Example: Decryption Rule to Monitor or Block Certificate Status
The last decryption rules, because they are the most specific and require the most processing, are rules that either monitor or block bad certificates and unsecure protocol versions. The example in this section shows how to monitor or block traffic by certificate status.
Important | Use the Cipher Suite and Version rule conditions only in rules with either the Block or Block with reset rule actions. Do not use Cipher Suite and Version with Decrypt - Resign or Decrypt - Known Key rule actions. These conditions in rules with other rule actions can interfere with the system's ClientHello processing, resulting in unpredictable performance. |
Procedure
Step 1 | Log in to the Secure Firewall Management Center if you haven't already done so. |
Step 2 | Click . |
Step 3 | Click Edit ( |
Step 4 | Click Edit ( |
Step 5 | Click Add Rule. |
Step 6 | n the Add Rule dialog box, in the Name field, enter a name for the rule. |
Step 7 | Click Cert Status. |
Step 8 | For each certificate status, you have the following options:
|
Step 9 | From the Action list, click either Monitor to only monitor and log traffic that matches the rule or click Block or Block with Reset to block the traffic and optionally reset the connection. |
Step 10 | To save changes to the rule, at the bottom of the page, click Add. |
Step 11 | To save changes to the policy, at the top of the page, click Save. |
Example
The organization trusts the Verified Authority certificate authority. The organization does not trust the Spammer Authority certificate authority. The system administrator uploads the Verified Authority certificate and an intermediate CA certificate issued by Verified Authority to the system. Because Verified Authority revoked a certificate it previously issued, the system administrator uploads the CRL that Verified Authority provided.
The following figure shows a certificate status rule condition checking for valid certificates, those issued by a Verified Authority, are not on the CRL, and still within the Valid From and Valid To date. Because of the configuration, traffic encrypted with these certificates is not decrypted and inspected with access control.
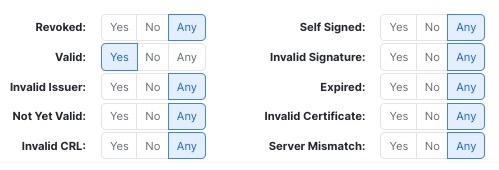
The following figure shows a certificate status rule condition checking for the absence of a status. In this case, because of the configuration, it matches against traffic encrypted with a certificate that has not expired.

In the following example, traffic would match this rule condition if the incoming traffic is using a certificate that has an invalid issuer, is self-signed, expired, and it is an invalid certificate.
The following graphic illustrates a certificate status rule condition that matches if the SNI of the request matches the server name or if the CRL is not valid.

