Access control policy default action
A newly created access control policy directs its assigned devices to handle all traffic using its default action.
In a simple access control policy, the default action specifies how a device handles all traffic. In a more complex policy, the default action handles traffic that:
-
is not fast pathed by the prefilter policy
-
is not on a Security Intelligence block list
-
is not blocked by the decryption policy (encrypted traffic only)
-
matches none of the rules in the policy (except monitor rules, which match and log—but do not handle or inspect—traffic)
The access control policy default action can block or trust traffic without further inspection, or inspect traffic for intrusions and discovery data.
Note | You cannot perform file or malware inspection on traffic handled by the default action. Logging for connections handled by the default action is initially disabled, though you can enable it. |
If you are using policy inheritance, the default action for the lowest-level descendant determines final traffic handling. Although an access control policy can inherit its default action from its base policy, you cannot enforce this inheritance.
The following table describes the types of inspection you can perform on traffic handled by each default action.
|
Default Action |
Effect on Traffic |
Inspection Type and Policy |
|---|---|---|
|
Access Control: Block All Traffic |
Block without further inspection. |
None. |
|
Access Control: Trust All Traffic |
Trust (allow to its final destination without further inspection). |
None. |
|
Intrusion Prevention |
Allow, as long as it is passed by the intrusion policy you specify. |
Intrusion, using the specified intrusion policy and associated variable set. Discovery, using the network discovery policy. |
|
Network Discovery Only |
Allow. |
Discovery only, using the network discovery policy. |
|
Inherit from base policy |
Defined in base policy. |
Defined in base policy. |
The following diagram illustrates the table.
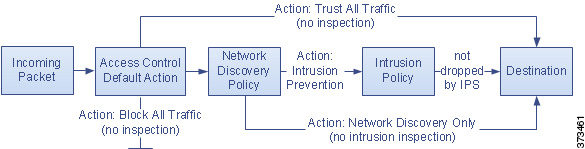
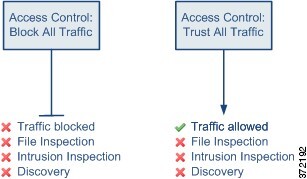
The following diagrams illustrate the Block All Traffic and Trust All Traffic default actions.
The following diagrams illustrate the Intrusion Prevention and Network Discovery Only default actions.

Tip | The purpose of Network Discovery Only is to improve performance in a discovery-only deployment. Different configurations can disable discovery if you are only interested in intrusion detection and prevention. |