Passive identity agent primary/secondary agent deployments
To provide redundancy and to avoid a single point of failure, you can configure primary and secondary passive identity agents in any of the ways shown in this topic.
You can install a passive identity agent on the AD domain controller, directory server, or on any client connected to the domain you wish to monitor.
Single AD domain controller with primary and secondary agents
The following figure shows how to set up primary and secondary passive identity agents on one AD domain controller. If the primary agent fails, the secondary takes over.
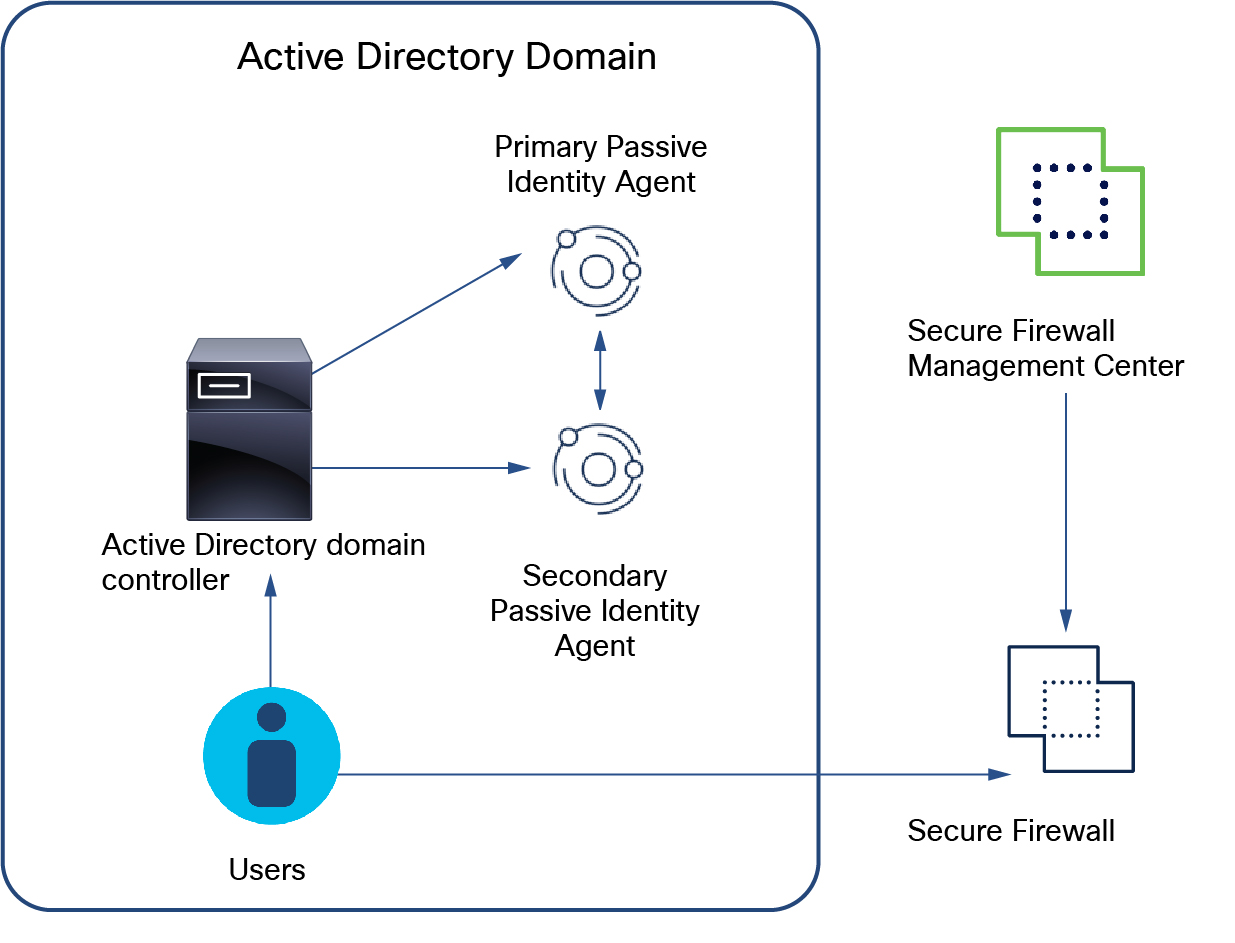
To set this up:
-
Create a Microsoft AD realm that has one directory for the domain controller.
See Create an LDAP realm or an Active Directory realm and realm directory.
-
Install the passive identity agent software on any two network machines connected to the domain controller.
Configure each passive identity agent individually to communicate with the Cloud-Delivered Firewall Management Center on which you configure the passive identity agent source.
