Run the Decryption Policy Wizard
This task discusses how to run the decryption policy wizard for outbound traffic protection. This policy has four rules:
-
Do Not Decrypt rule for distinguished names that are known to be undecryptable, most likely because they use TLS/SSL pinning.
-
Do Not Decrypt rule for URL categories that we classify as sensitive based on their content (for example, medical and financial).
-
Do Not Decrypt rule for applications that are known to be undecryptable, most likely because they use TLS/SSL pinning.
-
Decrypt - Resign rule that uses a certificate authority object named IntCA to decrypt the remainder of the traffic.
You can then edit the rules if you want and also manually add:
-
Decrypt - Resign rules for traffic to monitor and determine whether the traffic should be blocked in the future.
-
Do Not Decrypt rules for other types of traffic
-
Block or Block with Reset rules for bad certificates and unsecure cipher suites.
If you enabled Change Management, you must create and assign a ticket before you can create a decryption policy. Before the decryption policy can be used, the ticket and all associated objects (like certificate authorities) must be approved. For more information, see Creating Change Management Tickets and Policies and Objects that Support Change Management.
Procedure
Step 1 | Log in to the Secure Firewall Management Center if you haven't already done so. |
Step 2 | Click . |
Step 3 | Click Create Decryption Policy. |
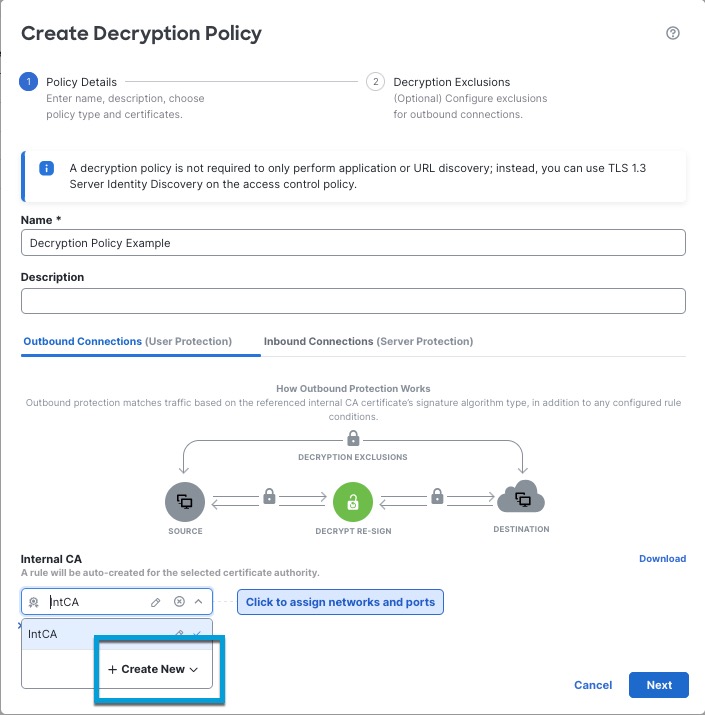
Step 4 | Give the decryption policy a Name and optionally a Description. |
Step 5 | Click the Outbound Protection tab. |
Step 6 | From the Internal CA list, click the name of an internal certificate authority object or click Create New to upload or generate one. The following figure shows an example.
For more information about creating or uploading an internal certificate authority object, see: |
Step 7 | (Optional.) To restrict traffic to source and destination networks, click Click to assign networks and ports. |
Step 8 | Click Next. |
Step 9 | Complete the wizard as discussed in Decryption Policy Exclusions. |