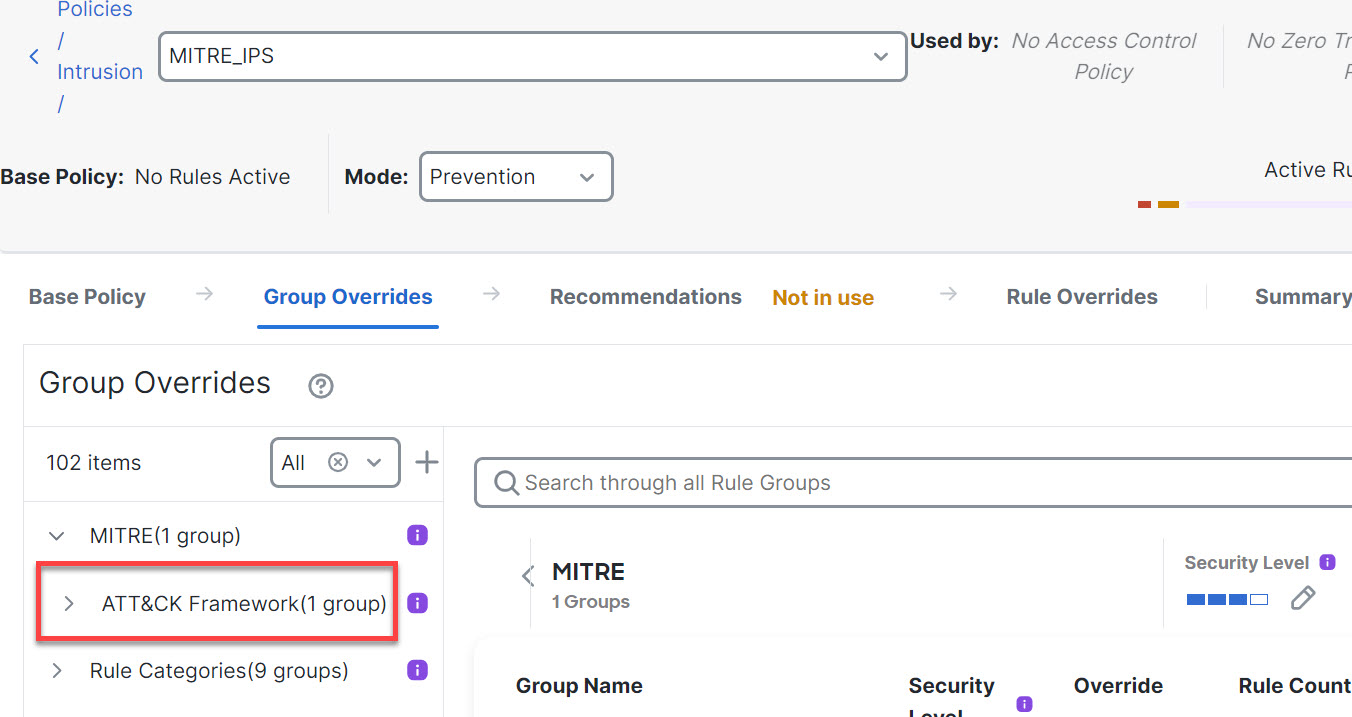
| ||
Step 9 | Under ATT&CK Framework, click Enterprise to expand it. 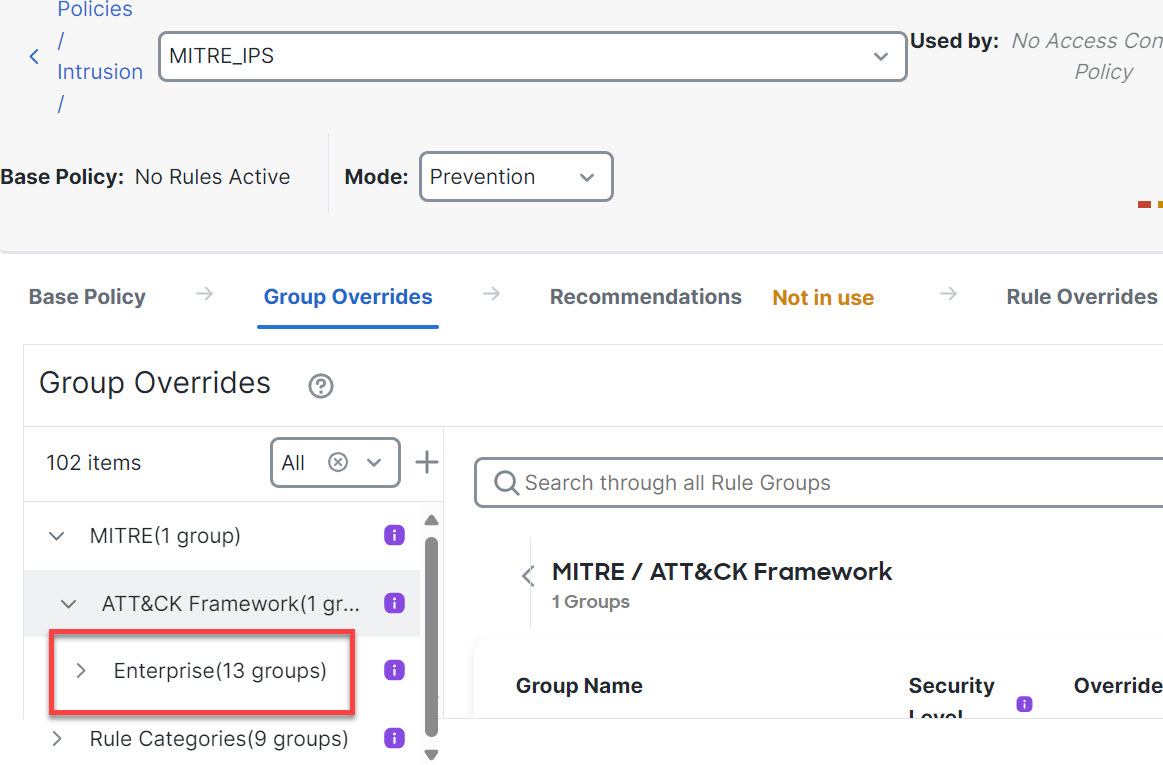
| ||
Step 10 | Click the Edit ( 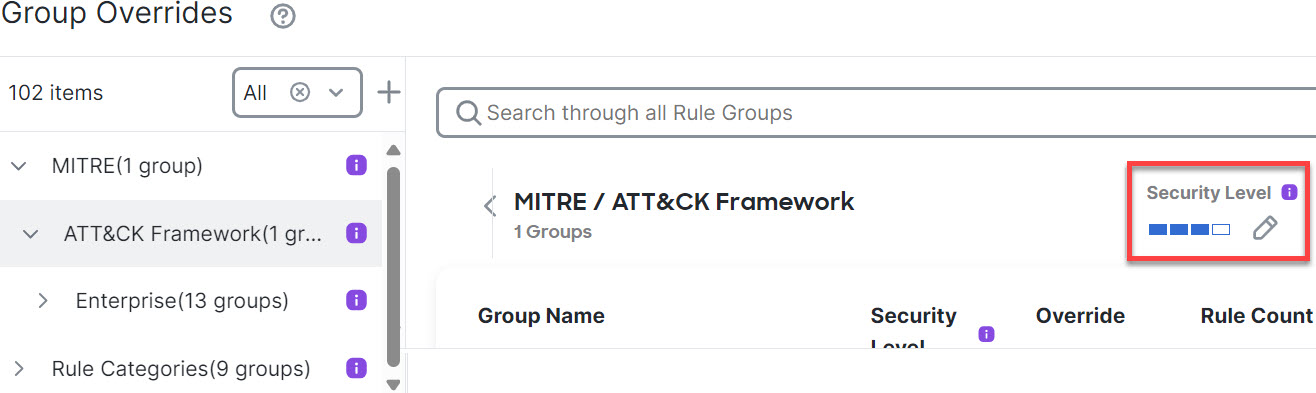
| ||
Step 11 | In the Edit Security Level window, choose a Security Level (in this example, 3), and click Save. 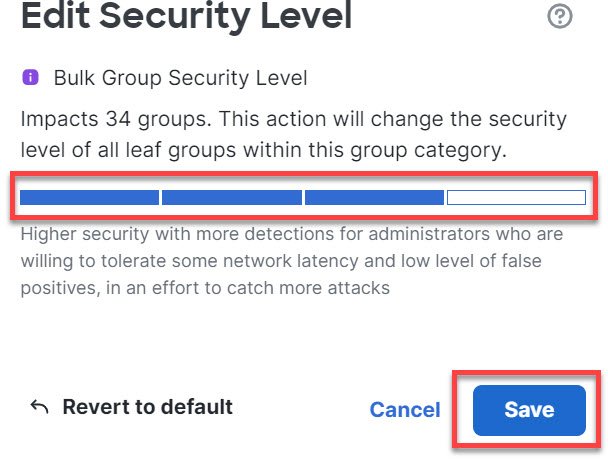
