How the pxGrid Cloud identity source works
The following figure shows how the identity source works.
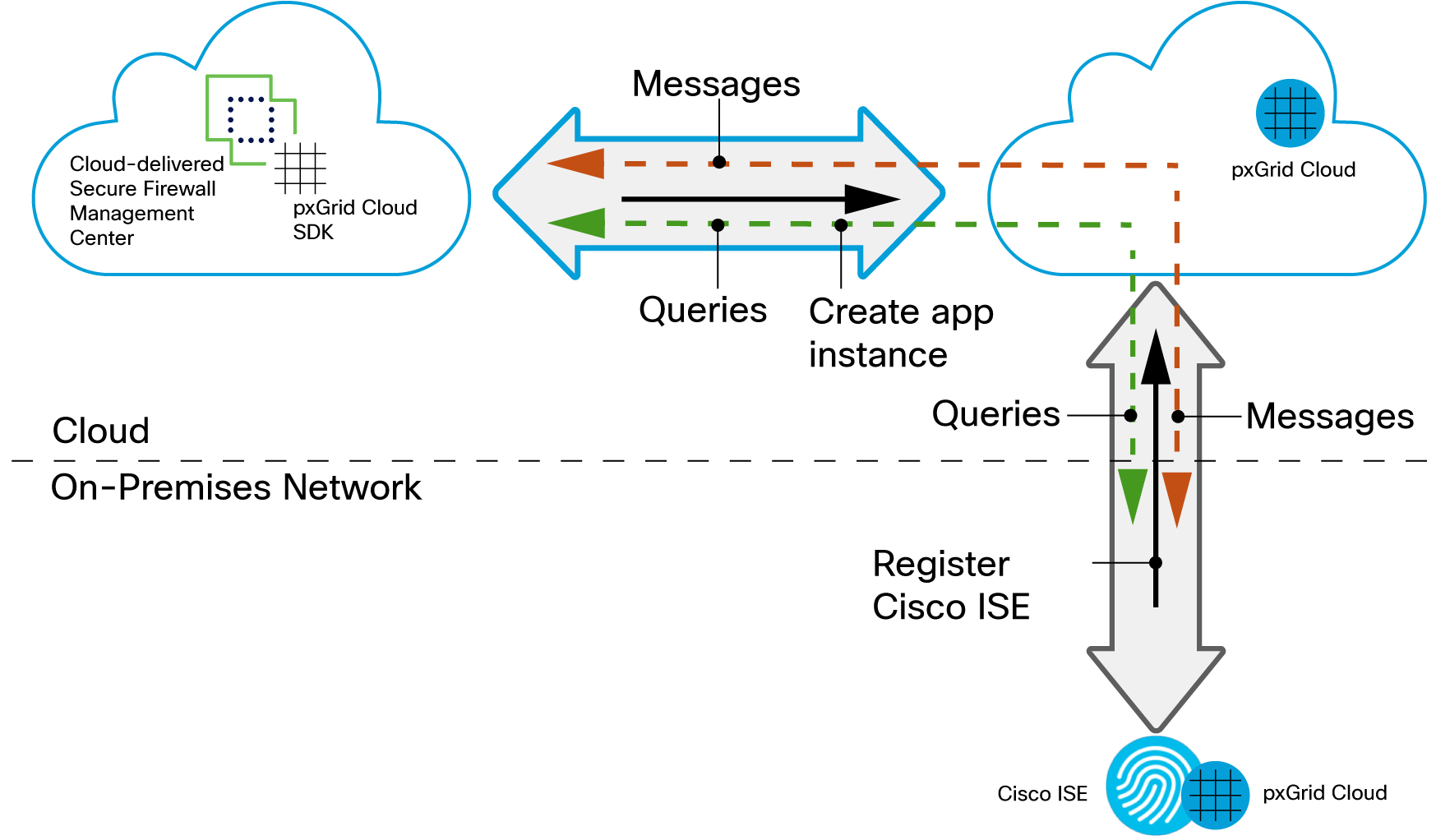
Your Cloud-Delivered Firewall Management Center uses the pxGrid Cloud SDK to programmatically retrieve user information from an on-premises Cisco ISE server so these users can be used in identity policies on the Cloud-Delivered Firewall Management Center.
To authorize and authenticate this data exchange, you must:
-
In Cisco ISE, enable the use of pxGrid Cloud.
-
Register Cisco ISE as a product in pxGrid Cloud, which authenticates Cisco ISE and pxGrid Cloud and enables them to communicate with each other.
The authentication process requires you to paste a one-time password (OTP) from pxGrid Cloud into Cisco ISE.
-
In pxGrid Cloud, create an "app instance" that generates an OTP for you to use in the Cloud-Delivered Firewall Management Center to authenticate the two with each other.
-
After completing all the preceding tasks, the Cloud-Delivered Firewall Management Center (which includes the pxGrid Cloud SDK) can query Cisco ISE using pxGrid Cloud and retrieve sessions containing user information, SGT, endpoint profile, and other details.
-
Many types of dynamic objects can be filtered and sent to the Cloud-Delivered Firewall Management Center as dynamic objects to be used in access control rules. These include: SGT, endpoint profile, posture status, and machine authentication.
We retrieve user information from Cisco ISE and group information from either Microsoft Active Directory or Azure Active Directory.