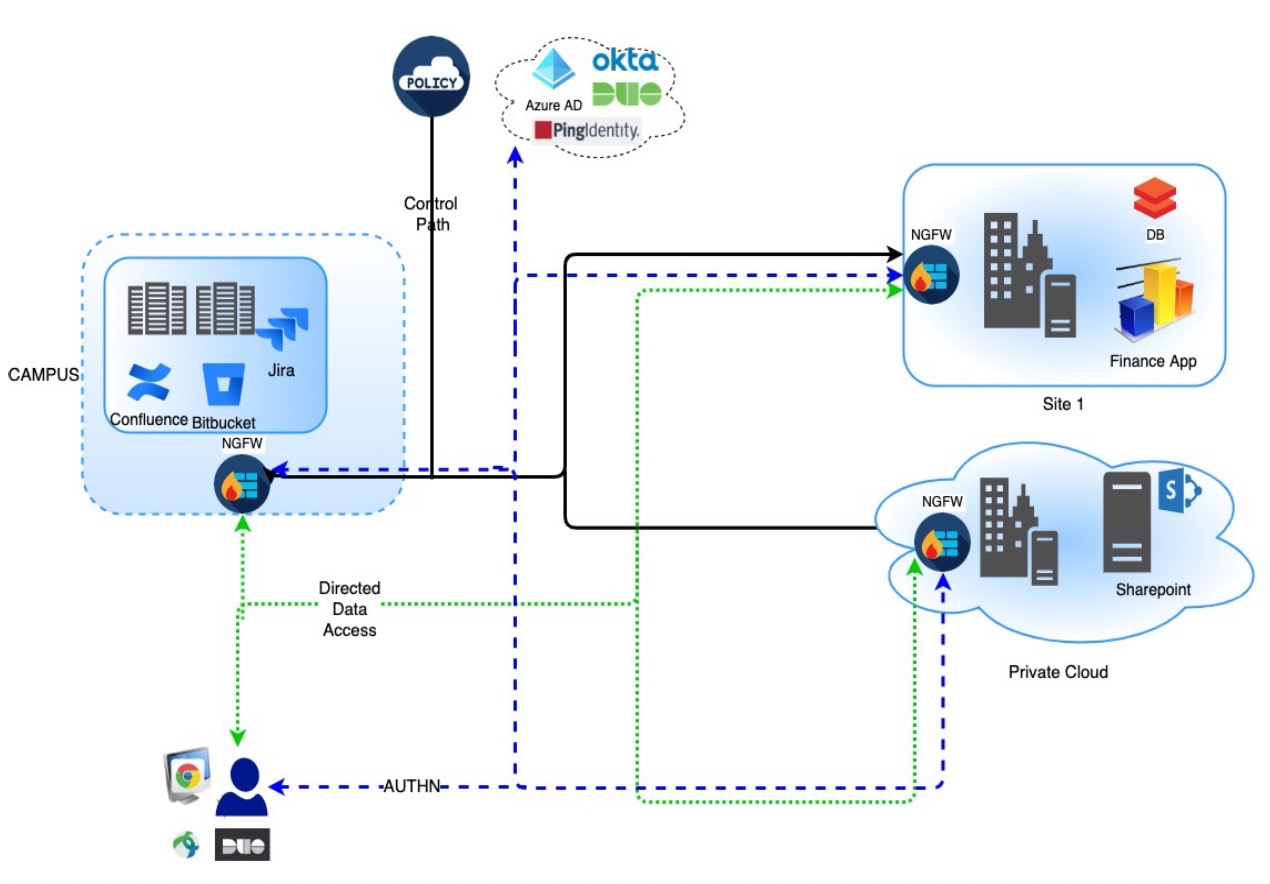
How Threat Defense Works with Zero Trust Access
-
Using a browser, a remote or on-prem user sends a HTTPS request to connect to an application from an endpoint.
-
The HTTPS request is intercepted by the firewall that protects the application.
-
The firewall redirects the user to application’s configured IdP for authentication.
NoteIn the figure, each firewall protects a set of web applications. The user can directly access the applications behind the firewall after authentication and authorization.
-
After the authentication and authorization process is complete, the firewall allows the user to access the application.