Limitations for Clientless Zero Trust Network Access
-
Supports only TLS-enabled web applications. All traffic must be decrypted.
-
Supports only SAML identity providers.
-
IPv6 is not supported.
NAT66, NAT64, and NAT46 scenarios are not supported.
-
Supports IPv6; however, you can use only homogeneous network address translations (NAT) scenarios such as NAT66 and NAT44.
NAT64, and NAT46 scenarios are not supported.
-
Clientless zero trust network access is available on Firewall Threat Defense only if Snort 3 is enabled.
-
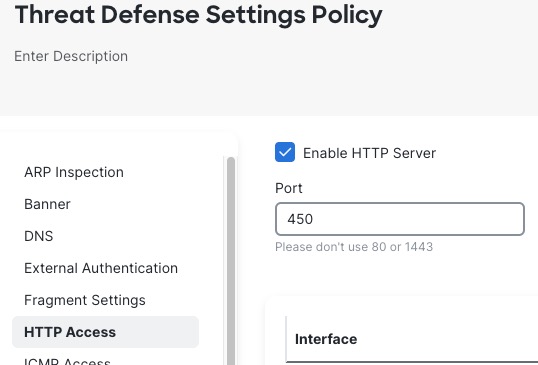
By default, the Firewall Threat Defense device uses port 443 for secure communications. Because this is the same port used by TLS-enabled applications likely to be configured for zero trust network access, you must change the device's HTTP server port.
Go to , then edit the Threat Defense Settings policy for the device, click HTTP Access, select the Enable HTTP Server check box, and enter a port other than 443 in the field. When you're finished, click Save in the upper right corner of the page.
The following figure shows an example.
-
All hyperlinks in protected web applications must have a relative path and are not supported on individual mode clusters.
-
Protected web applications running on a virtual host or behind internal load balancers must use the same external and internal URL.
-
Not supported on applications with strict HTTP Host Header validation enabled.
-
If the application server hosts multiple applications and serves content based on the Server Name Indication (SNI) header in the TLS Client Hello, the external URL of the zero trust application configuration must match the SNI of that specific application.