Convert Snort 2 Rules of a Single Intrusion Policy to Snort 3
Procedure
Step 1 | Choose . | ||
Step 2 | In the Intrusion Policies tab, click Show Snort 3 Sync status. 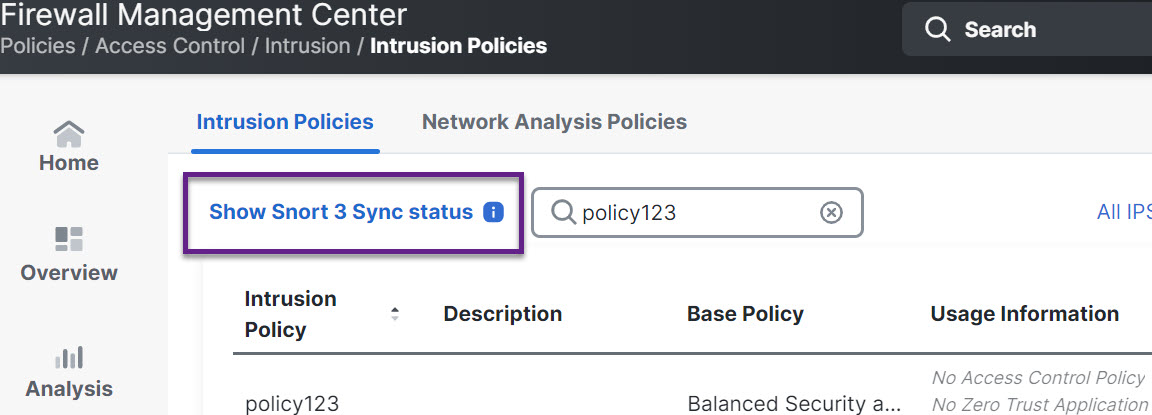
If your policy displays an orange arrow, it indicates that the Snort 2 and the Snort 3 versions of the intrusion policy are not synchronized. 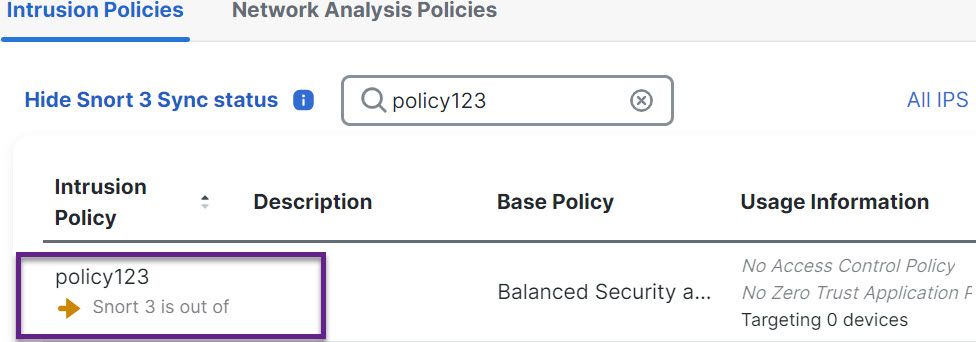
