Objects Associated with Meraki Devices
About Objects Used with Meraki Devices
The Meraki dashboard utilizes groups of IP addresses, protocols, or port ranges in source and destination fields in outbound access control rules. Once onboarded, Security Cloud Control translates IP address into network objects, and application layer protocol values into either service objects or protocol objects.
A single rule in Security Cloud Control can translate into multiple rules in the dashboard. For example, if you add an ASA protocol group that includes both TCP and UDP protocols to a single access control rule in Security Cloud Control, Security Cloud Control translates the one Security Cloud Control rule into multiple rules in the dashboard: one rule containing a TCP protocol and one rule containing a UDP protocol.
Note that the Meraki dashboard and Security Cloud Control both support CIDR subnet notation. For more information on layer 3 switch interfaces and MX device layout, see the Meraki Knowledge Base.
Which Objects Can You Use With a Meraki Device in Security Cloud Control?
There are no objects in Security Cloud Control that are exclusive to MX devices. Instead, you can create or share FTD, FDM, and ASA objects and associate these objects in rules that are deployed to the device. Because Meraki is not fully compatible with FTD and ASA objects, there may be a few limitations that affect how the MX device uses objects.
Note that if you associate an FTD, FDM, and ASA objects with an MX device, that object becomes shared. Any changes to that object will affect all the devices it is shared with and the devices' configuration status will appear as Not Synced. See Shared Objects for more information. For additional object states that could affect your objects, see the Related Articles section listed at the bottom of this page.
Meraki does not support objects containing IPv6 addresses or FQDNs.
|
Object in Security Cloud Control |
Compatible with Meraki |
|---|---|
|
Protocol Objects |
TCP, UDP, ICMP |
|
Network Objects |
yes |
|
Network Groups |
yes |
|
Service Objects |
yes |
|
ASA Service Groups |
no |
|
FTD Service Groups |
no |
Local Network Objects and Object Groups From the Meraki Cloud
Network objects and object groups provide easier management of firewall rules for Meraki devices. They serve as labels to IP Subnets and FQDN that can be used on access policies such as firewall rules. If there are needs to modify multiple access policies that use the same IP Subnets or FQDN, you only need to modify the network object to have it reflect on all policies. At this time, you must use the Meraki dashboard to create and modify these objects. For more information about what these objects can do for your environment, see Meraki's Network Objects Highlights.
Note | Once a device configuration referencing a Meraki network object or network object group is onboarded or synchronized to the Security Cloud Control UI, these objects are displayed as FTD Network objects. These objects and object groups are read-only in Security Cloud Control. |
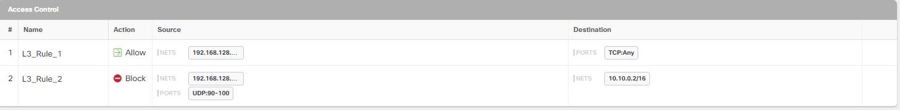
What Do Meraki Rules Look Like in Security Cloud Control
You can view the objects from the device's policy page, or you can filter the objects page based on device. From the policy page you can view, edit, and reorder the access control rules. Because Security Cloud Control translates the outbound rules from the Meraki dashboard into access control rules with objects, rules and protocols from the Meraki dashboard may look different. The following table addresses the new names for protocols once the device is onboarded to Security Cloud Control:
|
Rule or Protocol Header in the Meraki dashboard |
Rule or Object Header in Security Cloud Control |
|---|---|
|
Policy |
Action |
|
Source IP |
Network Object or Network Group |
|
Destination IP |
Network Object or Network Group |
|
Source Port |
Network Object or Network Group |
|
Destination Port |
Network Object or Network Group |
|
Layer 3 Application Protocol |
Ports (Protocol Groups, Port Groups, or Service Objects) |
The following is an example of what the outbound rules from the Meraki dashboard look in Security Cloud Control: