Configure Elephant Flow Remediation Exemption
You can configure L4 access control list (ACL) rules for flows that must be exempted from remediation. If a flow is detected as an elephant flow and it matches the rules that are defined, that flow is exempted from the remediation action.
Before you begin
You must be running management center 7.4.0 or later and the managed threat defense must also be 7.4.0 or later.
Procedure
Step 1 | Choose . |
Step 2 | Click Edit ( |
Step 3 | Choose Advanced Settings from the More drop-down arrow at the end of the packet flow line. |
Step 4 | Click Edit ( |
Step 5 | Ensure that you have configured the elephant flow detection and remediation parameters. See Configure Elephant Flow Parameters. |
Step 6 | Click the Add Rule button next to Remediation Exemption Rules. 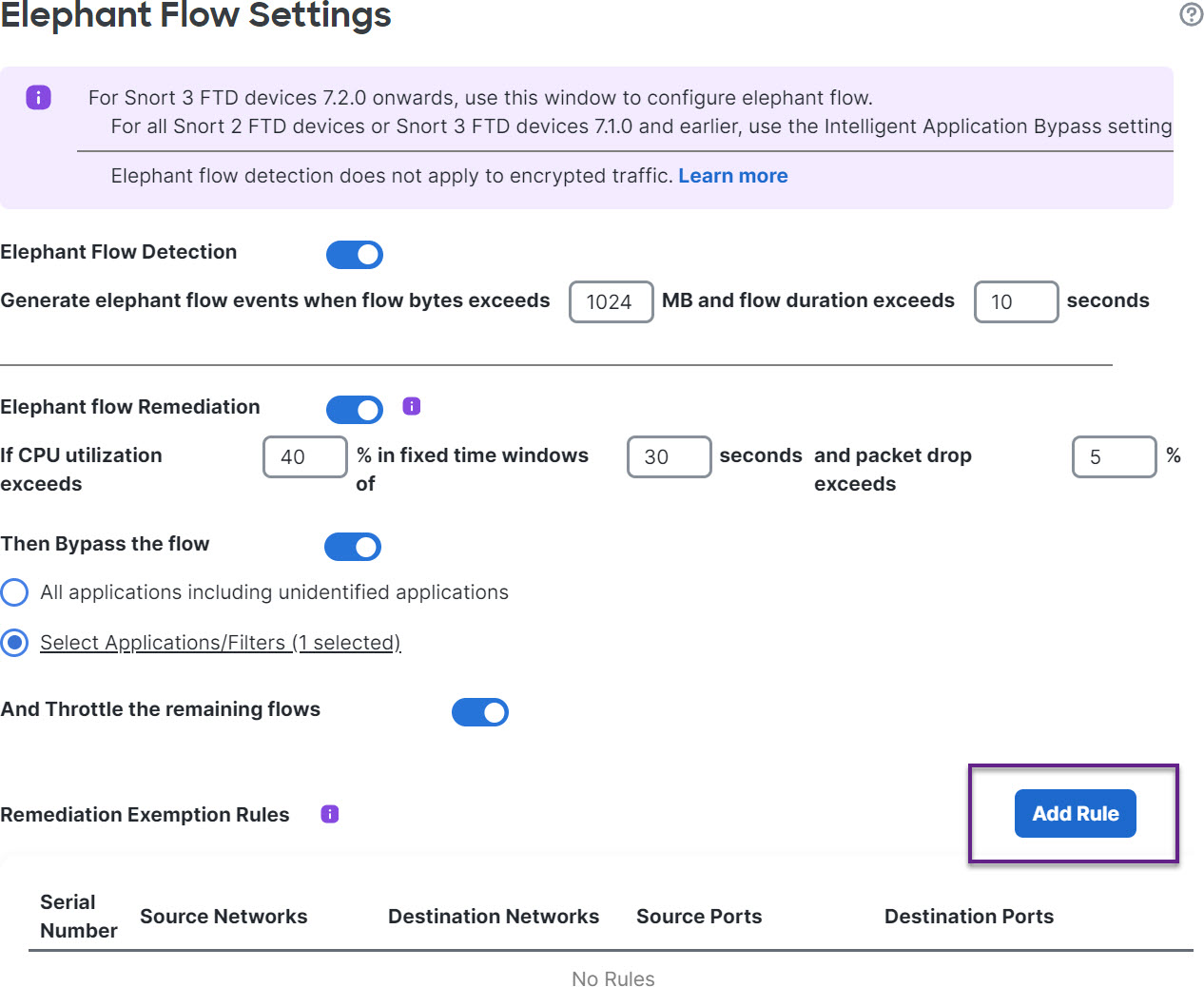
|
Step 7 | From the list of Available Networks, choose the configured host to exempt from elephant flow remediation. For the purposes of this example, we have created a host called “Host1_Exception.” 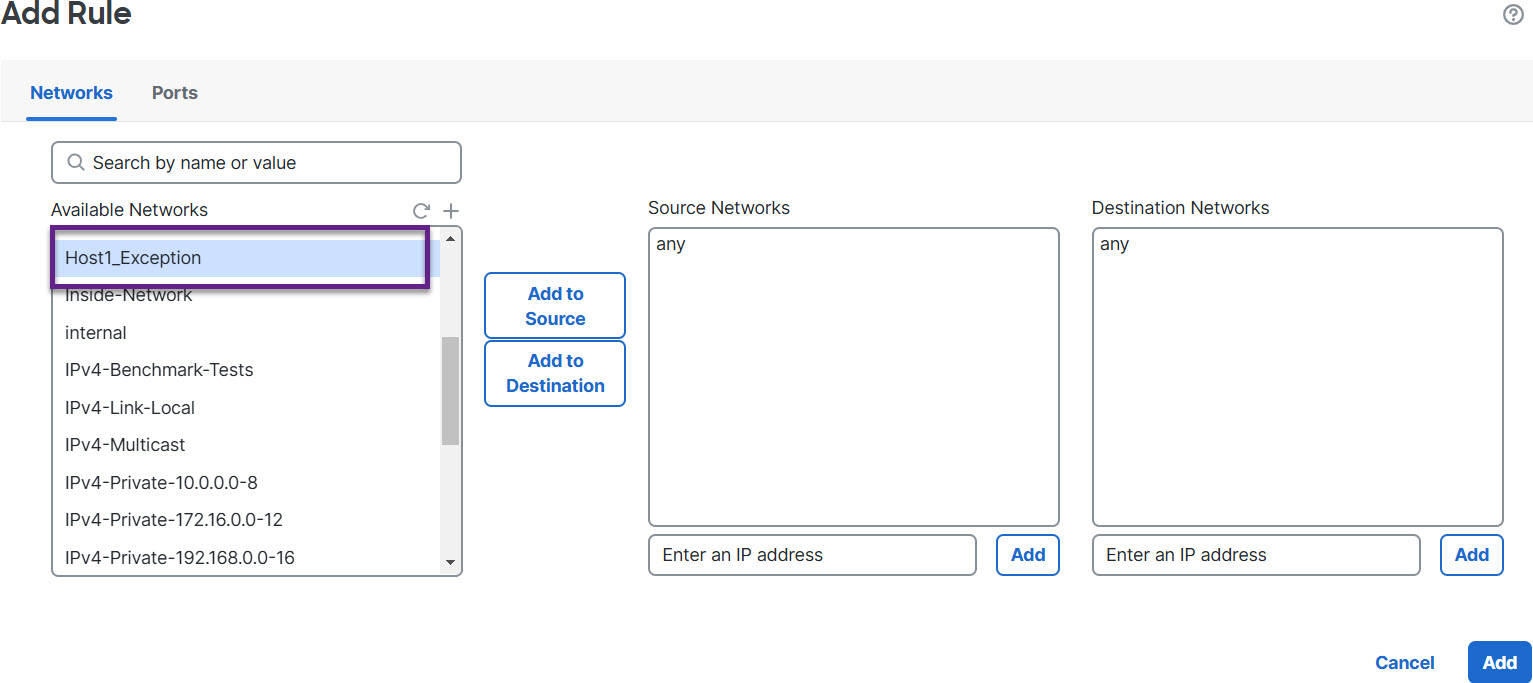
