Resolve Issues with Shadowed Rules
This is how Security Cloud Control displays the rules described in the "example" network policy above:
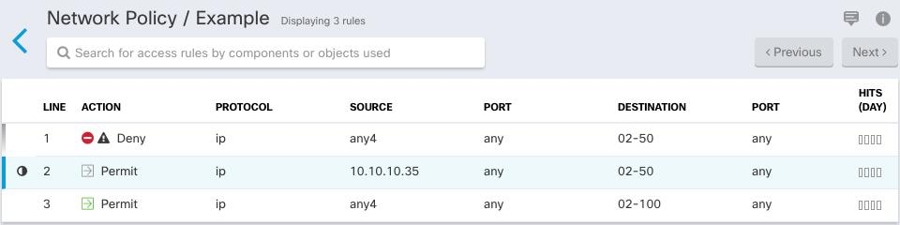
The rule on line 1 is marked with a shadow warning badge  because it's shadowing another rule in the policy. The rule on line 2 is marked as being shadowed
because it's shadowing another rule in the policy. The rule on line 2 is marked as being shadowed  by another rule in the policy. The action for the rule on line 2 is grayed-out because it's entirely shadowed by another rule in the policy. Security Cloud Control is able to tell you which rule in the policy shadows the rule in line 2.
by another rule in the policy. The action for the rule on line 2 is grayed-out because it's entirely shadowed by another rule in the policy. Security Cloud Control is able to tell you which rule in the policy shadows the rule in line 2.
The rule on line 3 can only be triggered some of the time. This is a partially shadowed rule. Network traffic from any IPv4 address trying to reach an IP address in the range 10.10.10.2-10.10.10.50 would never be evaluated because it would have already been denied by the first rule. However, any IPv4 address attempting to reach an address in the range 10.10.10.51-10.10.10.100 would be evaluated by the last rule and would be permitted.
Caution | Security Cloud Control does not apply a shadow warning badge |
Procedure
Step 1 | Select the shadowed rule in the policy. In the example above, that means clicking on line 2. | ||
Step 2 | In the rule details pane, look for the Shadowed By area. In this example, the Shadowed By area for the rule in line 2 shows that it is being shadowed by the rule in line 1: 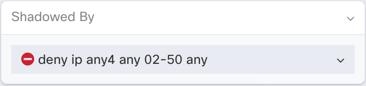
| ||
Step 3 | Review the shadowing rule. Is it too broad? Review the shadowed rule. Do you really need it? Edit the shadowing rule or delete the shadowed rule.
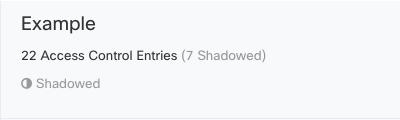
Security Cloud Control also displays the number of ACEs derived from a single rule in a network policy and displays that information in the network policy details pane. Here is an example of that listing: 
| ||
Step 4 | Determine which devices use the policy by looking in the Devices area of the network policy details pane. | ||
Step 5 | Open the Security Devices page and Deploy Changes back to the devices affected by the policy change. |