End-to-End Process for Deploying Threat Defense Virtual Cluster on AWS
Template-based Deployment
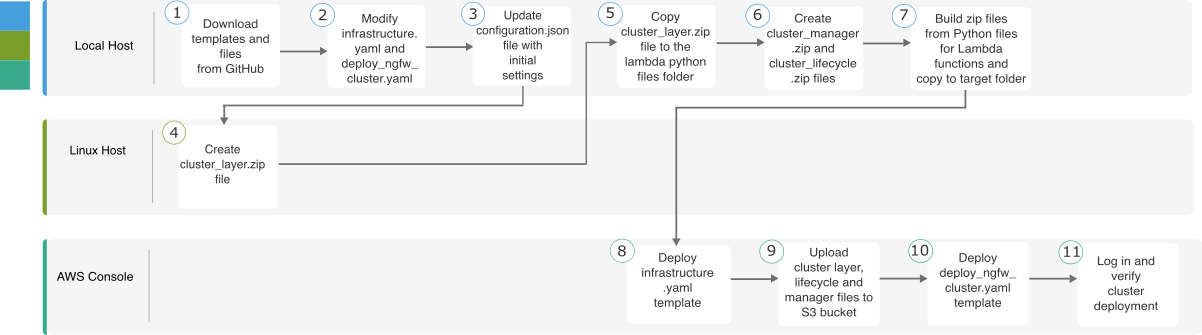
The following flowchart illustrates the workflow for template-based deployment of the Threat Defense Virtual cluster on AWS.
Manual Deployment
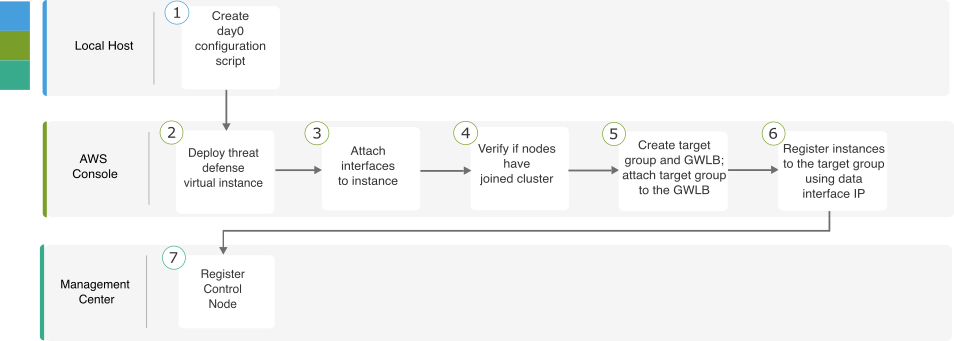
The following flowchart illustrates the workflow for manual deployment of the Threat Defense Virtual cluster on AWS.
|
Workspace |
Steps |
|
|---|---|---|
| Local Host | Create day 0 configuration script. | |
| AWS Console | Deploy Threat Defense Virtual instance. | |
| AWS Console | Attach interfaces to instance. | |
| AWS Console | Verify if nodes have joined cluster. | |
| AWS Console | Create target group and GWLB; attach target group to the GWLB. | |
| AWS Console | Register instances with the target group using data interface IP. | |
| Management Center | Register control node. |