| ||
Step 12 | Under Enterprise, click Initial Access to expand it. | ||
Step 13 | Under Initial Access, click Exploit Public-Facing Application, which is the last leaf group. 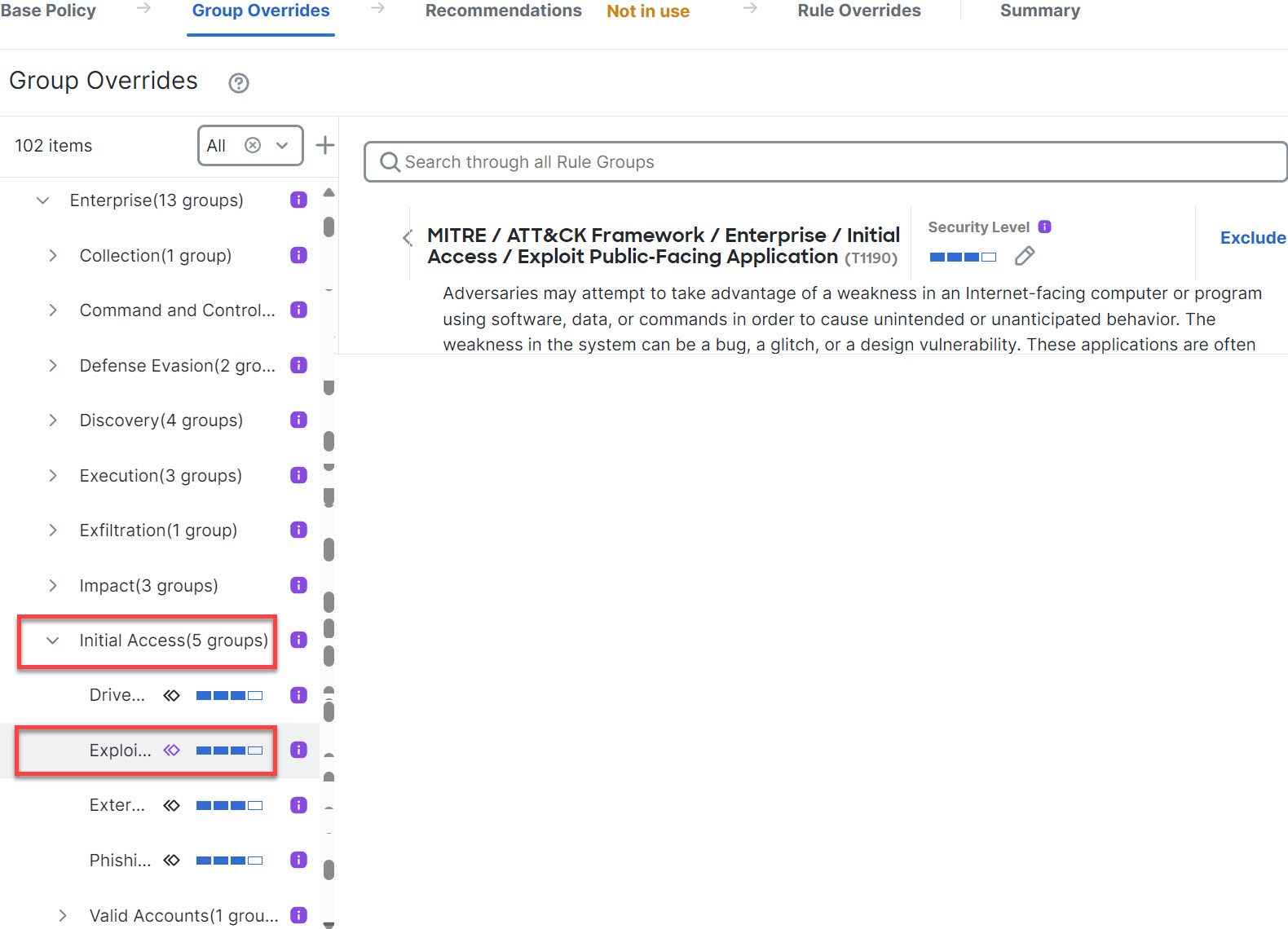
| ||
Step 14 | Click View Rules in Rule Overrides to view the different rules, rule details, rule actions, and