Clientless Zero Trust Network Access Workflow
This figure depicts the Zero Trust Access workflow.
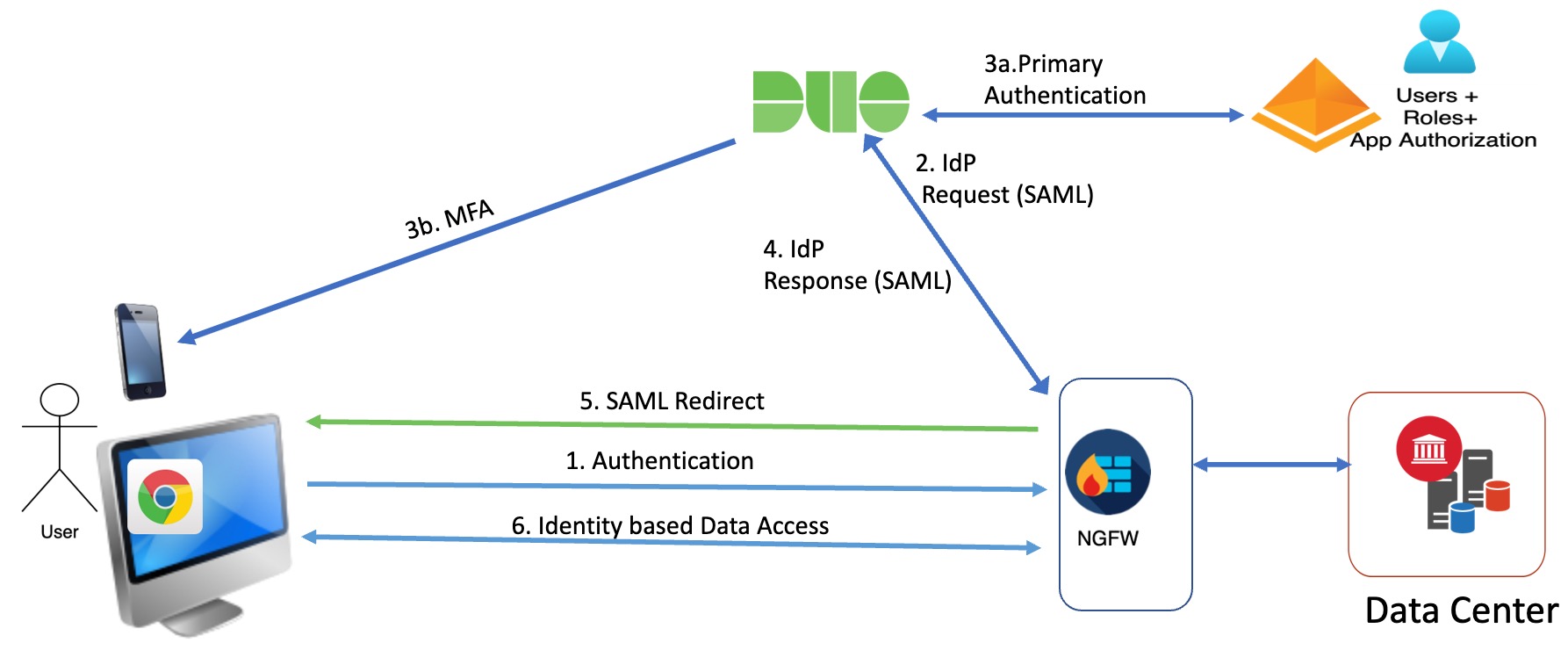
The workflow is as follows:
-
User types the application URL in the browser.
-
If the HTTPS request is valid, the user is redirected to the mapped port (Step 6).
-
If the HTTPS request is invalid, the user is sent for authentication per application (Step 2).
-
-
The user is redirected to the configured identity provider (IdP).
-
-
The user is redirected to the configured primary authentication source.
-
The user is challenged with the configured secondary multi-factor authentication, if any.
-
-
The IdP sends a SAML response to threat defense. The user ID and other necessary parameters are retrieved from the SAML response through the browser.
-
The user is redirected to the application.
-
The user is allowed access to the application after validation is successful.