Before You Begin
Prior to adding an AD group mapping to CDO as a form of user management, you must have your AD integrated with SecureX. If your AD Identity Provider (IdP) is not already integrated, you must do the following operations:
-
Open a Support Case with Cisco TAC and request a custom AD IdP integration with the following information:
-
Your CDO tenant name and region.
-
Domain to define custom routing for (for example : @cisco.com, @myenterprise.com).
-
Certificate and federation metadata in .XML format.
-
-
Add the following custom SAML claims in your AD. Note these values are case sensitive.
-
SamlADUserGroupIds - This attribute describes all group associations a user has on AD. For example, in Azure select + Add a group claim as seen in the screenshot below:
Custom Claims defined in Active Directory 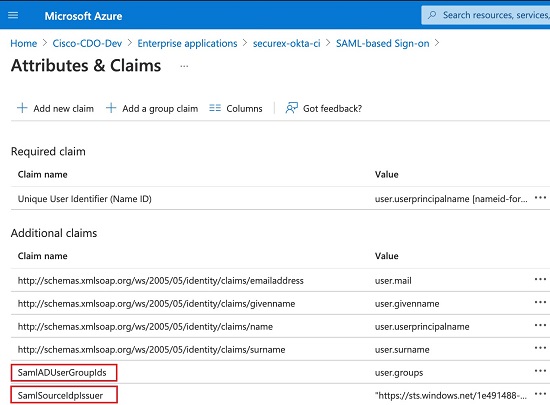
-
SamlSourceIdpIssuer - This attribute uniquely identifies an AD instance. For example, in Azure select+ Add a group claim and scroll to locate the Azure AD Identifier as seen in the screenshot below:
Locate the Azure Active Directory Identifier 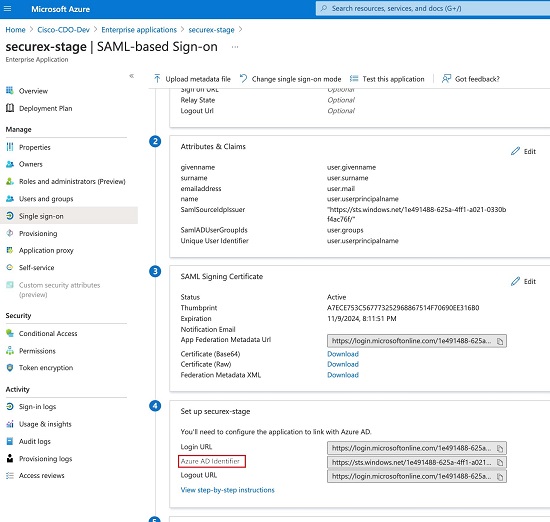
-