Configure elephant flow detection
You can configure elephant flow to take actions on elephant flows, which helps resolve issues, such as system duress, high CPU utilization, packet drops, and so on.
Attention | Elephant flow detection is not applicable for prefiltered, trusted, or fast-forwarded flows, which do not process through Snort. As elephant flows are detected by Snort, elephant flow detection is not applicable for encrypted traffic. |
Procedure
Step 1 | In the access control policy editor, click Advanced Settings from the More drop-down arrow at the end of the packet flow line. Then, click Edit ( If View ( 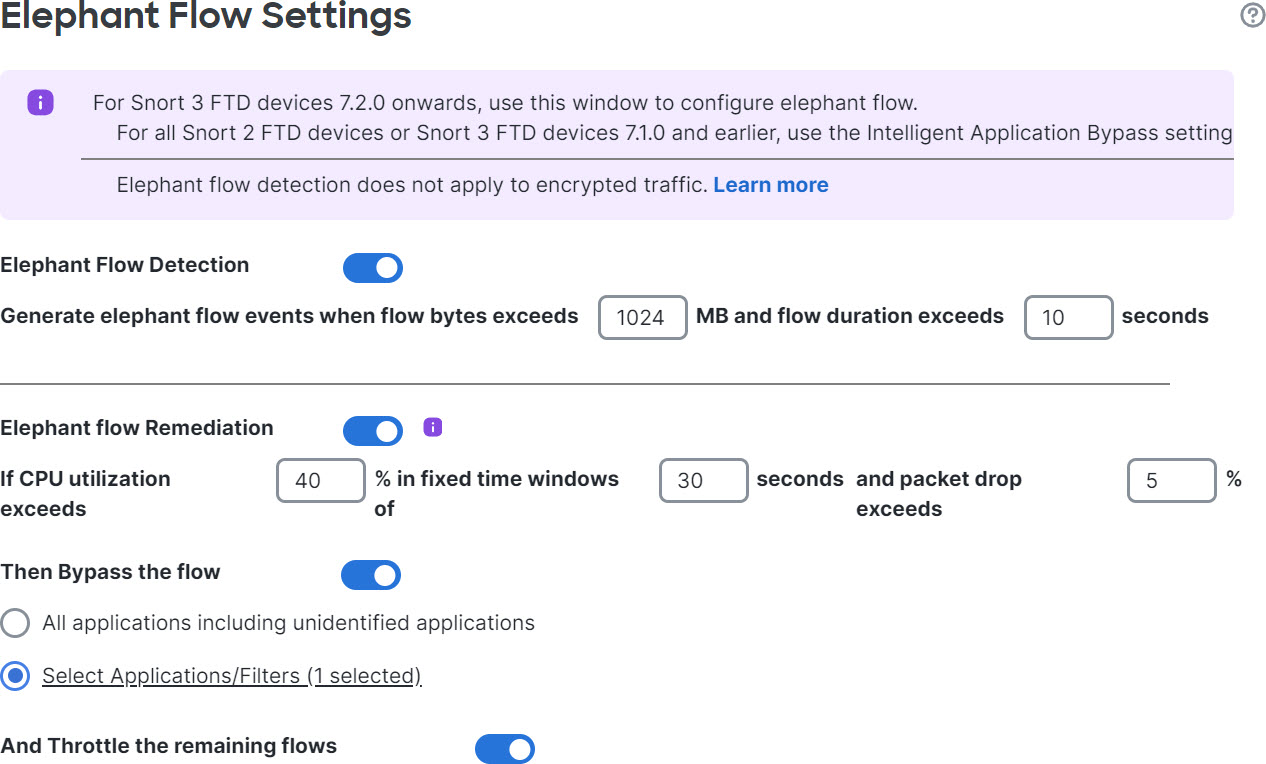
| ||
Step 2 | The Elephant Flow Detection toggle button is enabled by default. You can configure the values for flow bytes and flow duration. When they exceed your configured values, elephant flow events are generated. | ||
Step 3 | To remediate elephant flows, enable the Elephant Flow Remediation toggle button. | ||
Step 4 | To set the criteria for remediation of the elephant flow, configure the values for CPU utilization %, duration of fixed time windows, and packet drop %. CPU utilization is calculated per elephant flow and is derived from the flow latency. If the CPU utilization crosses the configured threshold and other configurations, such as fixed time windows and packet drops, are also matched, the elephant flow remediation actions are applied. Similarly, packet drop calculation is based on the packets dropped per CPU. After the packet drop percentage exceeds the configured value on a specific CPU, the remediation actions are applied. For example, consider that configurations are set to the default, that is, CPU utilization of 40%, fixed time window of 30 seconds, and packet drop of 5%. On a specific CPU, if more than 5% of packet drops are detected and the CPU utilization per flow exceeds 40% in the fixed time frame of 30 seconds, then the flows are either bypassed or throttled. | ||
Step 5 | You can perform the following actions for elephant flow remediation when it meets the configured criteria:
| ||
Step 6 | In the Remediation Exemption Rule section, click Add Rule to configure L4 access control list (ACL) rules for flows that must be exempted from remediation. | ||
Step 7 | In the Add Rule window, use the Networks tab to add the network details, that is the source network and the destination network. Use the Ports tab to add the source port and the destination port. If an elephant flow is detected and it matches the rules that are defined, an event is generated with the reason as Elephant Flow Exempted in the Reason column header of Connection Events. | ||
Step 8 | In the Remediation Exemption Rule section, you can view the flows that are exempt from the remediation action. | ||
Step 9 | Click OK to save the elephant flow settings. | ||
Step 10 | Click Save to save the policy. |
What to do next
Deploy configuration changes.
After configuring your elephant flow settings, monitor your connection events to see if any flows are detected, bypassed, or throttled. You can view this in the Reason field of your connection event. The three reasons for elephant flow connections are:
-
Elephant Flow
-
Elephant Flow Throttled
-
Elephant Flow Trusted
Attention | Enabling elephant flow detection alone does not cause generation of connection events for elephant flows. If a connection event is already logged for another reason and the flow is also an elephant flow, then the Reason field contains this information. However, to ensure that you are logging all elephant flows, you must enable connection logging in the applicable access control rules. |
