Incoming traffic decryption actions
Both the Decrypt - Replace Cert and Decrypt - Known Key decryption actions enable you to decrypt incoming traffic to a server you want to protect from malicious attacks.
We provide the Decrypt - Replace Cert decryption action as an alternative to Decrypt - Known Key for the following reasons:
-
Certificates can expire or need to be replaced anytime.
If you choose the Decrypt - Known Key action, decryption can stop and the rule can stop functioning when a certificate is replaced for any reason.
-
With Decrypt - Replace Cert, the connection matches and traffic is decrypted, and deploying the certificate hours or days later on the device is not an issue.
-
Decrypt - Replace Cert gives you the flexibility to have separate internal and external facing certificates. For example, you could use
payroll.example.localas an internal server hostname, but usepayroll.example.comas an externally-facing hostname. You can also use an Enterprise PKI certificate for an internal server but use DigiCert or some other public provider for my external certificate.
The following figure shows the difference between Decrypt - Replace Cert and Decrypt - Known Key decryption actions.
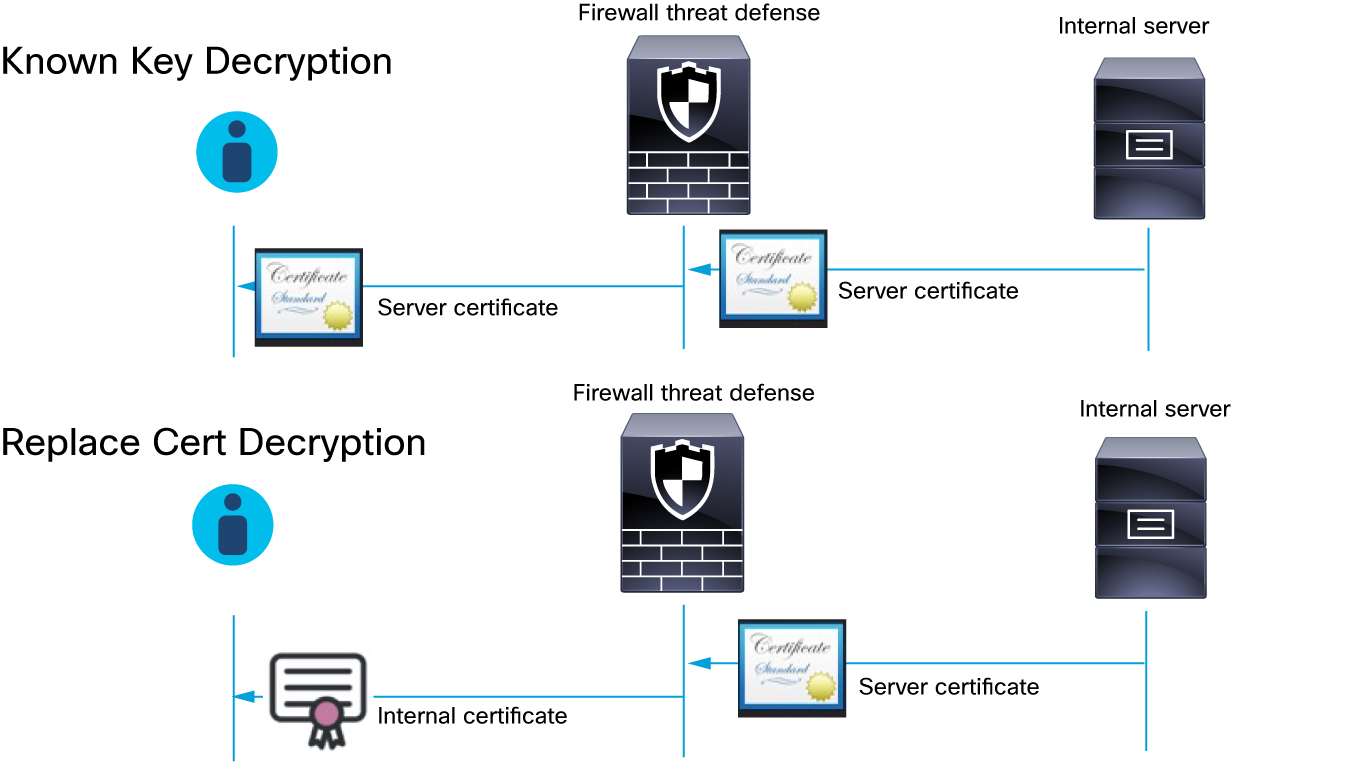
The following table provides more information.
|
Known Key |
Replace Cert |
|
|---|---|---|
|
Must match certificate installed on internal server or resource |
Yes |
No |
|
The device must trust the internal certificate (that is, it must be chained to Trusted CAs list in the decryption policy) |
No |
No |
|
Certificate hostnames can be different between device-installed certificate and that on the internal server |
No, certificates must be identical. (Although multiple SANs can be on the certificates to accommodate different internal and external host names.) |
Yes, certificates and certificate host names can be completely different, as long as the internal certificate is trusted by the user's device. |
|
Works if the internal server certificate is expired |
Yes – As long as it matches the certificate installed on the device. |
No – an expired certificate causes broken trust, and therefore a mismatch. |