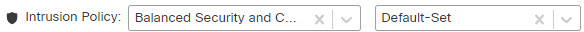How to Block Threats
You can implement next generation Intrusion Prevention System (IPS) filtering by adding intrusion policies to your access control rules. Intrusion policies analyze network traffic, comparing the traffic contents against known threats. If a connection matches a threat you are monitoring, the system drops the connection, thus preventing the attack.
All other traffic handling occurs before network traffic is examined for intrusions. By associating an intrusion policy with an access control rule, you are telling the system that before it passes traffic that matches the access control rule's conditions, you first want to inspect the traffic with an intrusion policy.
You can configure intrusion policies on rules that allow traffic only. Inspection is not performed on rules set to trust or block traffic. In addition, you can configure an intrusion policy as the default action if you do not want to use a simple block.
Besides inspecting traffic that you allow for potential intrusions, you can use the Security Intelligence policy to preemptively block all traffic to or from known bad IP addresses, or to known bad URLs.
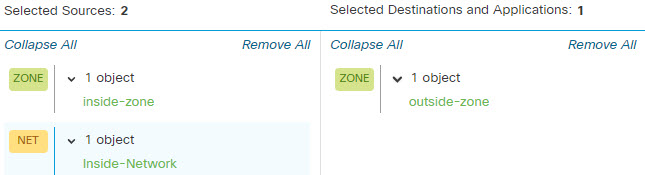
This example adds an intrusion policy that allows the internal 192.168.1.0/24 network to got outside, and assumes you already have block rules to selectively eliminate unwanted connections, while also adding a Security Intelligence policy to do pre-emptive blocking.
Before you begin
You must apply the IPS license to any managed device that uses this rule.
This example assumes you have already created security zones for inside and outside interfaces, and the network object for the inside network.
Procedure
Step 1 | Create the access control rule that applies the intrusion policy. |
Step 2 | Configure the Security Intelligence policy to preemptively drop connections with known bad hosts and sites. By using Security Intelligence to block connections with hosts or sites that are known to be threats, you save your system the time needed to do deep packet inspection to identify threats in each connection. Security Intelligence provides an early block of undesirable traffic, leaving more system time to handle the traffic you really care about. |
Step 3 | Deploy your changes. |