ServerHello and server certificate message handling
Overview
The following figure shows an example. Also see RFC 8446, sec. 4 . You can also consult a resource such as What Happens in a TLS Handshake? at cloudflare.com.
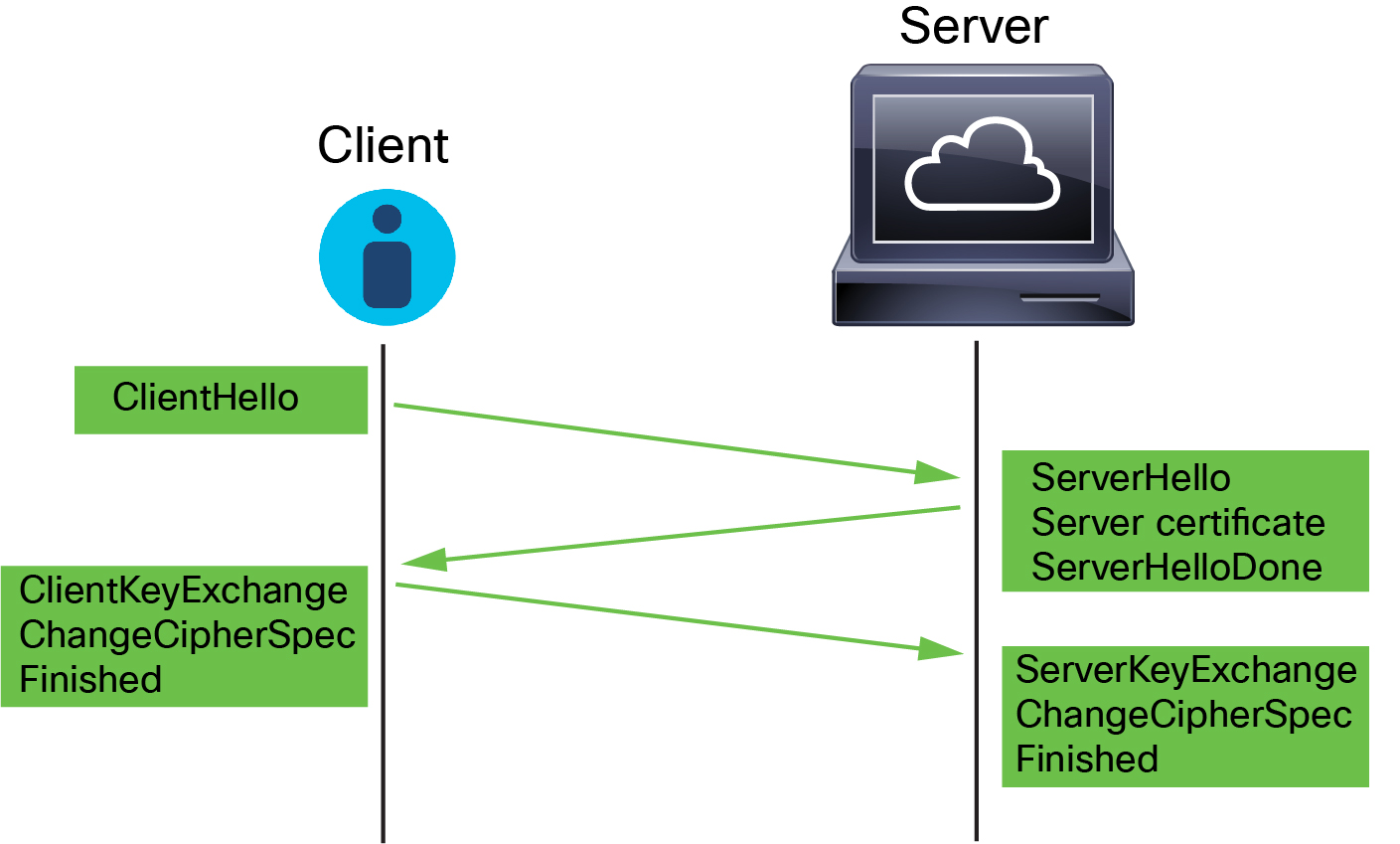
The process can be summarized as follows:
-
ClientHello initiates the process.
The ClientHello message contains the Server Name Indication (SNI), which has the server's fully qualified domain name.
-
After a managed device processes a ClientHello message and transmits it to the destination server, the server determines whether it supports the decryption attributes the client specified in the message. If it does not support those attributes, the server sends a handshake failure alert to the client. If it supports those attributes, the server sends the ServerHello message. If the agreed-upon key exchange method uses certificates for authentication, the server certificate message immediately follows the ServerHello message.
The server certificate contains the Subject Alternative Name (SAN), which can have fully qualified domain names and IP addresses. For more information about the SAN, see Distinguished Name.
-
When the managed device receives these messages, it attempts to match them with decryption rules configured on the system. These messages contain information that was absent from either the ClientHello message or the session data cache. Specifically, the system can potentially match these messages on decryption rules' Distinguished Names, Certificate Status, Cipher Suites, and Versions conditions.
The entire process is encrypted.
Decryption rule actions
If the messages do not match any decryption rules, the managed device performs the Rule-based decryption policy default actions.
If the messages match a rule that belongs to a decryption policy associated with an access control policy, the managed device continues as appropriate:
- Action: Monitor
- The TLS/SSL handshake continues to completion. The managed device tracks and logs traffic but does not decrypt it.
- Action: Block or Block with Reset
-
The managed device blocks the TLS/SSL session and, if configured, resets the TCP connection.
- Action: Do Not Decrypt
-
The TLS/SSL handshake continues to completion. The managed device does not decrypt the application data exchanged during the TLS/SSL session.
- Action: Decrypt - Known Key
-
The managed device attempts to match the server certificate data to an Internal Certificate object previously imported into the Security Cloud Control. Because you cannot generate an Internal Certificate object, and you must possess its private key, we assume you own the server on which you're using known key decryption.
If the certificate matches a known certificate, the TLS/SSL handshake continues to completion. The managed device uses the uploaded private key to decrypt and re-encrypt the application data exchanged during the TLS/SSL session.
If the server changes its certificate between the initial connection with the client and subsequent connections, you must import the new server certificate in the Security Cloud Control for future connections to be decrypted.
- Action: Decrypt - Resign
-
The managed device processes the server certificate message and re-signs the server certificate with the previously imported or generated certificate authority (CA). The TLS/SSL handshake continues to completion. The managed device then uses the uploaded private key to decrypt and re-encrypt the application data exchanged during the TLS/SSL session.
Note | The Firepower System does not support mutual authentication; that is, you cannot upload a client certificate to the Security Cloud Control and use it for Decrypt - Resign, Decrypt - Replace Cert, or Decrypt - Known Key decryption rule actions. |