ClientHello message handling
The client sends the ClientHello message to the server that acts as the packet destination if a secure connection can be established. The client sends the message to initiate the TLS/SSL handshake or in response to a ServerHello message from the destination server.
Overview
The following figure shows an example. Also see RFC 8446, sec. 4 . You can also consult a resource such as What Happens in a TLS Handshake? at cloudflare.com.
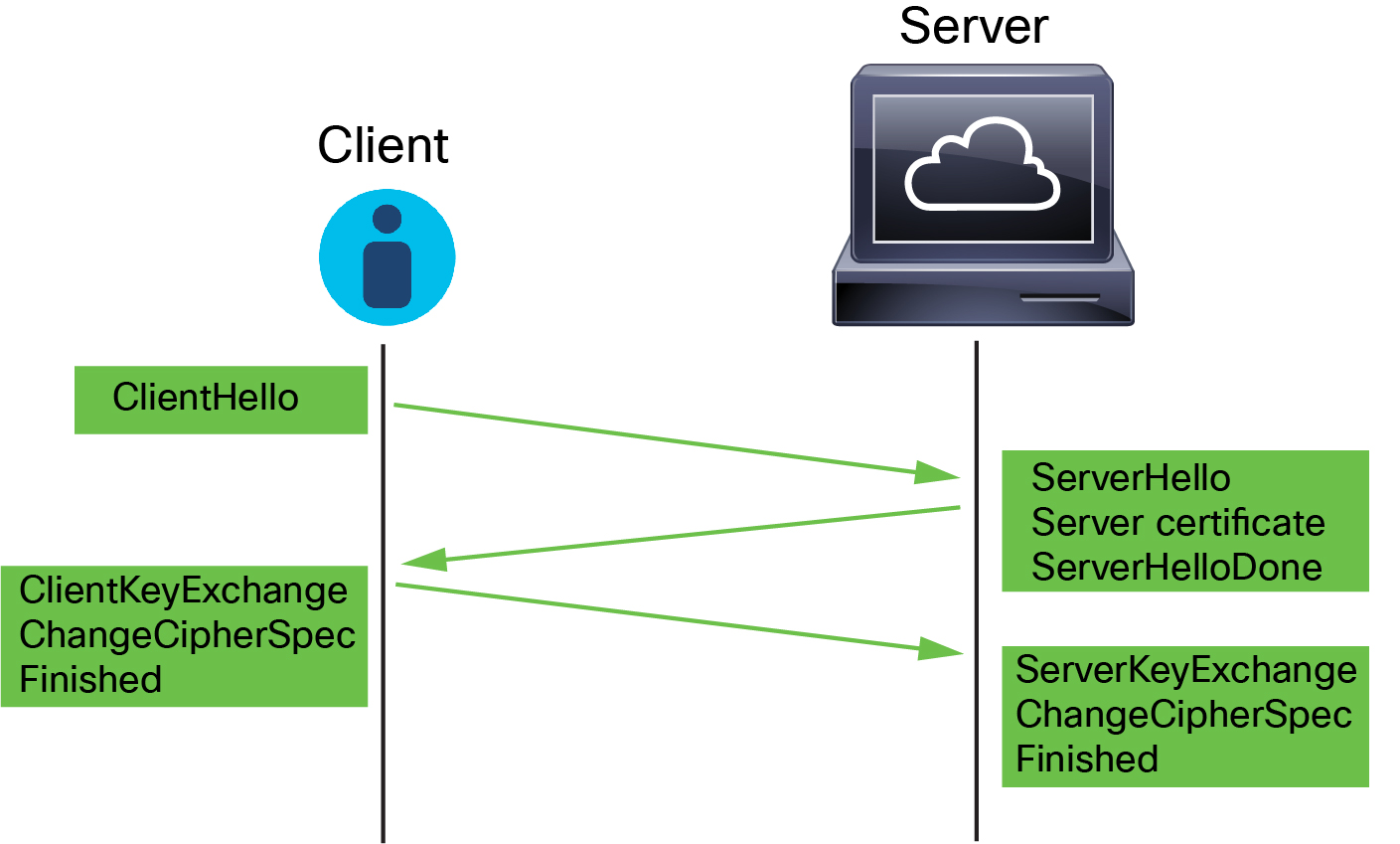
The process can be summarized as follows:
-
ClientHello initiates the process.
The ClientHello message contains the Server Name Indication (SNI), which has the server's fully qualified domain name.