so on, for the different rules. You can change the rule actions for one or multiple rules in the Rule Overrides layer. 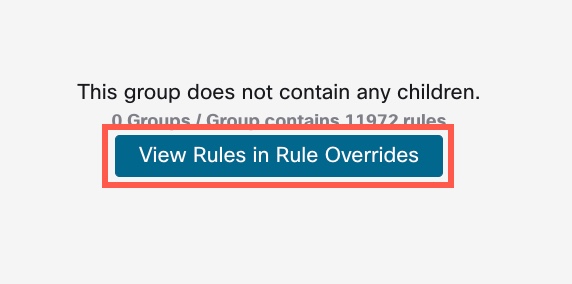
| ||
Step 15 | Click the Recommendations layer and then click Start to start using Cisco-recommended rules. You can use the intrusion rule recommendations to target the vulnerabilities that are associated with the host assets detected in the network. For more information, see Generate New Secure Firewall Recommendations in Snort 3. 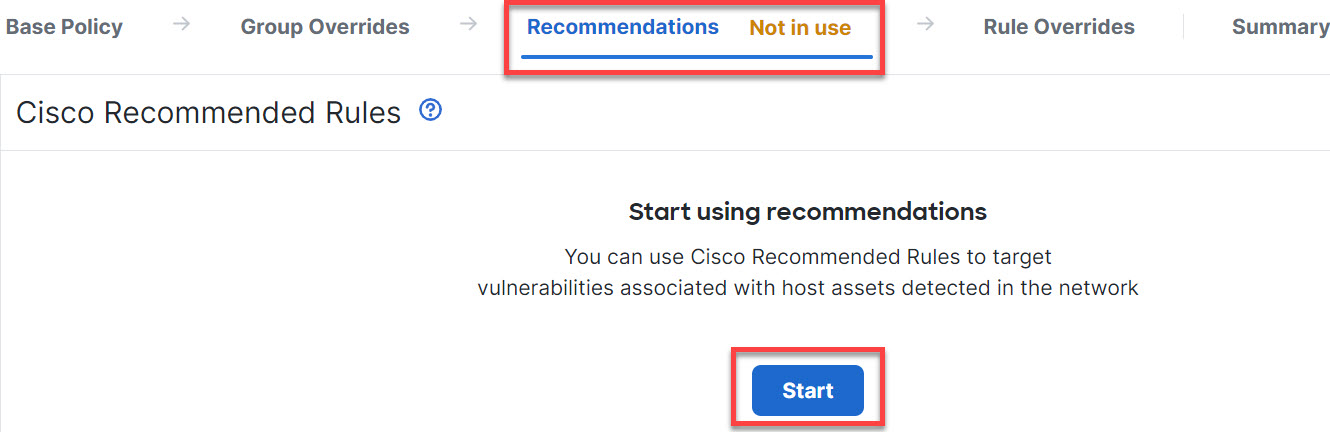
| ||
Step 16 | Click the Summary layer for a holistic view of the current changes to the policy. Based on the rule overrides, security-level changes, and generation