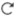Configure Security Intelligence
Each access control policy has Security Intelligence options. You can add network objects, URL objects and lists, and Security Intelligence feeds and lists to a Block list or Do Not Block list, and constrain any of these by security zone. You can also associate a DNS policy with your access control policy, and add domain names to a Block or Do Not Block list.
The number of objects in the Do Not Block lists plus the number in the Block lists cannot exceed 125 network objects, or 32767 URL objects and lists.
Before you begin
-
Tip: For guidance on minimum configuration recommendations, see also Configuration Example: Security Intelligence Blocking.
-
To ensure that all options are available to select, add at least one managed device to your management center.
-
In passive deployments, or if you want to set Security Intelligence filtering to monitor-only, enable logging
-
Configure a DNS policy to take Security Intelligence action for domains. For more information, see DNS Policies.
Procedure
Step 1 | In the access control policy editor, click Security Intelligence. If the controls are dimmed, settings are inherited from an ancestor policy, or you do not have permission to modify the configuration. If the configuration is unlocked, uncheck Inherit from base policy to enable editing. | ||
Step 2 | You have the following options:
| ||
Step 3 | Find the Available Objects you want to add to the Block or Do Not Block list. You have the following options:
Security Intelligence ignores IP address blocks using a | ||
Step 4 | Choose one or more Available Objects to add. | ||
Step 5 | (Optional) Choose an Available Zone to constrain the selected objects by zone. You cannot constrain system-provided Security Intelligence lists by zone.
| ||
Step 6 | Click Add to Do Not Block list or Add to Block list, or click and drag the selected objects to either list. To remove an object from a Block or Do Not Block list, click Delete ( | ||
Step 7 | (Optional) Set objects on the Block list to monitor-only by right-clicking the object under Block List, then choosing Monitor-only (do not block). You cannot set system-provided global Security Intelligence lists to monitor only. | ||
Step 8 | Choose a DNS policy from the DNS Policy drop-down list. | ||
Step 9 | Click Save. |
What to do next
-
Deploy configuration changes.