| ||
Step 3 | Click the orange arrow. The Snort 2 to Snort 3 Sync Summary page displays that the Snort 2 to Snort 3 sync is pending. 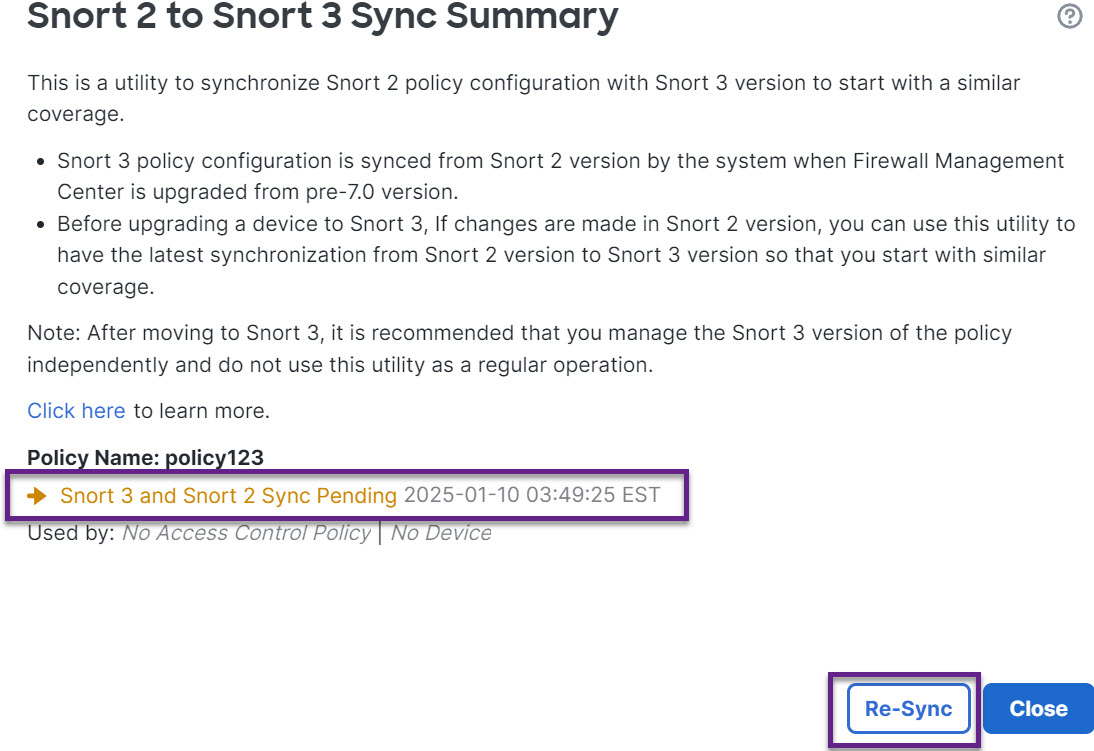
| ||
Step 4 | Click Re-Sync to start the synchronization.
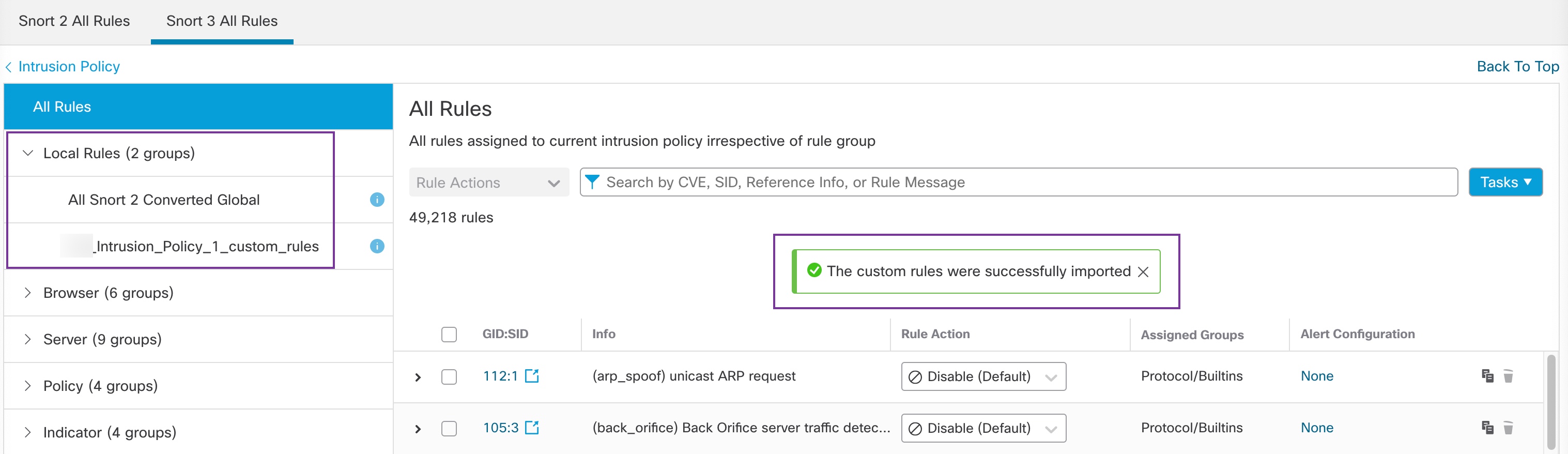
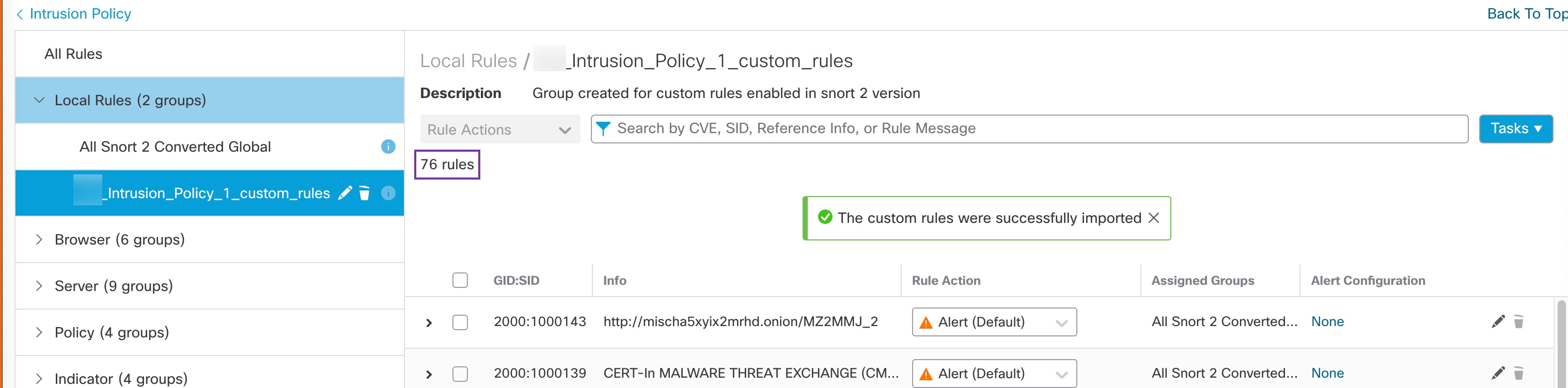