-
Create the identity source.
See Create a primary or secondary passive identity agent identity source.
Multiple AD domain controllers, primary and secondary agents
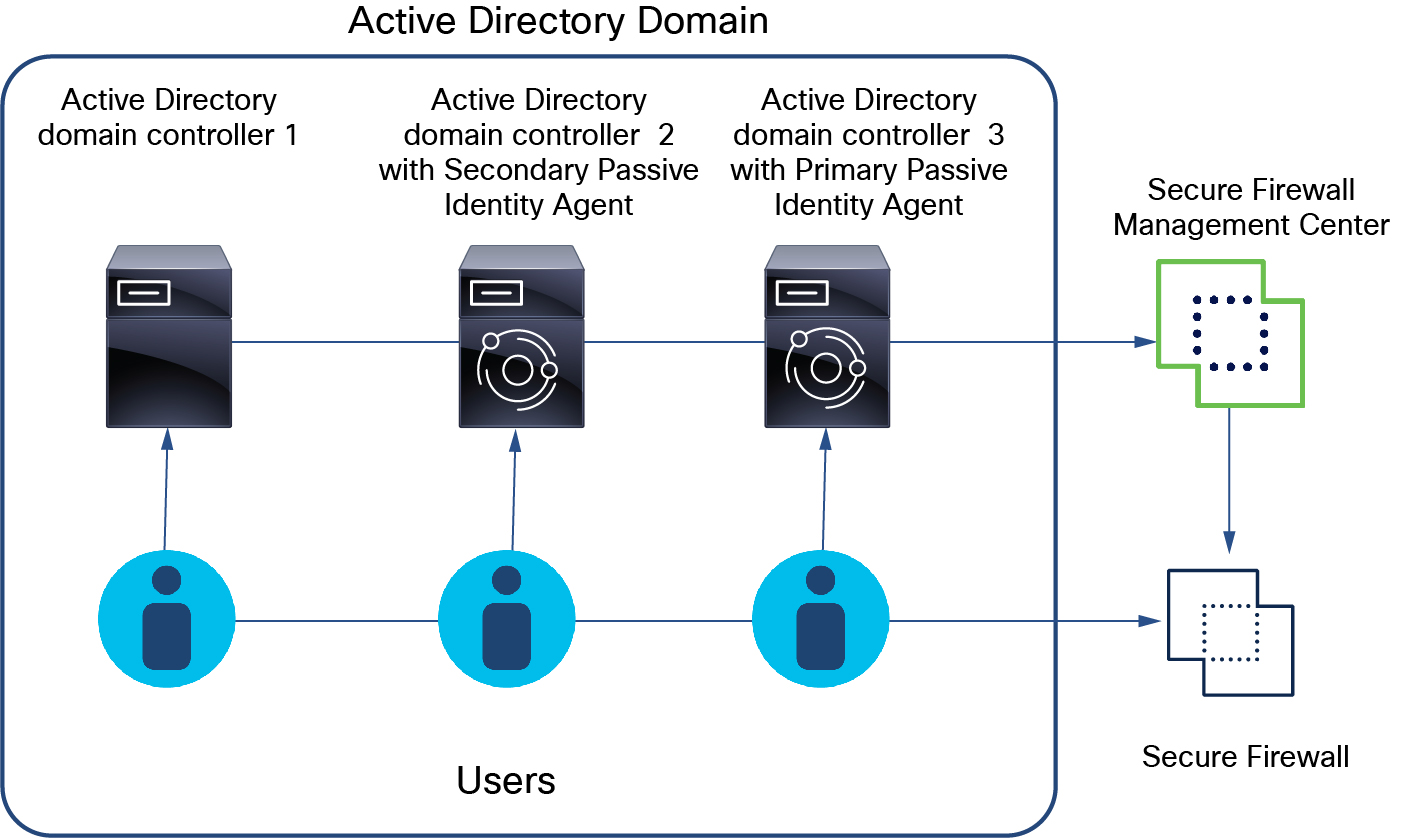
The preceding figure shows how to configure primary and secondary agents to monitor three AD domain controllers. If the primary agent fails, the secondary agent takes over.
To set this up:
-
Create a Microsoft AD realm that has one directory for the domain controller.
See Create an LDAP realm or an Active Directory realm and realm directory.
-
Install the passive identity agent software on any machine connected to the domain controller.
Configure each passive identity agent individually to communicate with the Cloud-Delivered Firewall Management Center on which you configure the passive identity agent source.
-
Create the identity source.
See Create a primary or secondary passive identity agent identity source.