of Cisco-recommended rules, you can view the rule distribution of the policy, group overrides, rule overrides, rule recommendations, and so on, to verify your changes. 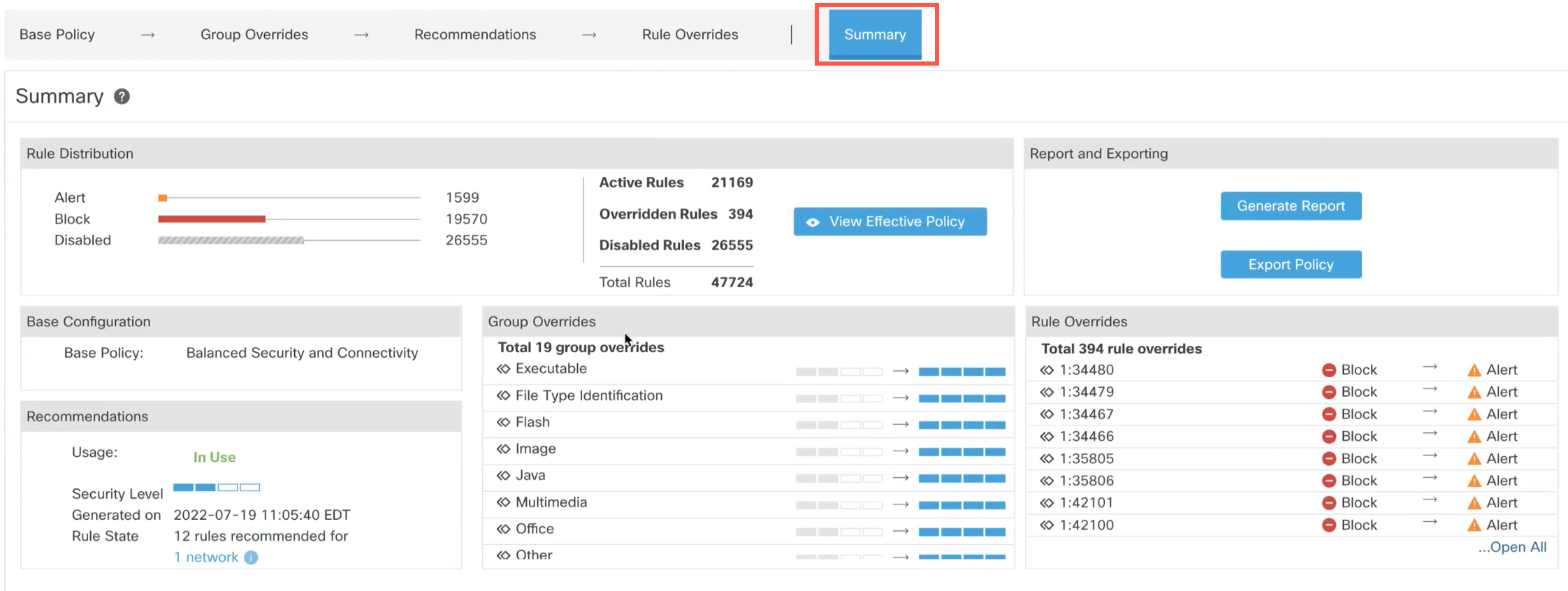
|
What to do next
Deploy your intrusion policy to detect and log events that are triggered by the Snort rules. See Deploy Configuration Changes.