How to Provide Internet Access with Overlapping Address Spaces
When using virtual routers, you can have the same network address for interfaces that reside in separate routers. However, because the IP addresses routed in these separate virtual routers are the same, apply NAT/PAT rules for each interface with separate NAT/PAT pools to ensure that return traffic goes to the correct destination. This example provides the procedure to configure the virtual routers and NAT/PAT rules to manage the overlapping address spaces.
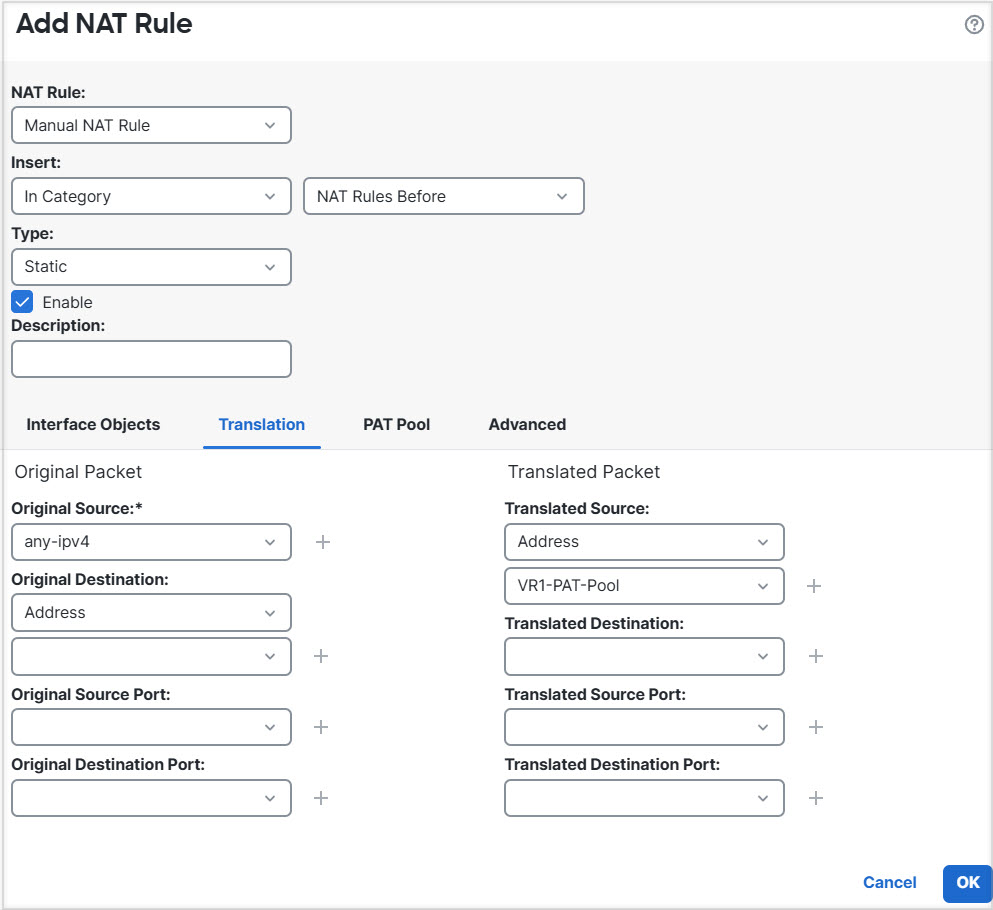
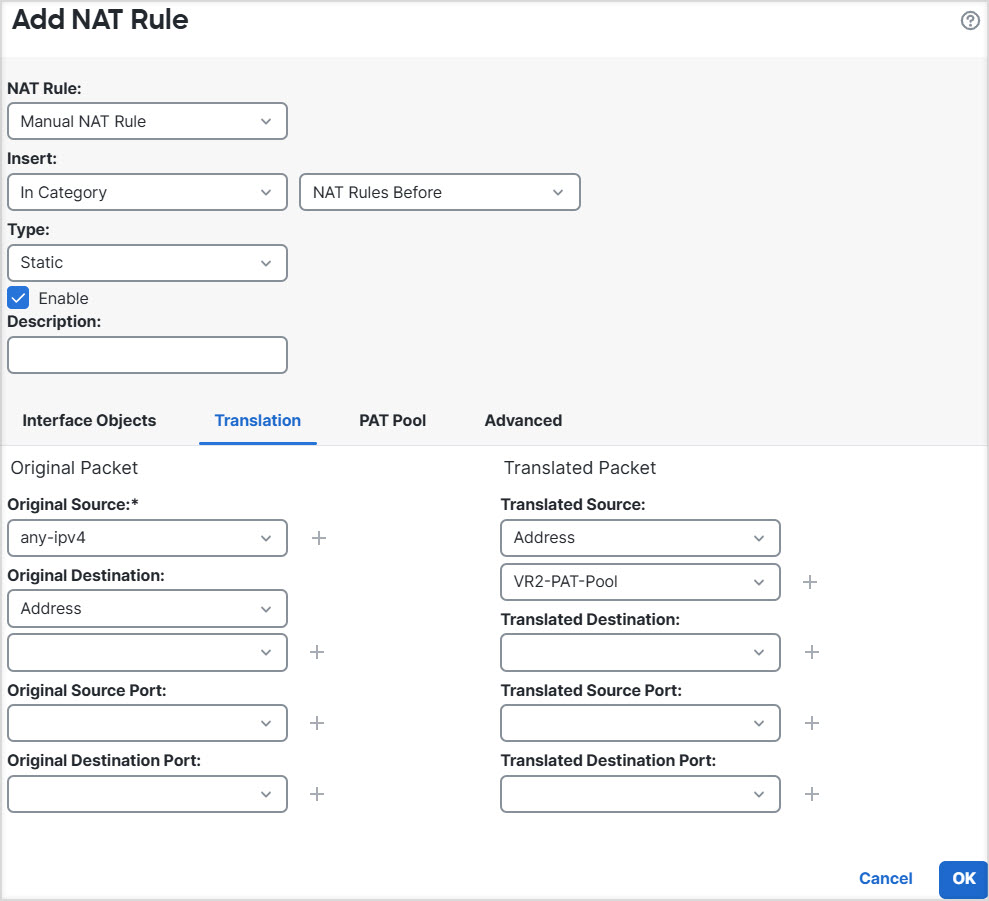
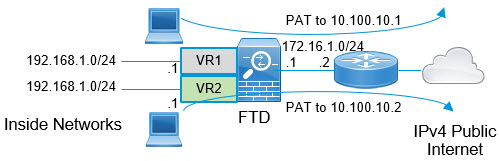
For example, interfaces vr1-inside and vr2-inside on Firewall Threat Defense is defined to use the IP address 192.168.1.1/24, managing endpoints on their segment in the 192.168.1.0/24 network. To allow Internet access from two virtual routers that use the same address space, you need to apply NAT rules separately to the interfaces within each virtual router, ideally using separate NAT or PAT pools. You could use PAT to translate the source addresses in VR1 to 10.100.10.1, and for those in VR2, to 10.100.10.2. The following illustration shows this setup, where the Internet-facing outside interface is part of the global router. You must define the NAT/PAT rules with the source interface (vr1-inside and vr2-inside) explicitly selected—using “any” as the source interface makes it impossible for the system to identify the correct source because the same IP address could exist on two different interfaces.