The Summary Details section lists the rules that were migrated or skipped. In our use case, there are 76 custom Snort 2 rules, 17 rules with thresholds, and 15 rules with suppression that were skipped during the sync process. To migrate the custom rules, go to the next step. 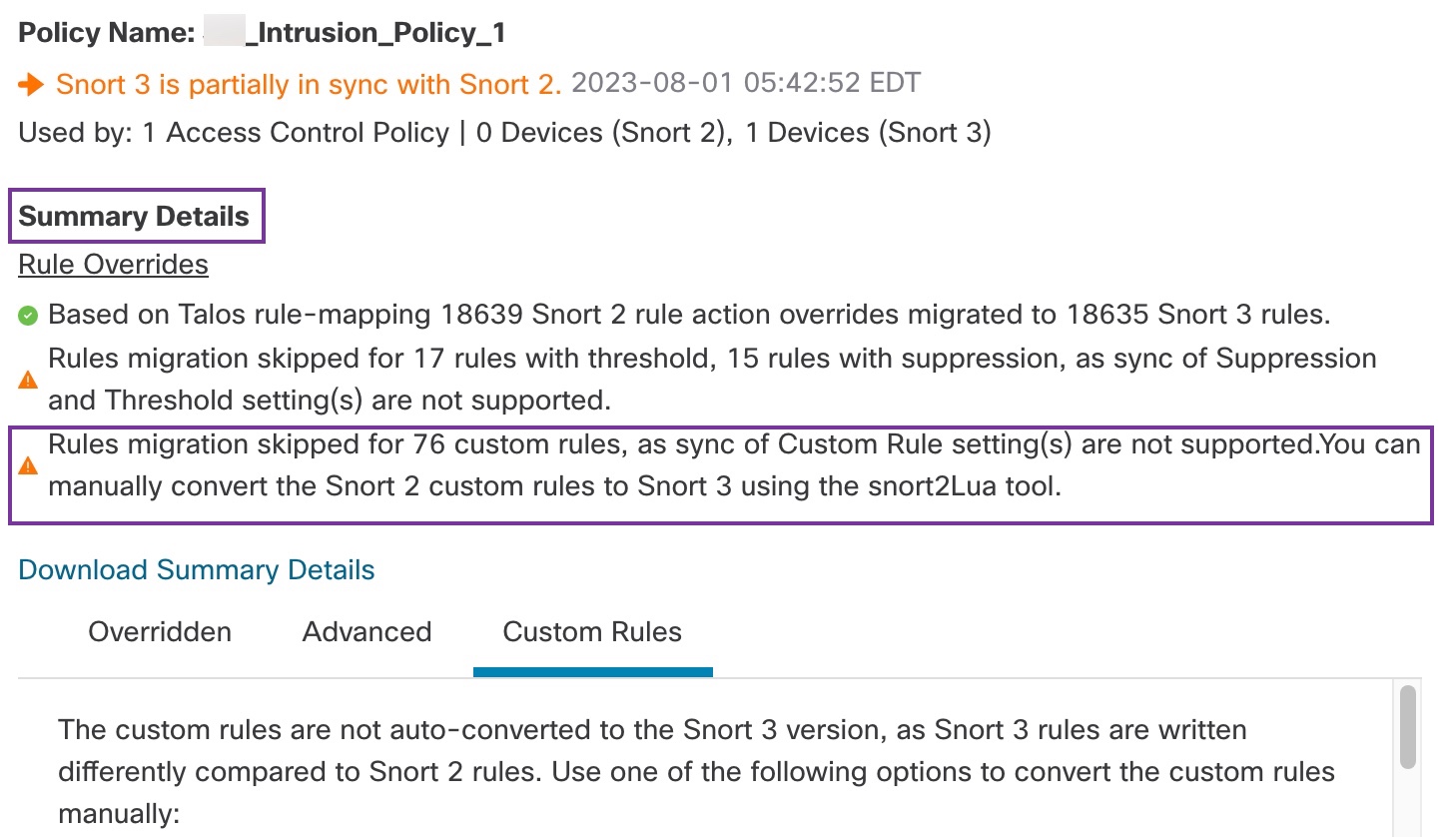
To migrate rules with thresholds and suppressions, go to Step 6. 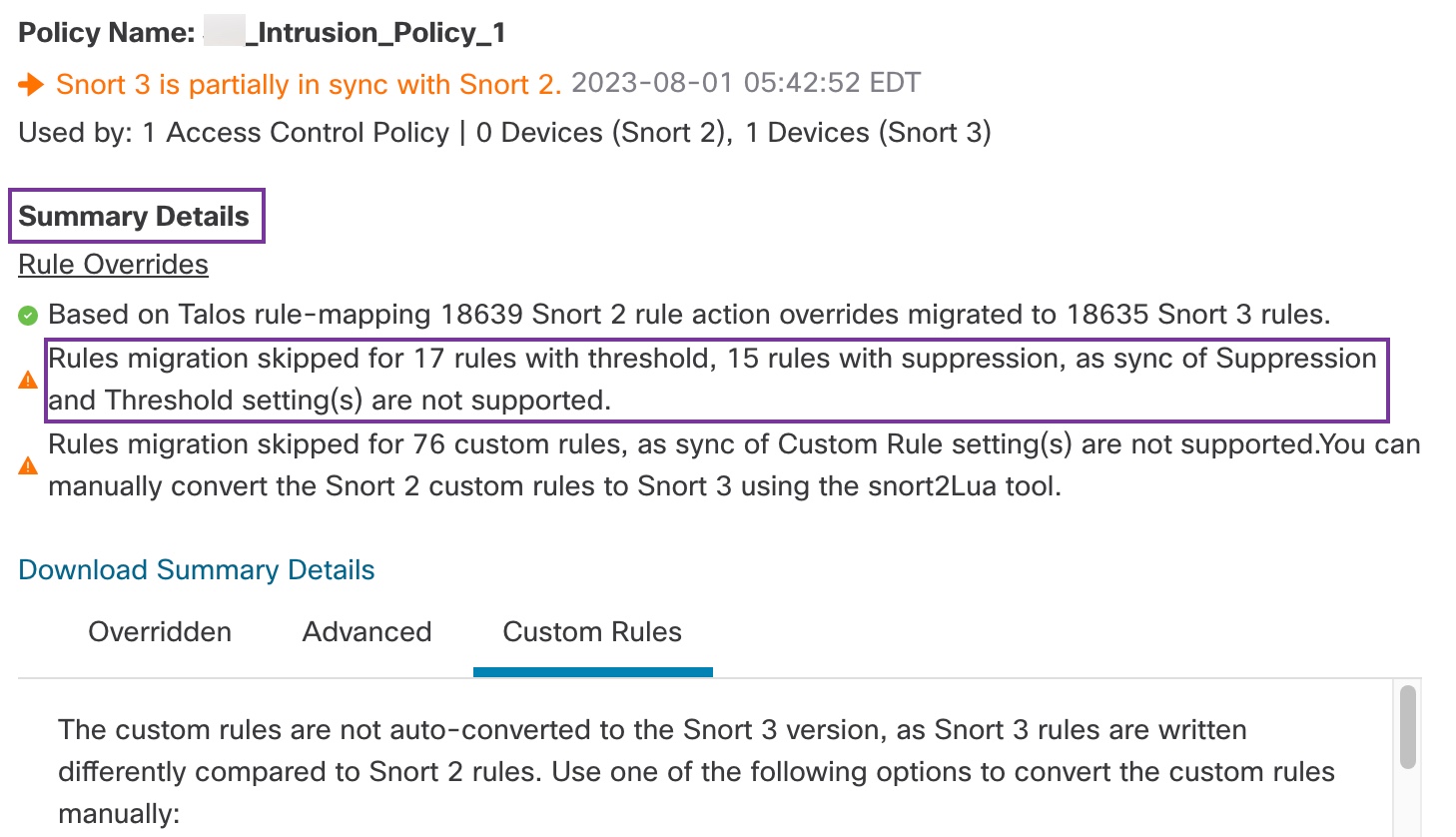