-
After a managed device processes a ClientHello message and transmits it to the destination server, the server determines whether it supports the decryption attributes the client specified in the message. If it does not support those attributes, the server sends a handshake failure alert to the client. If it supports those attributes, the server sends the ServerHello message. If the agreed-upon key exchange method uses certificates for authentication, the server certificate message immediately follows the ServerHello message.
The server certificate contains the Subject Alternative Name (SAN), which can have fully qualified domain names and IP addresses. For more information about the SAN, see Distinguished Name.
-
When the managed device receives these messages, it attempts to match them with decryption rules configured on the system. These messages contain information that was absent from either the ClientHello message or the session data cache. Specifically, the system can potentially match these messages on decryption rules' Distinguished Names, Certificate Status, Cipher Suites, and Versions conditions.
The entire process is encrypted.
Data exchange
If you configure TLS/SSL decryption, when a managed device receives a ClientHello message, the system attempts to match the message to decryption rules that have the Decrypt - Resign, or Decrypt - Known Key action. The match relies on data from the ClientHello message and from cached server certificate data. Possible data includes:
|
Decryption rule Condition |
Data Present In |
|---|---|
|
Zones |
ClientHello |
|
Networks |
ClientHello |
|
VLAN Tags |
ClientHello |
|
Ports |
ClientHello |
|
Users |
ClientHello |
|
Applications |
ClientHello (Server Name Indicator extension) |
|
Categories |
ClientHello (Server Name Indicator extension) |
|
Certificate |
Server certificate (potentially cached) |
|
Distinguished Names |
Server certificate (potentially cached) |
|
Certificate Status |
Server certificate (potentially cached) |
|
Cipher Suites |
ServerHello |
|
Versions |
ServerHello |
Important | Use the Cipher Suite and Version rule conditions only in rules with either the Block or Block with reset rule actions. Do not use Cipher Suite and Version with Decrypt - Resign or Decrypt - Known Key rule actions. These conditions in rules with other rule actions can interfere with the system's ClientHello processing, resulting in unpredictable performance. |
ClientHello modifications
If the ClientHello message matches a Decrypt - Resign, or Decrypt - Known Key rule, the system modifies the ClientHello message as follows:
-
(TLS 1.2 only; TLS 1.3 does not support compression.) Compression methods—Strips the
compression_methodselement, which specifies the compression methods the client supports. The system cannot decrypt compressed sessions. -
Cipher suites—Strips cipher suites from the
cipher_suiteselement if the system does not support them. If the system does not support any of the specified cipher suites, the system transmits the original, unmodified element. This modification reduces the Unknown Cipher Suite and Unsupported Cipher Suite types of undecryptable traffic. -
Session identifiers—Strips any value from the
Session Identifierelement and the SessionTicket extension (RFC 5077, sec 3.2) that does not match cached session data. If a ClientHello value matches cached data, an interrupted session can resume without the client and server performing the full TLS/SSL handshake. This modification increases the chances of session resumption and reduces the Session Not Cached type of undecryptable traffic. -
Elliptic curves—Strips elliptic curves from the Supported Elliptic Curves extension if the system does not support them. If the system does not support any of the specified elliptic curves, the managed device removes the extension and strips any related cipher suites from the
cipher_suiteselement. -
ALPN extensions—Strips any value from the Application-Layer Protocol Negotiation (ALPN) extension that is unsupported in the system (for example, the HTTP/2 protocol).
-
Other Extensions—Strips the Next Protocol Negotiation (NPN) and TLS Channel IDs extensions.
Decryption rules with a Decrypt - Resign, or Decrypt - Known Key action now natively support the Extended Master Secret (EMS) extension during ClientHello negotiation, enabling more secure communications. The EMS extension is defined by RFC 7627.
After the system modifies the ClientHello message, it determines whether the message passes access control evaluation (which can include deep inspection). If the message passes, the system transmits it to the destination server.
If the ClientHello message does not match a Decrypt - Resign, or Decrypt - Known Key rule, the system does not modify the message. It then determines whether the message passes access control evaluation (which can include deep inspection). If the message passes inspection, the system transmits it to the destination server.
ClientHello is not modified if traffic matches a Monitor rule condition.
Man-in-the-middle
Direct communication between the client and server is no longer possible during the TLS/SSL handshake, because after message modification the Message Authentication Codes (MACs) computed by the client and server no longer match. For all subsequent handshake messages (and for the encrypted session once established), the managed device acts as a man-in-the-middle. It creates two TLS/SSL sessions, one between client and managed device, one between managed device and server. As a result, each session contains different cryptographic session details.
Note | The cipher suites that the system can decrypt are frequently updated and do not correspond directly to the cipher suites you can use in decryption rule conditions. For the current list of decryptable cipher suites, contact Cisco TAC. |