|
Step 8 | Click Add to Source or Add to Destination (as required) to add this host to the source or destination. |
Step 9 | Click the Ports tab. |
Step 10 | For the source port, choose Protocol as TCP and enter 80 as the destination port, and click Add. 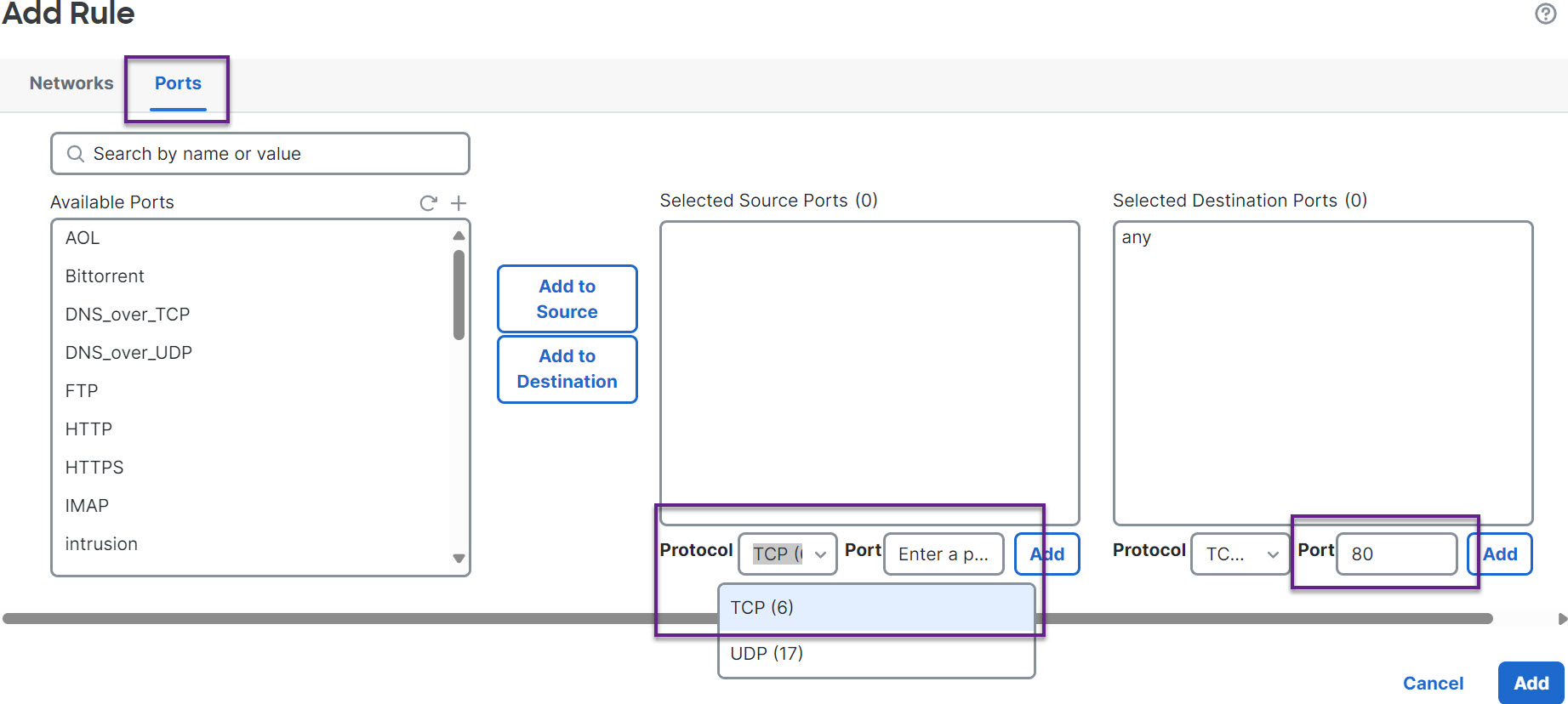
|
Step 11 | Click OK. 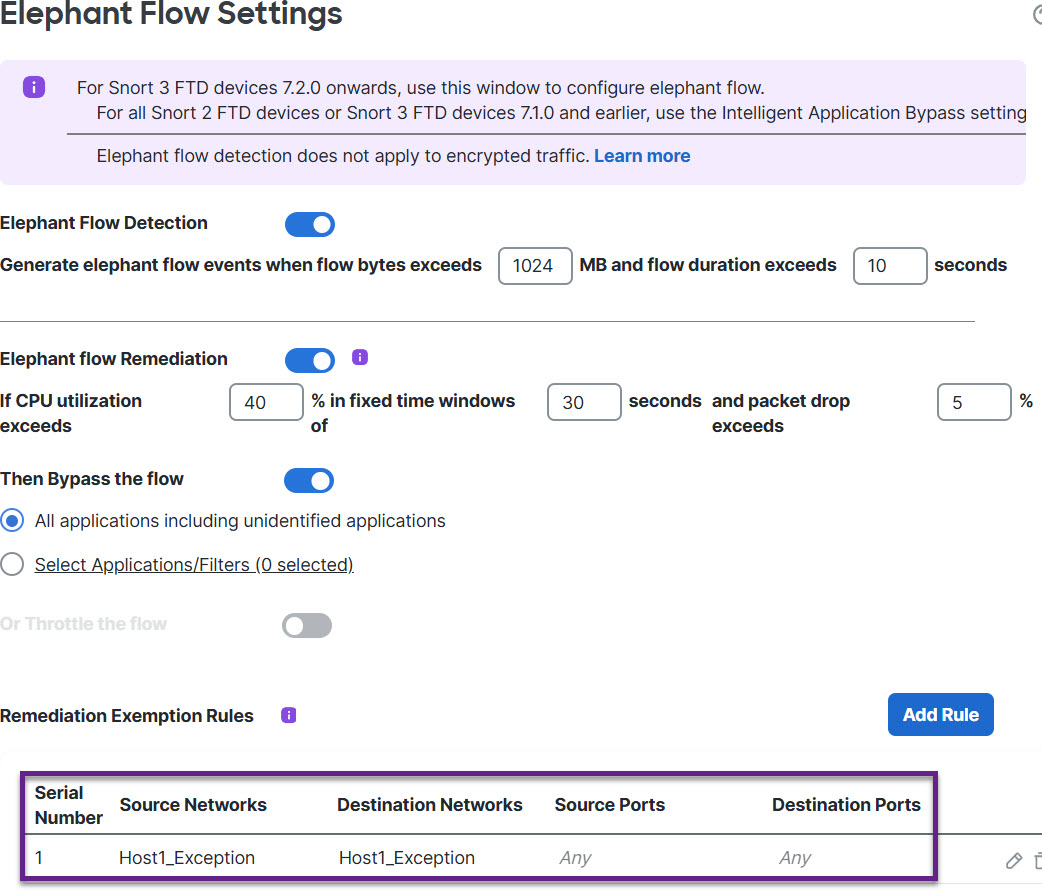
|
Step 12 | Click Save. |
What to do next
Deploy configuration changes. See Deploy Configuration Changes.