| ||
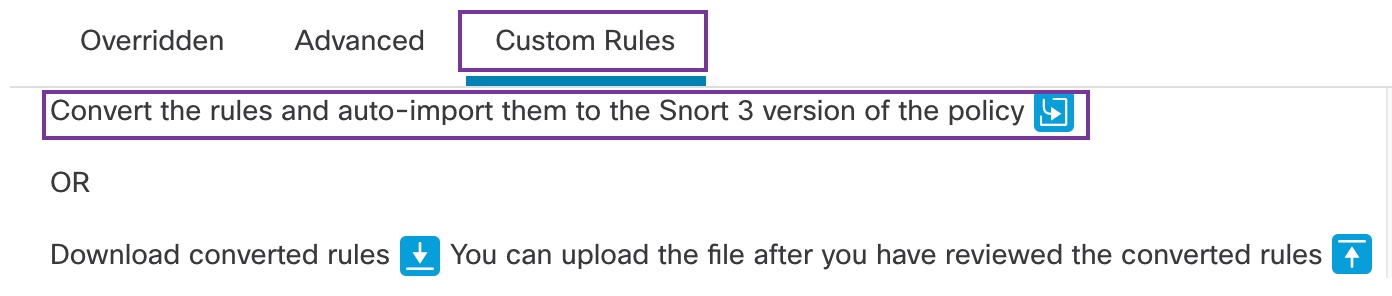
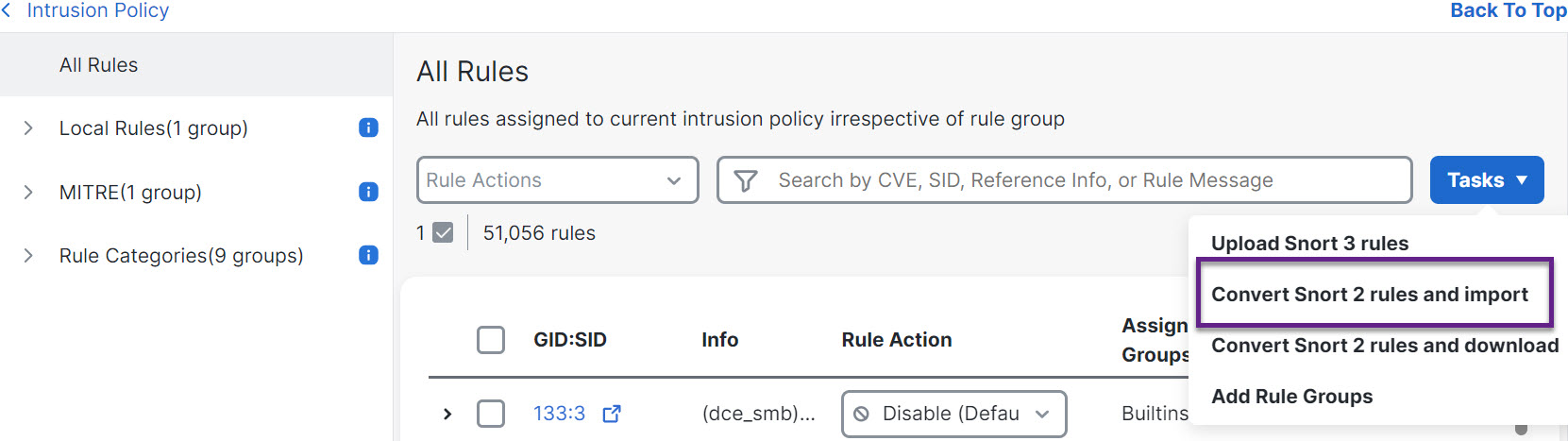
Step 5 | To migrate the 76 custom rules, perform either one of these steps:
| ||
Step 6 | Click the Download Summary Details link to download the rules in .txt format. The following is a sample of the summary that is displayed. | ||
Step 7 | Click Close to close the Sync Summary dialog box. | ||
Step 8 | To check the rules with status: ERROR, choose and click the Snort 2 version of the intrusion policy. | ||
Step 9 | Under Policy Information, click Rules and filter for the rule. For example, enter PSNG_TCP_PORTSCAN in the Filterfield to find the rule. | ||
Step 10 | Click Show Details to view the detailed version of the rule. | ||
Step 11 | Create the rule again in Snort 3 using Snort 3 rule guidelines and save the file as a .txt or .rules file. For more information, see www.snort3.org. | ||
Step 12 | Upload the custom rule that you just created locally to the list of all the Snort 3 rules. See Add Custom Rules to Rule Groups. |
What to do next
Deploy configuration changes. See Deploy Configuration Changes.