Note | Even if you have some interfaces within virtual routers that does not use overlapping address spaces, define the NAT rule with the source interface to make troubleshooting easier, and to ensure a cleaner separation between traffic from the virtual routers that is Internet-bound. |
Procedure
Step 1 | Configure the inside interface of the device for VR1: |
Step 2 | Configure the inside interface of the device for VR2: |
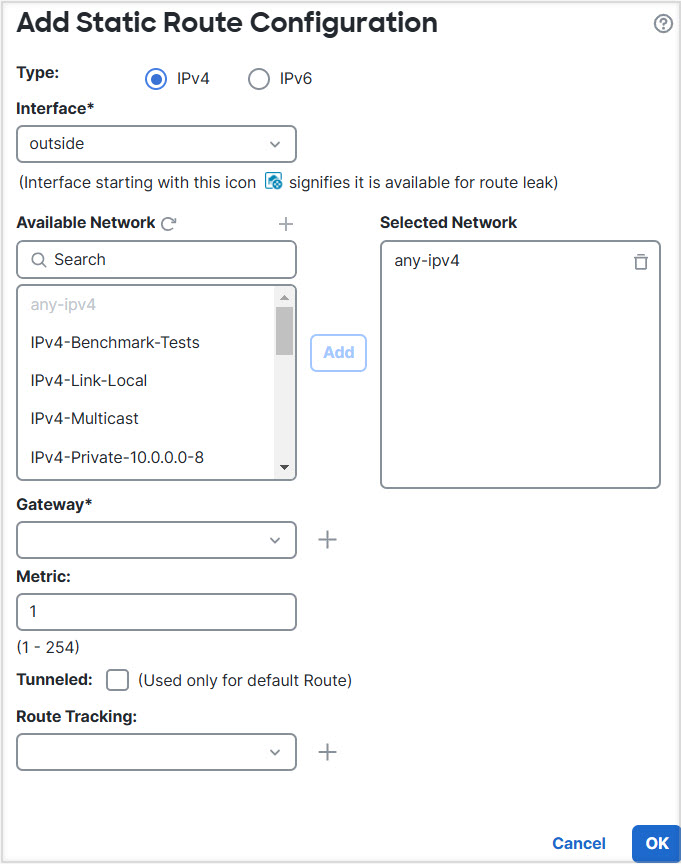
Step 3 | Configure VR1 and the static default route leak to the outside interface: |
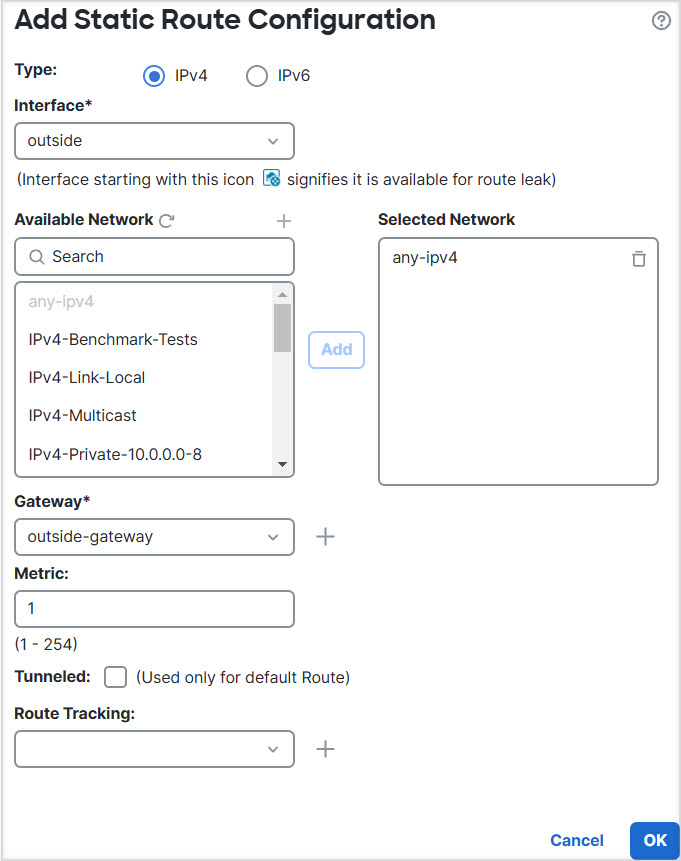
Step 4 | Configure VR2 and the static default route leak to the outside interface: |
Step 5 | Configure IPv4 static default route, namely 172.16.1.2 on the outside interface of the global router: |
Step 6 | Revisit the vr2-inside interface configuration:
|
Step 7 | Create the NAT rule to PAT inside to outside traffic of VR1 to 10.100.10.1. |
Step 8 | Add NAT rule to PAT inside to outside traffic of VR2 to 10.100.10.2. |
Step 9 | To configure the access control policy that allows traffic from the vr1-inside and vr2-inside interfaces to the outside interface, you need to create security zones. Use . Choose and create security zones for vr1-inside, vr2-inside, and outside interfaces. |
Step 10 | Choose and configure an access control rule to allow traffic from vr1-inside-zone and vr2- inside-zone to outside-zone. Assuming that you create zones named after the interfaces, a basic rule that allows all traffic to flow to the Internet will look like the following. You can apply other parameters to this access control policy: 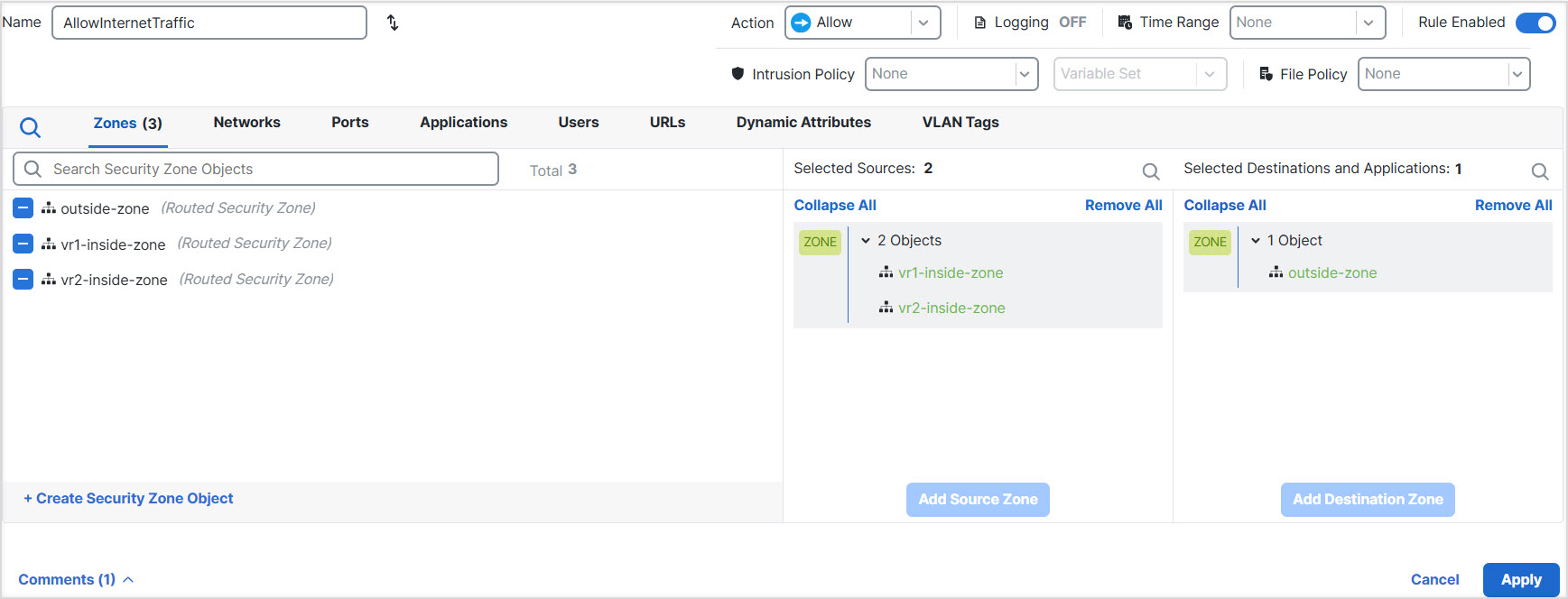 |